Be the first to spot compromised credentials. Secure your assets. Protect your organization.
Bitsight Identity Intelligence
Identity Intelligence & Credentials
Prevent compromised accounts from compromising your business.
Compromised credentials pose a significant threat to organizations. They can be used to impersonate users, escalate privileges, and carry out malicious activities such as data theft, fraud, or sabotage. By identifying these risks early, security teams can take preemptive measures to ensure organizational safety and integrity.
With the Bitsight Identity Intelligence & Credentials module, security teams get an AI-aggregated, streamlined view of their organizations’ risk to underground markets exposing leaked credentials, including usernames and passwords, plus access to endpoint information collected by Stealer malware for organizational risk analysis. Users can also view credentials currently for sale and take action to purchase them back, proactively defending against threats to their organization, assets, and customers.
Identify exposed credentials found on the dark web
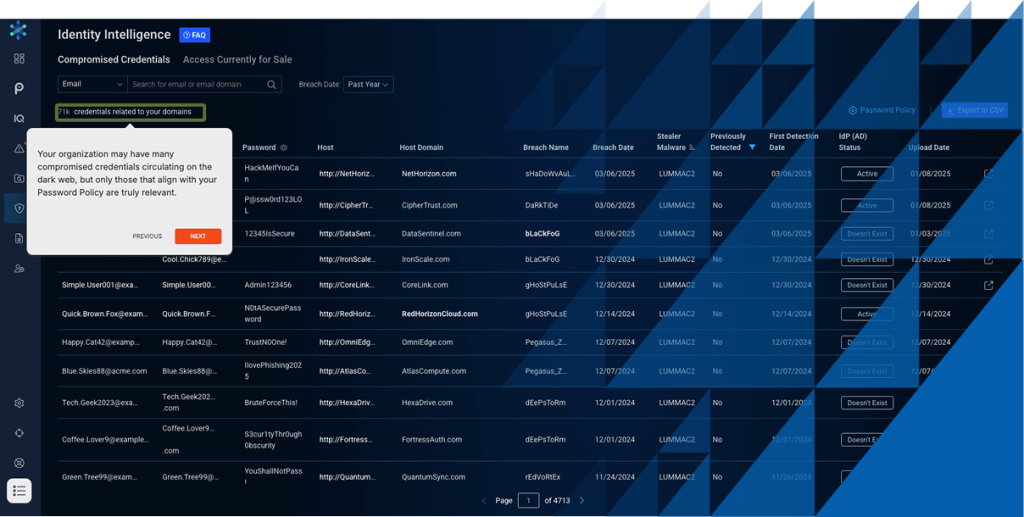
The Compromised Credentials tab focuses on organization and employee credentials that can be attributed to specific systems, e.g. corporate portal, Jira instance, Netflix account and more. These primarily originate from logs of stealer malware (infostealer).
- Cut through the noise with advanced filter capabilities, including identity provider integrations and password policies, for precise credential leak filtering
- Assign prioritization criteria for compromised credentials according to organizational needs
- Access endpoint information collected by stealer malware and aggregated by Bitsight AI for organizational risk analysis
See what’s currently being sold across the underground and reclaim access
The Access Currently for Sale tab displays organizational access available for purchase across underground markets. This data is based on the assets (domains and IPs) that are listed in an organization’s attack surface.
- View the Affected Assets, Details, Compromised Accounts, and Malware data related to the selected Asset
- Filter based on the importance level of the asset
- Reclaim what’s yours with quick access to available takedown/purchase services
Threat Intelligence Services
We are ready to help. Learn more about our cyber threat intelligence services.
Mitigate your exposure. Limit damage to your operations.
From the onset of activation, the Identity Intelligence & Credentials module provides immediate data on compromised accounts and continuously monitors organizational domains across the cybercriminal underground in real time. We leverage AI to aggregate and streamline the data so your team can better safeguard priority assets and proactively remediate threats.


