Gartner predicts disaster recovery will become part of the CISO’s job. This isn’t just an IT problem anymore—it’s an enterprise imperative.
Hack to School: Top 10 Cyber Threats Facing the Education Sector in 2025


As students return to classrooms, a different kind of "back-to-school" activity is ramping up: Hack-to-School. Cybercriminals and nation-state actors are intensifying their focus on educational institutions. According to Bitsight Threat Intelligence, the education sector is now the third-most targeted industry by cyber threat actors, facing a wide range of persistent and emerging risks.
Educational institutions, from K–12 to major universities, are increasingly vulnerable due to their reliance on digital platforms and often limited cybersecurity infrastructure. Nation-state actors and financially motivated groups alike are exploiting this weakness.
Key findings from Bitsight Threat Intelligence
- Ransomware attacks: A total of 562 ransomware events targeting the education sector have been recorded, affecting organizations in Spain and Canada recently.
- Nation-state activity: The education sector ranks second in targeting by nation-state actors. Chinese threat actors account for 22 percent of these attacks, with a particular focus on universities involved in advanced research.
- Phishing and QR code exploits: QR code phishing has become a prominent tactic, enabling attackers to bypass traditional email filters and gain unauthorized access to sensitive data.
- Vulnerabilities: The widespread use of legacy systems and expansion into remote learning environments has significantly increased the sector's attack surface. These factors contribute to a high Cyber Risk Index (CRI) score for the industry.
Massive threat activity detected in education
According to Bitsight Threat Intelligence—by scanning thousands of clear, deep, and dark web sources—we found 3,686,102 results referencing or targeting the education sector. From this extensive pool, we extracted the most critical threat intelligence and patterns shaping current risks.
In a Bitsight TRACE research study (2023), we identified the Education sector as the most commonly targeted industry in terms of Known Exploited Vulnerabilities (KEV), accounting for 54.3% of observed incidents. Importantly, activity against education has not declined in the past two years, underscoring the sector’s persistent exposure to cyber threats.
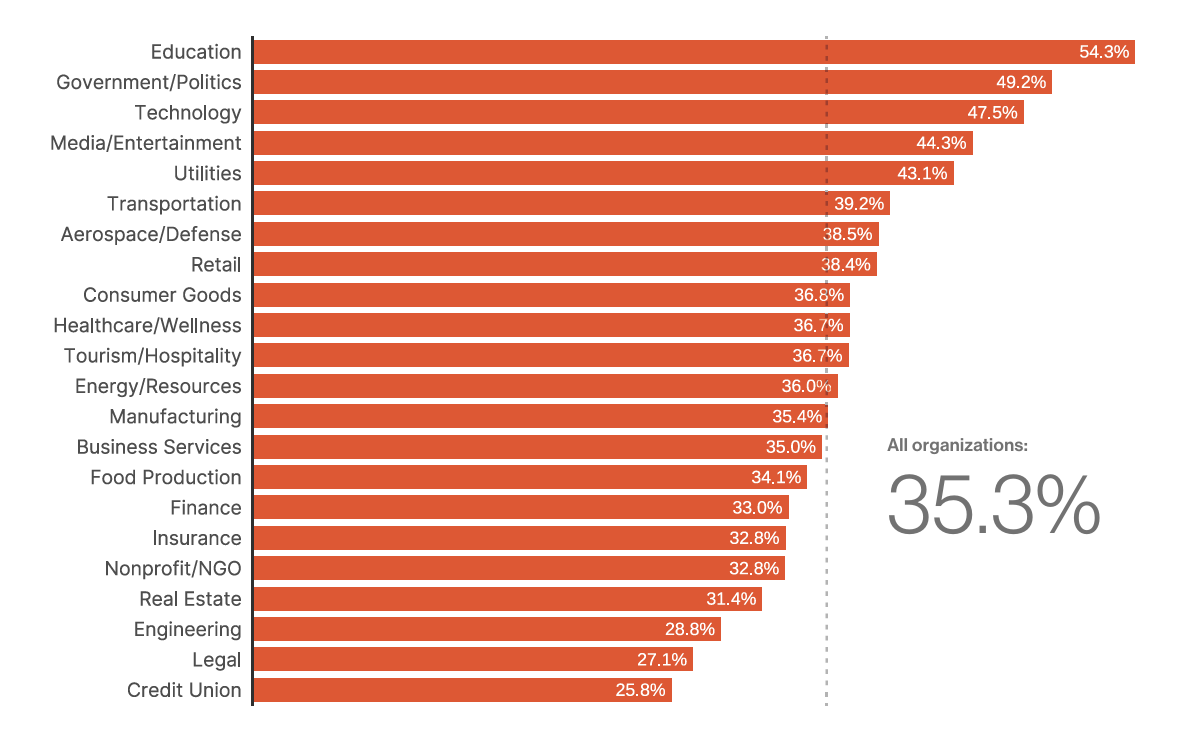
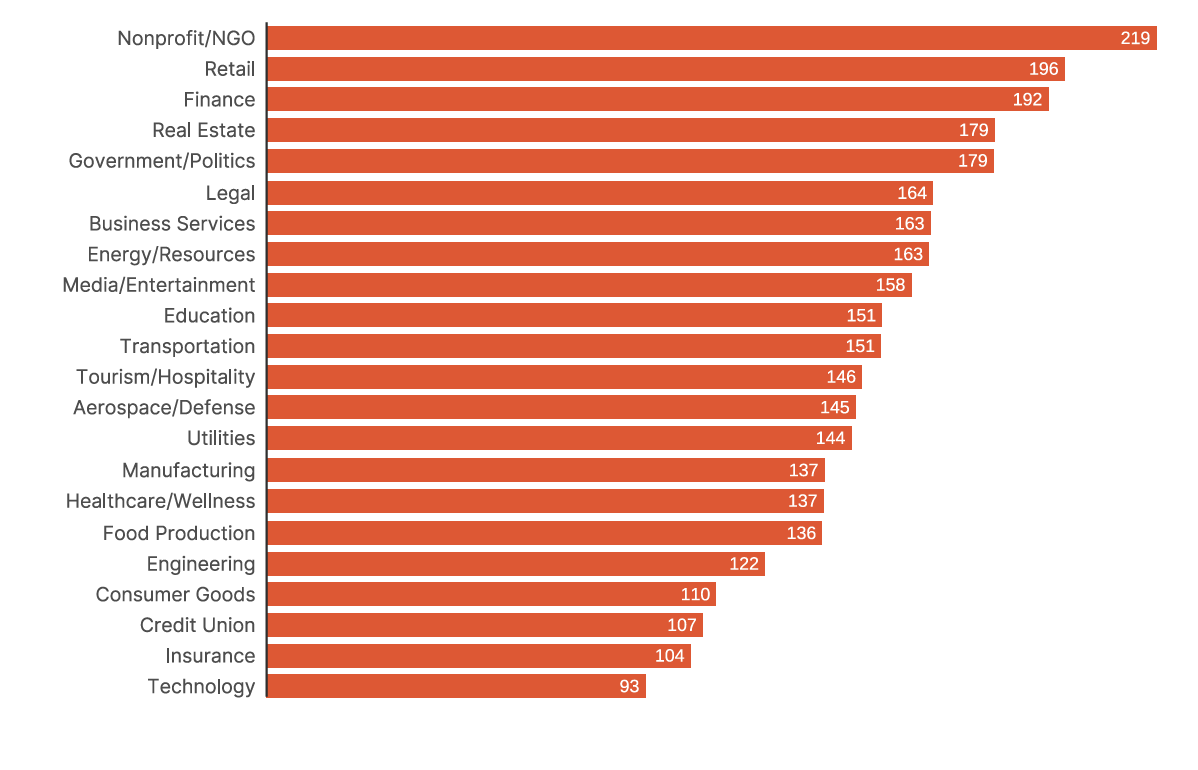
Comparatively, we examined the average time to remediate a KEV across sectors. The Education sector averaged 151 days, placing it in the middle of the pack. By contrast, the Technology sector demonstrated the fastest remediation times, reflecting stronger patch management practices and more agile security operations.
Analyst takeaway:
- 151 days is significant exposure—adversaries routinely exploit KEVs within days or weeks of disclosure, so Education’s remediation cycle leaves a large attack window.
- Technology’s quicker turnaround shows the impact of dedicated security resources, automation, and mature patching processes.
- For the Education sector, this kind of benchmarking highlights both strengths and weaknesses compared to peers. While Education often falls in the middle on KEV remediation timelines, its persistent targeting makes it a frequent “testing ground” for adversaries. Tactics, Techniques, and Procedures (TTPs) refined against Education networks may later be adapted and deployed against more resource-rich sectors such as Finance or Technology.
Top ransomware and malware groups mentioned in the underground
Our dark web monitoring shows the most frequently mentioned ransomware and malware families tied to education-sector targeting include:
- Fog
- Cacao
- Cactus
- Knight
- Owl
These groups represent the frontlines of malware and ransomware campaigns impacting educational institutions.
Top 10 cyber threats facing educational institutions
Based on Bitsight Threat Intelligence and broader industry reporting, here are the most significant cyber threats in the education sector:
- Ransomware
- Phishing and Social Engineering
- QR Code Exploits
- Advanced Malware
- Distributed Denial of Service (DDoS) Attacks
- Insider Threats
- Third-Party and Supply Chain Vulnerabilities
- Cyber Espionage Targeting Research
- Nation-State/APT Activity
- Unpatched Software and Misconfigured Systems
Notable trend: Surge in May 2025
Bitsight detected a notable increase in deep and dark web activity related to the education sector in May 2025. Such surges often coincide with recent breaches or signal preparations for coordinated attack campaigns. It is not yet clear whether this spike is directly connected to any incidents timed around the start of the 2025 school year.
Strategic recommendations for educational institutions
To strengthen cyber resilience and reduce exposure, we recommend the following:
- Enhance cybersecurity infrastructure: Upgrade legacy systems and deploy modern security platforms that block malicious emails, files, and links.
- Phishing awareness and training: Educate staff and students on recognizing phishing and QR code scams. Enforce multi-factor authentication (MFA) across accounts.
- Regular system updates: Patch all systems, especially those involving communication and collaboration tools.
- Monitor and respond: Establish proactive threat monitoring to detect and respond to anomalies. Monitor domains for typosquatting or impersonation.
- Collaboration and information sharing: Partner with other institutions and threat intelligence providers to share best practices and threat data.
Why this matters, and how we can help
The numbers are clear:
- Over 3.6 million deep and dark web references to education-related threats
- 562 confirmed ransomware incidents
- A rising tide of nation-state and criminal targeting
- School Systems host a massive amount of Personally Identifiable Information (PII), making them a hot target for cyber criminals looking to make some money
This is not a theoretical risk. Educational institutions are under constant attack, and their data, operations, and reputations are on the line.
Bitsight Cyber Threat Intelligence provides educational organizations with:
- Real-time visibility into threat actor behavior and malware campaigns
- Contextualized alerts on deep and dark web chatter tied to specific schools or universities
- Insights into QR code phishing trends and new ransomware threats
- Monitoring of supply chain vulnerabilities and third-party exposures
Conclusion
The education sector’s growing reliance on digital systems, combined with limited cybersecurity resources, makes it an appealing target for adversaries. By implementing the right tools and practices, and by acting on threat intelligence from providers like Bitsight, educational institutions can defend against attacks and build a stronger, more secure future for students and staff alike. If you’d like to learn more, please reach out to our team.



