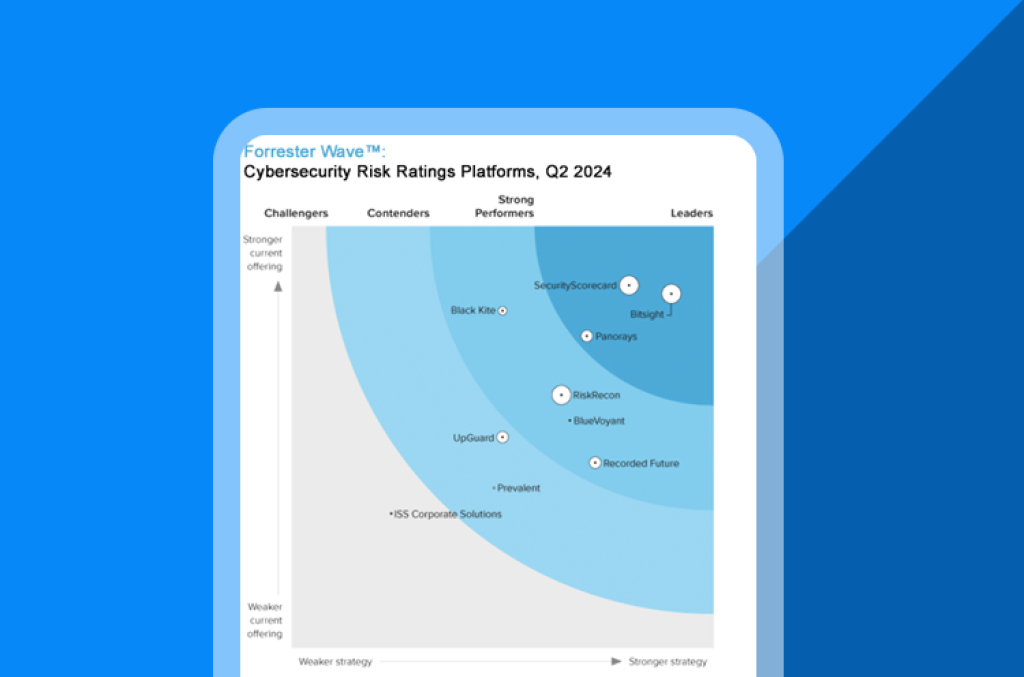
Cyber risk ratings platforms are proliferating—and not all are built equal. Forrester’s 25‑criterion evaluation reveals who’s delivering accuracy, scale, and vendor credibility. Use it to shortlist tools aligned to your risk appetite and control framework.
What is Zero Trust?
What is Zero Trust?
Zero trust is a cybersecurity approach that restricts network access so only the right people are accessing the specific information they need—and nothing more. Zero Trust is is built on the principle that no user, device, or network segment should be implicitly trusted, regardless of location or identity. Instead, every access request is continuously verified based on contextual factors such as identity, device posture, and real-time risk analysis. In a world increasingly characterized by sophisticated threats and expanding digital ecosystems, Zero Trust emerges as a foundational model for securing modern organizations.
The term was coined by John Kindervag at Forrester Research in 2009, and related frameworks include Google’s BeyondCorp and Gartner’s CARTA. Today, it’s a key component of cybersecurity programs, especially in organizations that outsource business functions to third-party vendors who need remote access to their networks.
Here’s everything you need to know about the basic principles of Zero Trust and how to apply them to your third-party risk management program (TPRM) to create more secure remote access connections.
Zero Trust principles
- Least-privilege access, which means increasing granularity on permissions for internal users and third-party vendor users. Apart from limiting who accesses the network, it also limits what services, devices, or applications; where; and when they’re accessed.
- Logs and audits, which help monitor vendor access and verify that they are not violating any access restrictions, either through malicious activity or just careless actions.
- General security mechanisms to apply advanced controls to third-party relationships, such as multi-factor authentication (MFA), identity access management (IAM), and a strong password policy that also disables identities once they are no longer working for the organization.
What is Zero Trust architecture?
Zero Trust Architecture (ZTA) is the implementation framework that applies the Zero Trust principles to IT environments. At its core, ZTA ensures that every access attempt, whether internal or external, is treated as potentially compromised. This approach removes implicit trust and focuses on continuous authentication and authorization. ZTA employs micro-segmentation to isolate networks and limits user access to only what's absolutely necessary, significantly minimizing potential damage from third-party breaches.
What is Zero Trust security?
Zero Trust Security extends beyond network architecture to encompass comprehensive policy enforcement and continuous monitoring of all access points. It integrates advanced technologies such as identity management, multi-factor authentication (MFA), encryption, endpoint detection, and response (EDR) solutions. By constantly validating users and devices, Zero Trust Security proactively identifies and mitigates threats before they can cause significant damage, dramatically improving an organization's overall cybersecurity posture.
What is Zero Trust in cybersecurity?
In cybersecurity, Zero Trust embodies a fundamental shift from traditional perimeter-based security approaches to one of continuous verification and least-privilege access. Rather than assuming trust based on network location, Zero Trust mandates verification at every step. This strategy significantly reduces the likelihood of lateral movement during cyberattacks, limiting both exposure and impact.
What are 5 pillars of Zero Trust?
The Zero Trust model is built upon five foundational pillars:
- Identity: Ensuring robust authentication and verification of user identities.
- Device: Continuously assessing device security posture and compliance.
- Network: Applying micro-segmentation to secure internal communications.
- Application: Protecting application layers with context-aware access controls.
- Data: Implementing strong encryption and access restrictions around sensitive data.
How to implement Zero Trust
The Zero Trust technique revolves around continuous validation and strict access controls. It leverages advanced analytics and real-time cyber threat intelligence to provide context-aware security decisions. This technique ensures that even legitimate access attempts undergo stringent validation processes, constantly adapting based on the dynamic risk landscape.
Implementing Zero Trust involves several critical steps, beginning with an understanding of your current security landscape and business objectives. Organizations must:
- Identify critical assets and define sensitive data and systems.
- Map transaction flows across network segments and user access points.
- Establish robust identity and access management controls, integrating MFA and least-privilege access.
- Continuously monitor and analyze traffic for anomalous activities using cybersecurity intelligence solutions, such as Bitsight's Cyber Threat Intelligence suite.
- Employ micro-segmentation and encryption strategies to isolate and protect critical resources effectively.
Implementing Zero Trust in your organization
There are some technologies and infrastructure settings that can help organizations.
In August 2020, NIST released the NIST Special Publication 800-207: Zero Trust Architecture, which describes the components of a zero trust architecture, possible design scenarios, and threats. It also offers a roadmap to implement its main principles.
Dedicated solutions like Bitsight Vendor Risk Management (VRM) allow you to manage custom privileges for your third-party vendors based on job titles, departments, and roles. This makes it easier to manage the provisioning and de-provisioning of user permissions, with network access based on the least-privilege principle and granular controls to restrict third-party remote access to only the application they need and nothing else.
How does Zero Trust fit into third-party risk management?
Third-party relationships significantly expand an organization's attack surface, creating substantial cyber risk. Integrating Zero Trust principles into third-party risk management (TPRM) ensures every vendor and external partner undergoes continuous monitoring and strict verification processes. Solutions like Bitsight's Continuous Monitoring for third parties provide real-time insights into the security posture of your entire vendor ecosystem, aligning effectively with Zero Trust methodologies to identify and mitigate risks rapidly.
By adopting Zero Trust, organizations can better manage their cybersecurity risks, secure their extended digital ecosystems, and create resilience against evolving threats.
Why do you need to consider Zero Trust in your TPRM program?
A study by the Ponemon Institute found that:
- 63% of organizations said remote access is becoming their weakest attack surface
- 51% experienced a third-party data breach in the 12 months prior to the study
- 74% said it was the result of giving too much privileged access to third-parties
In addition, the accelerated digital transformation shifted the focus of security teams to more tactical needs, such as enabling remote workers, securing changes in operations to ensure business continuity, migrating to the cloud, re-assessing third-party and supply chain risks, accelerating and increasing vendor onboarding, and more.
In a world where the network perimeter is enlarged and has blurry boundaries, zero trust allows organizations to constantly re-evaluate in real-time anything and anyone that touches their data.
How is Zero Trust different from other approaches?
You’ve probably heard “trust but verify” in the context of cybersecurity and third-party risk. To that, zero trust responds: “Never trust, always verify.”
According to this approach, devices should not be trusted by default, even if they are connected to a permissioned network such as a corporate LAN and even if they were previously verified. Authentication or verification is always needed before granting access to sensitive data or protected resources.
Zero trust deems all resources as external to the organization’s network, and continuously verifies users, resources, devices, and applications before granting the minimum level of access required. In contrast, the traditional approach automatically trusted users and endpoints within the organization’s perimeter.
But time is precious and there aren’t enough hours in the day to review every access attempt. In order to make this concept applicable, zero trust uses broad data sets and dynamic risk-based policies to aid access decisions and perform continuous monitoring.
Another component of a secure third-party vendor ecosystem
Organizations make significant efforts to control and secure the access given to third-party vendors, in order to avoid data breaches, security incidents, or noncompliance. Zero trust is another tool for mature enterprise risk management practices, establishing the framework for minimizing third-party risk on every network access.
With grounds on continuous verification, third-party vulnerabilities and insufficient security practices can be properly addressed.
While no security and defense strategy is immune, and data breaches will continue to happen, zero trust reduces the attack surface and limits the impact of a cyberattack.