We've sourced several guides and checklists covering some of the most important topics facing cybersecurity professionals when it comes to third-party risk management. Find insights to put to practice, identified and compiled by security experts.

TPRM learning center
Learn about third-party risk management
It's vital for cybersecurity professionals to stay informed about emerging threats, vendor risk security strategies, and evolving regulatory requirements. This resource center offers valuable insights into key areas such as mitigating third party risk, vendor risk assessments, zero trust, TPRM tools, and more. Having a deeper understanding of these foundational topics is crucial for security and risk managers looking to strengthen their organization’s security posture and proactively mitigate risks.
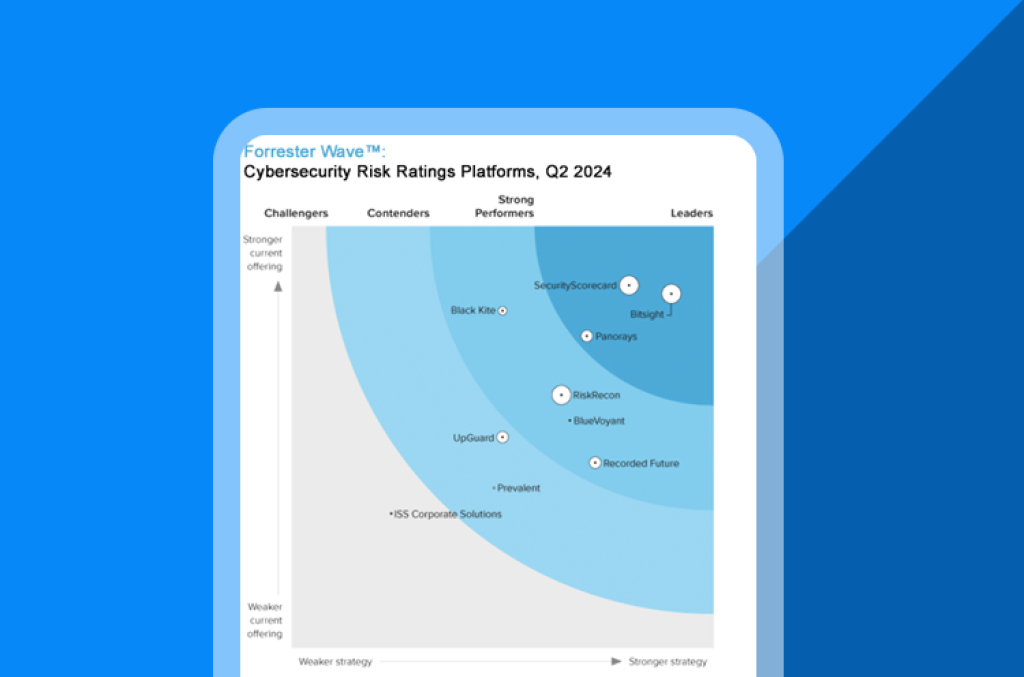
Navigate Cyber Risk Ratings with Confidence
Cyber risk ratings platforms are proliferating—and not all are built equal. Forrester’s 25‑criterion evaluation reveals who’s delivering accuracy, scale, and vendor credibility. Use it to shortlist tools aligned to your risk appetite and control framework.
Manage third-party risk across your digital supply chain
Bitsight solutions help you maintain control over your vendors, your vendors’ vendors, and so on, from onboarding and assessments, to threat monitoring and response, to offboarding. Stay ahead of threats by focusing your priorities, trusting our externally validated data and insights, and managing workflows from end to end. Showcase how your team keeps third-party risks at bay.