Identify and prioritize vulnerabilities that pose the greatest risk to your organization.
Assess the likelihood of a CVE being exploited.
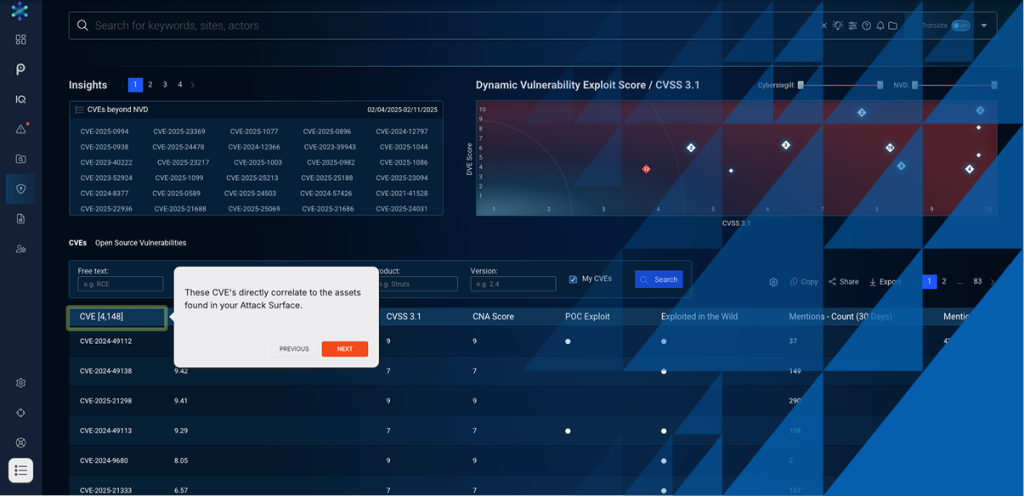
Vulnerability exploitation is rapidly becoming the most common attack vector for cybercriminals. And while CVEs continue to be reported and published every day, some are at higher risk of exploitation than others. As a result, it’s easy for teams to feel simultaneously overwhelmed by the sheer number of CVEs to keep track of and unsure about how to make the best decisions regarding mitigation and prioritization.
That’s where Bitsight Vulnerability Intelligence comes in: an end-to-end vulnerability exploit intelligence solution powered by our proprietary Dynamic Vulnerability Exploit (DVE) score, delivering immediate, AI-cultivated CVE risk assessments within hours of publication. By complementing traditional static scoring systems like CVSS with real-time threat intelligence and underground cybercriminal activity, security teams can focus on the vulnerabilities that pose the greatest risk to their organization.
Too many CVEs, too much time to respond.
Manage vulnerabilities, not the other way around.
Support across the entire CVE lifecycle.

“The DVE Score is a huge time saver. Not only can you drill in to identify the sources and content of real issues, but you don’t put time into things that aren’t issues or likely to become issues.”
-Global Threat Intelligence Manager
Threat Intelligence Services
We are ready to help. Learn more about our cyber threat intelligence services.

