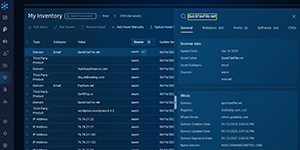
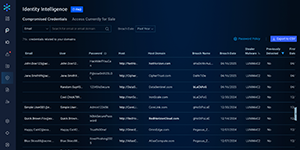
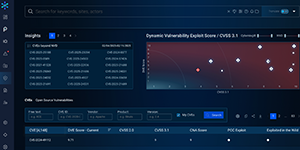
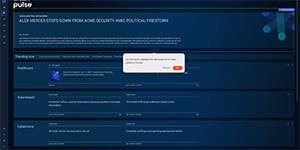
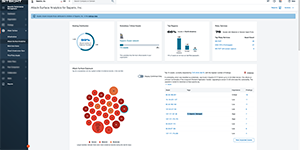
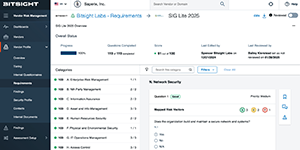
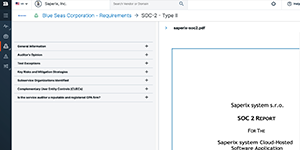
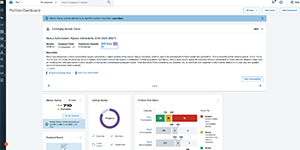
See what Bitsight can do for you, on your schedule. Discover platform capabilities firsthand—from summarizing lengthy SOC 2 reports to detailing compromised credentials—with interactive, self-guided tours.
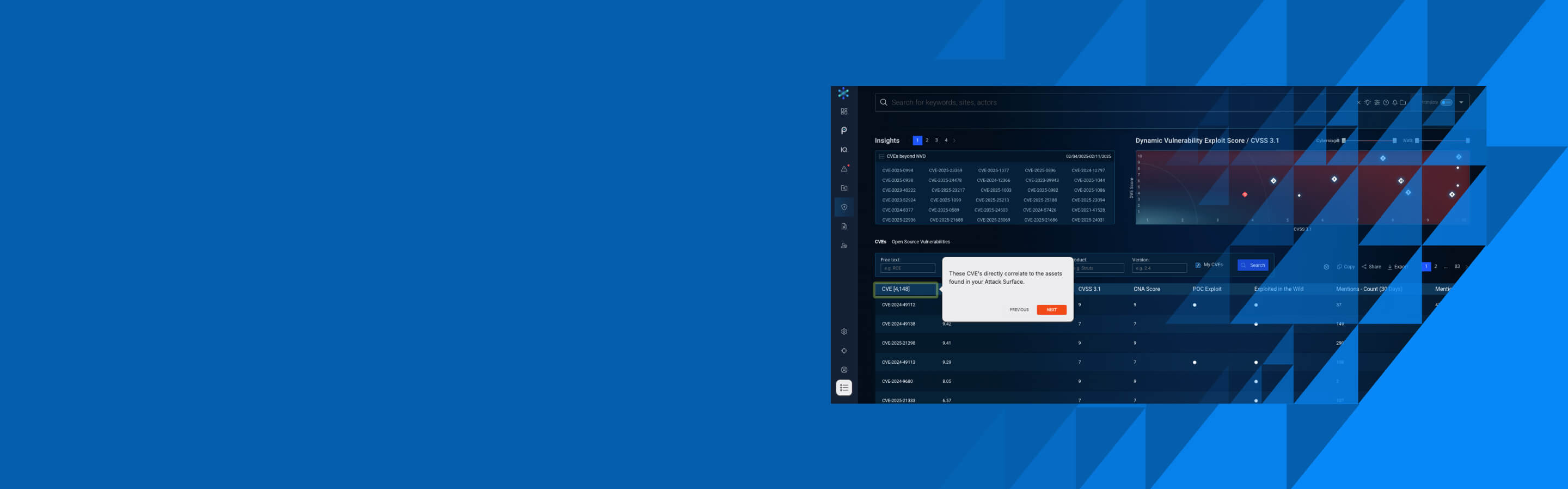
Cyber Threat & Exposure Interactive Tours.
If you want to see an interactive tour of the full product you can ▶ start the interactive tour here. The tours of the individual modules are below.
Request Demo
Like what you see?
Enjoying these interactive tours? Talk to us live and we're happy to give you a
personal demo of our solutions and see data related to your organization.