Ransomware, breach sharing, stealer logs, credentials, and cards. What has shifted and how to respond.
Critical Care, Critical Risk: Inside the Cyber Threats Targeting Healthcare
Tags:


Audio Recap
Overview
The healthcare sector remains one of the most targeted industries for cyber attacks due to its critical role in national infrastructure and its extensive repositories of sensitive data containing personally identifiable information (PII). It’s widely assumed that threat actors target healthcare and related organizations because they are perceived as more likely to pay a ransom to restore critical systems and protect patient safety in the event of an attack.
The sector’s ongoing digital transformation, including the rapid adoption of cloud-based systems and AI-driven technologies, has further expanded the attack surface and introduced new vulnerabilities that adversaries continue to exploit. According to Bitsight Threat Intelligence, these developments have made healthcare entities increasingly attractive to both financially motivated and state-sponsored threat actors.
In 2023, the HCA Healthcare breach affected approximately 11 million individuals, followed in 2024 by the Change Healthcare cyber attack, which impacted an estimated 190 million people. These incidents underscore threat actors’ growing willingness to target healthcare-related organizations, driven by the expectation of substantial financial payouts and the critical importance of healthcare operations.
Key cybersecurity threats in healthcare
Ransomware attacks
The healthcare sector continues to experience a high volume of ransomware incidents. Our intelligence indicates that multiple ransomware operations have been observed targeting healthcare institutions globally. These attacks often involve the encryption of critical patient and operational data, followed by ransom demands to restore access. Such incidents disrupt healthcare delivery and compromise patient safety.
Data breaches
Due to the sensitive nature of patient information, healthcare organizations are frequent targets of large-scale data breaches. By 2024, the average cost of a data breach in healthcare was nearly $10 million, the highest among all industries. Data breaches not only result in financial losses but also erode public trust and regulatory compliance standing.
Nation-State threat activity
Nation-state actors have increasingly focused on healthcare infrastructure to gather intelligence, disrupt services, or undermine public confidence. These actors often deploy custom-built malware to compromise IT networks and operational technology (OT) environments. Bitsight Threat Intelligence has observed an uptick in sophisticated campaigns that blend espionage with disruptive objectives.
Recent healthcare incidents
In January 2025, a ransomware group conducted a coordinated attack against multiple healthcare entities. The campaign caused temporary system outages and data encryption events, highlighting the sector’s continued vulnerability to ransomware operations.
In another case, threat actors exploited weaknesses in outdated IoT-enabled medical equipment within a large healthcare network. The intrusion resulted in widespread operational disruption and the exposure of thousands of anonymized patient records. Analysis by Bitsight Threat Intelligence confirms that the exploitation of unpatched IoT devices remains a persistent attack vector across healthcare environments.
More recently, Bitsight threat researchers identified instances of personally identifiable information (PII) related to healthcare organizations being leaked and discussed on dark web forums. In one instance, a spreadsheet containing donor information, including names and physical addresses, was discovered, placing affected individuals at elevated risk of identity theft and social engineering attempts.
In a separate case, Bitsight Threat Intelligence observed hospital-related financial data, including anonymized transaction details and bank account numbers, circulating on dark web marketplaces.
These findings demonstrate the expanding scope of data exposure impacting the healthcare sector and reinforce the importance of continuous dark web monitoring and the integration of actionable threat intelligence.
Top CVEs and malware targeting healthcare institutions
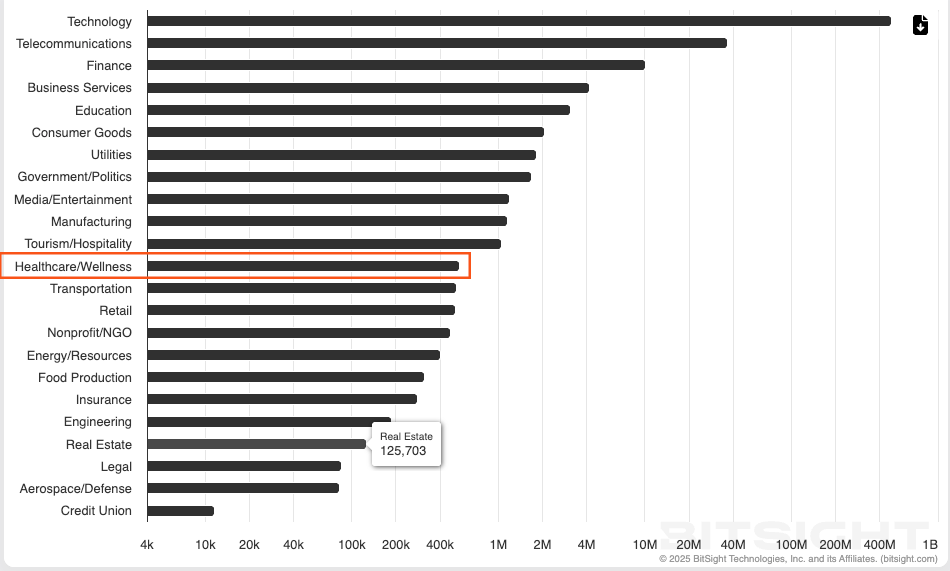
Over the past month, the leading CVEs affecting the healthcare industry have been CVE-2025-10035, CVE-2025-0603, and CVE-2025-11319. The most prevalent malware families impacting the sector include Solarmarker, Resident, Edam, Broomstick, Oyster, and Scarabey.
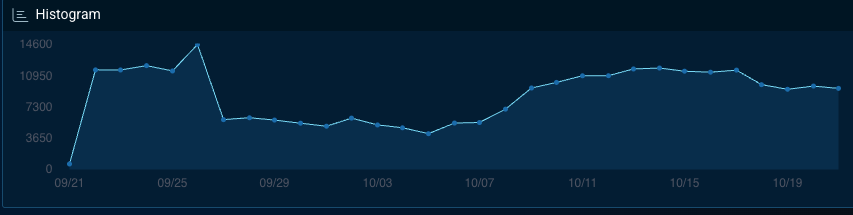
The above graph shows the ebb and flow of discussion regarding the healthcare industry on the deep and dark web over the past month.
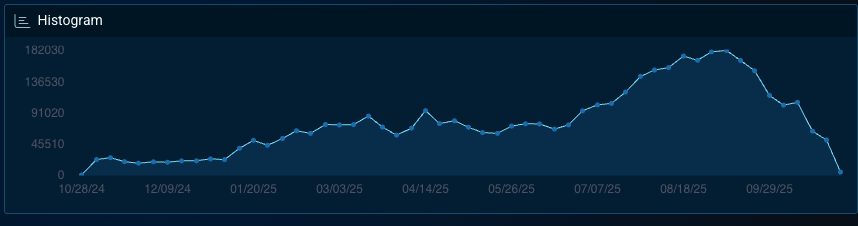
The above graph shows the rise in healthcare industry chatter and targeting over the past year.
Mitigation and prevention strategies
Adopt best practices
Healthcare providers should implement multi-factor authentication, maintain secure and redundant data backups, apply timely software patches, and conduct proactive vulnerability assessments. These foundational practices can significantly reduce the risk of compromise.
Enhance cybersecurity frameworks
Organizations must strengthen their cybersecurity posture through continuous risk assessments, network segmentation, and zero-trust architecture. Regular training and awareness programs for staff remain essential to preventing phishing and social engineering attacks.
Leverage AI and advanced technologies
Integrating AI-driven threat detection and response tools can enhance resilience by automating incident identification and remediation. Bitsight Threat Intelligence recommends adopting advanced analytics to detect anomalous activity patterns indicative of early-stage intrusions.
See how you can stay ahead of threats facing the Healthcare industry with Bitsight Pulse, your personalized, AI-driven stream of cyber threat intelligence content, from ransomware to breaking news. Or, talk to our team to learn more about how Bitsight Threat Intelligence can help.



