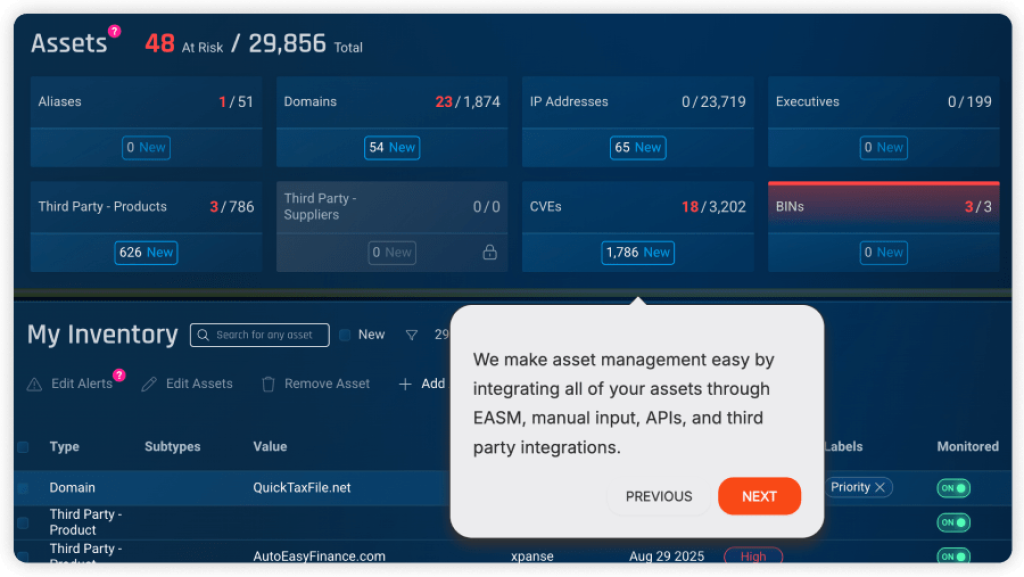
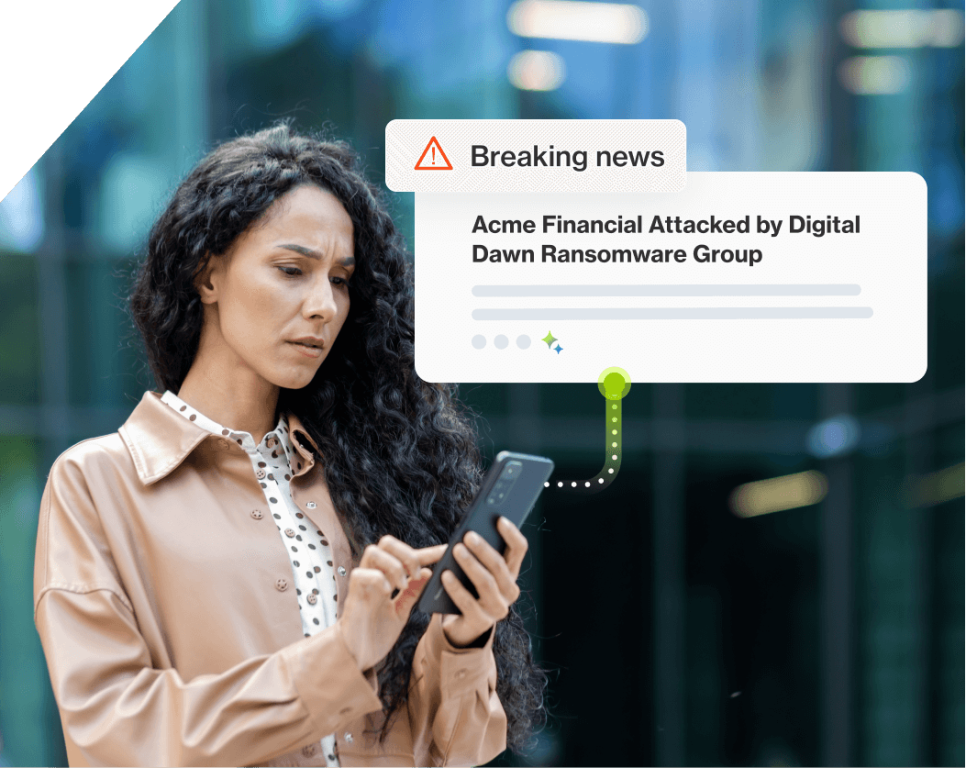
Without linking external threat intelligence to an organization’s specific attack surface, security teams lack the full context they need and often waste time on low-impact risks while high-priority threats and risks remain exposed.
Take control of your organization’s risk with Bitsight Cyber Threat Intelligence, which captures, processes, and alerts teams to emerging threats, TTPs, IOCs, and their risk exposure as it surfaces. Translate raw threat data from some of the most common risk areas—including compromised credentials, vulnerabilities, ransomware, adversaries, and more—into instant insights powered by Bitsight AI so you can get ahead of what’s coming.