Gartner predicts disaster recovery will become part of the CISO’s job. This isn’t just an IT problem anymore—it’s an enterprise imperative.
Bitsight Threat Intelligence Briefing: Key Malware Trends Shaping Cyber Risk in 2025


Audio Recap
Executive summary
The cybercrime underground continues to evolve into a mature, service-based economy that mirrors legitimate technology markets. Threat actors are increasingly adopting professionalized business models, offering malware, access, and data-theft capabilities “as a service” to a broad audience of buyers.
During the first half of 2025, Bitsight observed sustained growth in Malware-as-a-Service (MaaS) and Remote Access Trojan (RAT) activity across dark web forums and marketplaces. Ransomware operators remain active, and the ecosystem surrounding stealer and loader malware continues to diversify. Emerging toolkits written in Rust, Go, and other cross-platform languages demonstrate the technical evolution of criminal development practices.
Across sectors, healthcare, technology, and finance remain among the most frequently targeted industries. Healthcare continues to rank as the most impacted sector, with 93% of U.S. organizations reporting at least one cyber incident in the past year and 60% experiencing ransomware attacks in 2024. Breach costs in this sector averaged $10.3 million per incident, far exceeding other industries.
In the technology sector, Bitsight observed continued targeting of software vendors and service providers, particularly through third-party compromise; nearly half (46.75%) of all third-party breaches in Bitsight’s telemetry involved technology products and services.
The finance sector remained a top target, experiencing a 47% year-over-year increase in observed attacks, underscoring the persistent interest in institutions managing digital assets and high-value data.1
Key findings include:
Malware ecosystems
- Malware-as-a-Service (MaaS) and stealer ecosystems remain dominant, with Lumma, Acreed, Katana, and Vidar among the most visible families in dark web markets.
- Remote Access Trojan (RAT) activity increased steadily, reflecting continued reliance on RATs as first-stage infection tools.
- Destructive malware, including wipers, continues to appear in politically motivated operations, blending state-aligned and criminal objectives.
Sector targeting
- Healthcare continues to face the highest attack frequency, driven by ransomware and data exfiltration campaigns.
- Technology organizations were implicated in nearly half of third-party breaches, indicating a sustained expansion of the attack surface through interconnected supply chains. Later in the year, Bitsight observed a relative decrease in dark web mentions, infections, and targeting activity associated with this sector. This decline may reflect temporary shifts in attacker focus, improved defensive posture, or reduced visibility within certain underground sources.a
- Finance experienced a 47% increase in observed attacks compared to 2023, highlighting continued focus on monetary and data-driven targets.
- Education remains vulnerable due to decentralized IT and limited security resources, and underground chatter suggests ongoing interest in selling university network access.
Underground trends
- Increased advertising of MaaS toolkits and stealer logs points to a professionalizing cybercrime market.
- Cross-platform malware written in Rust and Go is becoming standard among emerging actors.
- The use of legitimate communication channels (e.g., Discord, cloud storage) for command and control complicates detection and attribution.
Methodology
This report is based on Bitsight’s monitoring and analysis of underground ecosystems and threat data over the past year. Data and insights were derived from a combination of dark web and deep web collection, malware sample analysis, and exposure telemetry observed across Bitsight’s global vantage points. Analysts reviewed marketplace listings, forum discussions, malware build environments, and affiliated distribution networks to identify emerging trends in Malware-as-a-Service (MaaS), Ransomware-as-a-Service (RaaS), and stealer activity.
All findings represent Bitsight’s independent research and interpretation of underground activity observed to date, supplemented by open contextual indicators where appropriate. No external datasets were used in this analysis.
The state of Malware-as-a-Service
Malware-as-a-Service (MaaS) continues to be one of the most active components of the underground economy. Bitsight assessed this trend based on multiple indicators, including increased stealer infections, a higher number of MaaS advertisements and listings on underground forums, and sustained discussion of subscription-based malware services. Similar to outsourcing a crime, MaaS enables less experienced actors to purchase ready-to-use malware while more advanced developers monetize their code and delivery infrastructure.
Popular MaaS platforms such as Fog, Acreed, and Lumma (often tracked as Lummac2) remain widely circulated across underground marketplaces. Bitsight observed a steady increase in dark web listings promoting these services from January through October 2025. These tools are attractive because they provide turnkey capabilities for data theft, credential harvesting, and extortion thus reducing the technical barrier to entry for aspiring cybercriminals.
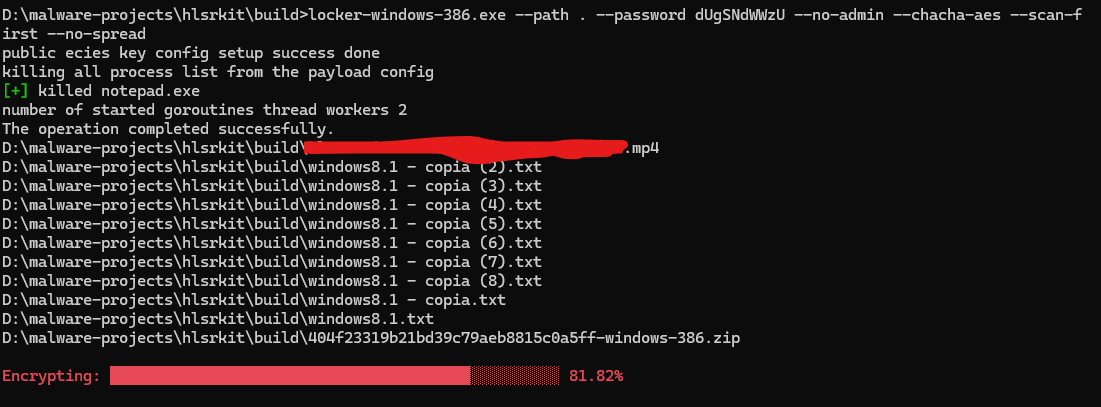
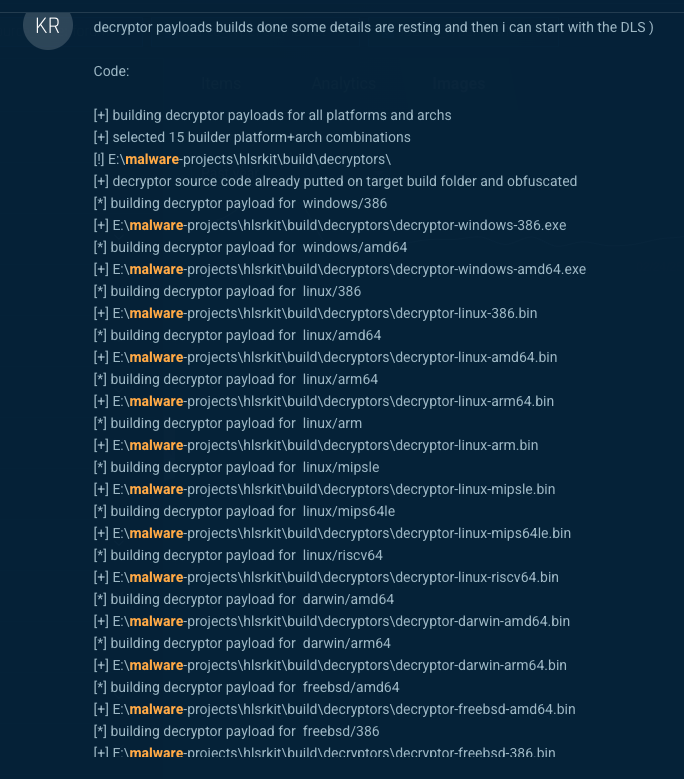
The screenshots below illustrate the build and testing phases of a ransomware framework observed in development environments. In the first, multiple decryptor payloads are compiled across operating systems, demonstrating a cross-platform ransomware toolkit written in Go. In the second, a locker executable is tested, showcasing encryption progress using AES and ChaCha routines, a hybrid approach common in modern ransomware families. These development artifacts mirror behaviors seen in Ransomware-as-a-Service ecosystems, where developers validate functionality before offering their tools for sale or affiliate use on dark web markets.
According to Bitsight Threat Intelligence, Lumma, LummaStealer, Acreed, Katana, and Vidar remain among the most visible Malware-as-a-Service (MaaS) and stealer families observed across underground ecosystems. This assessment is based on aggregated mentions, marketplace listings, and infection telemetry collected from monitored deep and dark web sources.
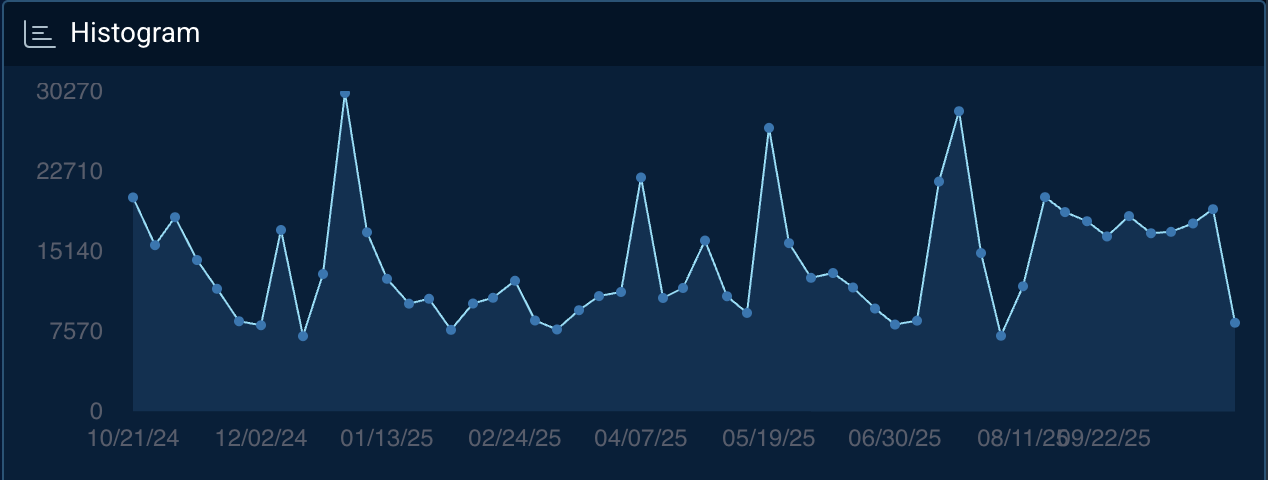
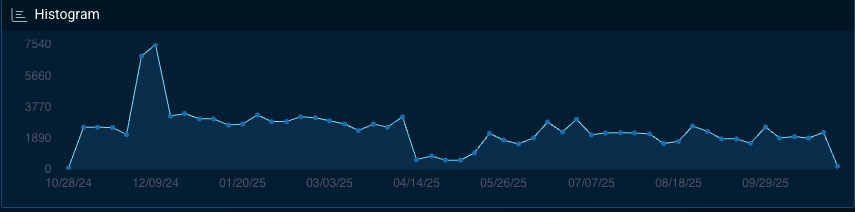
Among remote access and loader tools, several RAT and Trojan families continue to dominate underground discussions and sales activity, reflecting their ongoing role as first-stage infection mechanisms. Figure 1 illustrates the steady level of RAT activity observed across dark web forums and marketplaces, incorporating trends in mentions, listings, and related infection telemetry. All subsequent graphs in this section draw on the same dataset, representing aggregated deep and dark web mentions, marketplace listings, recent activity, and observed infections.
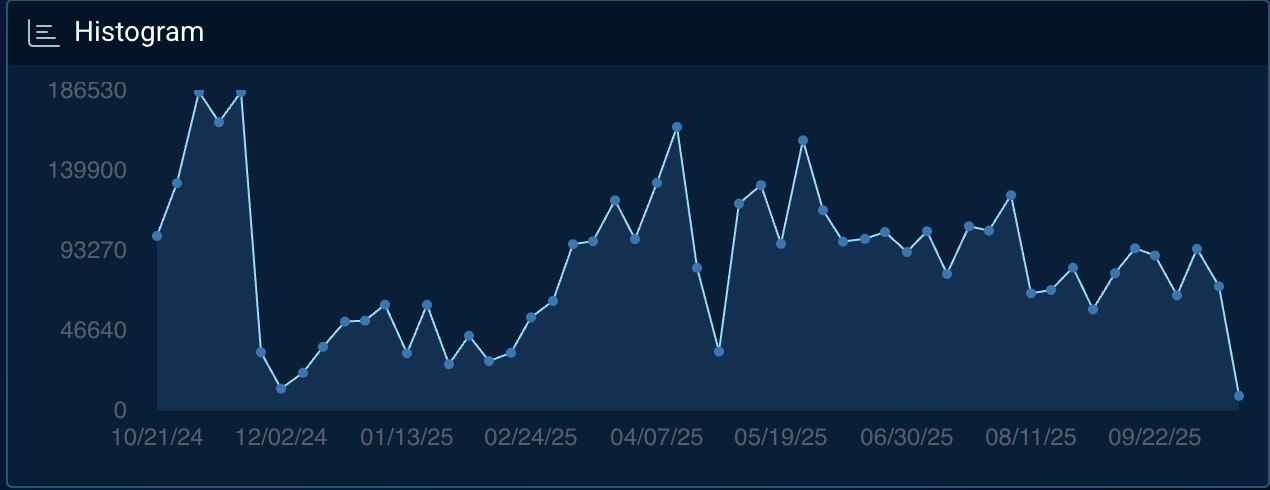
In contrast, general malware activity (as seen below) across the underground shows consistent volume with periodic surges around newly released stealer kits and ransomware variants.
Emerging malware trends and tools from 2025
New and evolving malware families continue to surface, reflecting both innovation among threat developers and the influence of geopolitical conflicts. The following threats and malware tools were particularly active or noteworthy during the first half of 2025:
- Sponsor Backdoor: This malware exploits Microsoft Exchange vulnerabilities (CVE-2021-26855) to gain persistent access and exfiltrate host and network data.
- BUGHATCH Malware: BUGHATCH has targeted organizations across the Americas, exploiting Veeam Backup & Replication vulnerabilities to deploy additional payloads.
- WhisperGate, FoxBlade, DesertBlade, and CaddyWiper: These destructive malware families have been deployed in cyber operations primarily targeting critical infrastructure. Their behavior, overwriting system files and boot records, underscores the continuing intersection between state-aligned and criminal operations.
- ChaosBot: A newly identified malware written in Rust, ChaosBot uses Discord for command and control, blending malicious communication within legitimate network traffic. This highlights an ongoing trend of attackers abusing mainstream platforms for stealth and persistence.
Malware targeting by sector: Who’s most at risk?
Threat actors are motivated by profit, ideology, and influence and their targeting patterns reflect those priorities. During the first half of 2025, Bitsight observed persistent targeting across several key industries.
1. Technology
The technology sector remains one of the most frequently targeted industries. Threat actors continue to exploit trusted vendor relationships, managed service providers, and software supply chains to access downstream clients. The sector’s interconnected nature makes it a prime target for both espionage and financially motivated operations. According to Bitsight Threat Intelligence data derived from observed third-party breach telemetry, nearly half (46.75%) of breaches in 2025 involved technology products and services, underscoring the sector’s systemic exposure through vendor and partner ecosystems.
Bitsight also observed a relative decline in deep and dark web mentions, infection telemetry, and targeting references associated with this sector in recent months. This decrease may indicate a temporary shift in attacker focus, improved defensive posture, or reduced underground visibility rather than a long-term reduction in risk.
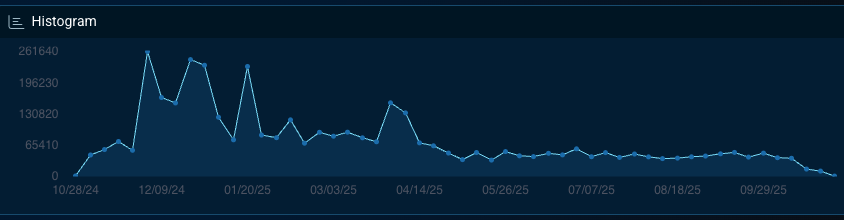
2. Government and Administration
Government organizations continue to face sustained attacks from both state-linked and financially motivated actors. Bitsight observed ongoing data theft, espionage, and disruption campaigns targeting ministries, defense agencies, and local administrations. Dark web chatter and incident telemetry indicate steady pressure on public-sector networks, reflecting the persistent value of governmental and defense-related data.
Although overall activity levels have remained consistent, attacks increasingly leverage vulnerabilities in remote-access infrastructure and publicly exposed services.
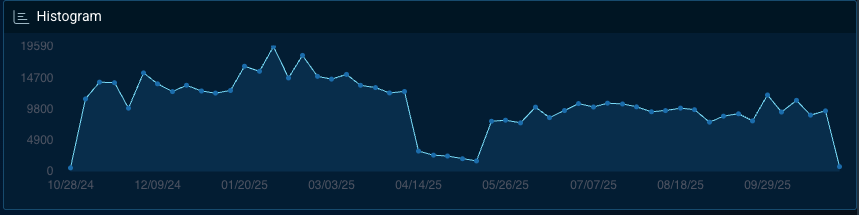
3. Finance
Financial institutions remain highly attractive to attackers because of the concentration of personal and transactional data they hold. Bitsight observed a 47% year-over-year increase in attacks against the finance sector during 2024, driven largely by ransomware and credential-theft campaigns.
While many organizations have improved detection and response capabilities, attackers are adapting quickly with new delivery methods and evasion tactics. Access brokers and stealer-log sellers continue to monetize compromised financial credentials, reinforcing the sector’s persistent exposure within the underground economy.
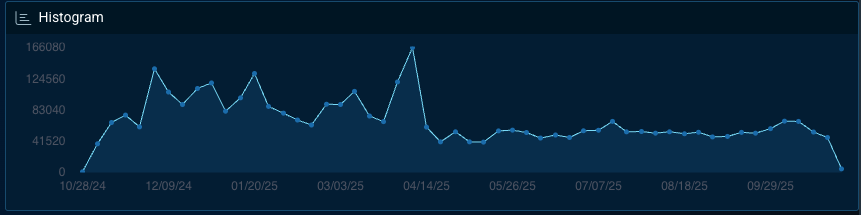
4. Education
Educational institutions continue to experience elevated levels of ransomware and data-theft activity. Decentralized IT environments, legacy systems, and limited resources contribute to ongoing vulnerability. Bitsight data indicates that underground marketplaces regularly advertise access to university networks and research servers, suggesting that educational institutions are being used for both testing and monetization purposes.
Targeting of this sector has remained steady through 2025, reflecting its consistent appeal to opportunistic attackers.
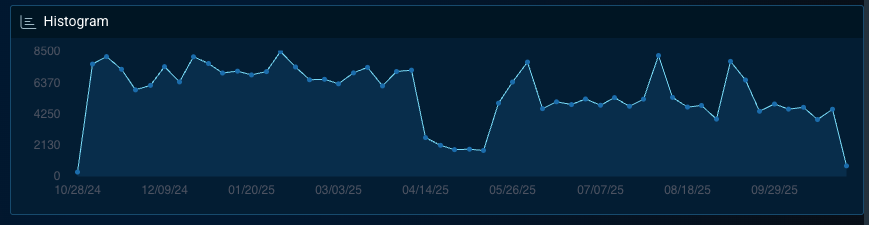
5. Healthcare
Healthcare providers, pharmaceutical firms, and research organizations remain among the most targeted industries due to the sensitivity and urgency of their data. Bitsight Threat Intelligence indicates that 93% of U.S. healthcare organizations reported at least one cyber incident in the past year, and 60% experienced ransomware attacks in 2024.
Breach costs in this sector averaged $10.3 million per incident, the highest across industries. Ongoing ransomware and data-exfiltration campaigns continue to disrupt operations and drive extortion pressure, highlighting healthcare as the single most at-risk vertical.
Outlook: The underground economy ahead
As 2025 progresses, the underground cybercrime economy shows no signs of slowing. Service-based models such as MaaS and RaaS continue to lower the barrier to entry, enabling a wider range of actors to participate in sophisticated operations. Bitsight’s sectoral intelligence indicates that healthcare and technology remain the most persistently targeted industries, while finance and education continue to face steady pressure from credential theft and ransomware campaigns.
Threat actors are increasingly abusing legitimate infrastructure — from cloud platforms to collaboration tools like Discord — to host payloads, exfiltrate data, and manage command-and-control operations, complicating both detection and attribution. Bitsight anticipates continued growth in stealer and loader malware families through the remainder of 2025, alongside sustained third-party and supply chain exposure across critical sectors.
Organizations should maintain heightened vigilance around third-party risk management, patch hygiene, and identity security to mitigate threats emerging from this rapidly professionalizing underground market.
1 Bitsight Threat Intelligence, 2025. Based on observed dark web and exposure data.



