The 2025 State of Cyber Risk and Exposure report reveals why security leaders are under pressure: AI-driven threats, expanding attack surfaces, and misalignment with business priorities. Based on global survey data, it surfaces the root causes behind today’s risk fatigue—and what mature organizations are doing differently.
Reaching Peak Understanding of IoT and ICS Risk
Tags:


In a world where internet connectivity intersects with just about every facet of our physical world—from cameras and door locks to power grids and factory robots—cyber risk intelligence has moved well beyond just protecting the bits and bytes of logical IT ecosystems. Security and risk professionals also have to be on the lookout for and aware of improperly secured cyber physical devices, like IoT devices, which greatly expand the enterprise attack surface.
As a part of our research for the 2025 State of Cyber Risk and Exposure report, we asked our pool of 1,000 cybersecurity and risk leaders about their perception of risks around internet of things (IoT) and industrial control security/operational technology (ICS/OT) devices, both of which are at the root of modern cyber physical infrastructure. They control everything from gas lines and power grids to home security cameras.
The results? IoT and ICS/OT devices are everywhere:
- 85% of respondents say their firms use IoT
- 79% of those say at least some of IoT devices are exposed to the internet
- 78% of those say at least some of ICS/OT devices are exposed to the internet
- 69% of firms report they use ICS/OT devices
Why perceived risk doesn't always reflect reality
These numbers are staggering, not because the use of the devices is alarming, but rather, the security risks they bring with them. While it’s encouraging to see growing awareness around these risks, our data suggests that some executive teams may still be building their understanding of where and how cyber-physical vulnerabilities surface, particularly when it comes to ICS/OT environments.
Interestingly, the estimates we gathered from respondents actually outpace the level of ICS/OT exposure we’ve observed in the wild. At first glance, that might seem encouraging, perhaps even a sign that organizations are erring on the side of caution. But we suspect it reflects a deeper issue: limited visibility into what’s really happening within their environments, and in some cases, confusion about what “internet exposure” actually entails.
To be fair, part of this discrepancy could stem from how the survey questions were framed. That’s one reason we initially held back from publishing these results, they didn’t neatly fit into our broader narratives on cyber risk. However, given the recent work from our Bitsight TRACE team on both IoT and ICS/OT exposure, we believe these findings deserve a closer look. They provide a useful starting point for unpacking the bigger challenges tied to cyber-physical risk.
IoT risk and exposure
Most executives have a solid grasp of the fundamentals when it comes to IoT, particularly how it supports business value. IoT brings internet-enabled visibility and control to everything from breakroom refrigerators to conference room cameras. It powers smart building capabilities and plays a foundational role in creating the “data-driven enterprise” by making operations more measurable. Whether it’s connected sensors on fleet vehicles, assembly line machinery, or shipping pallets, IoT generates the data that fuels advanced analytics and predictive AI.
Of course, the flip side of IoT’s business value is the increased risk it brings. Every connected device introduces a potential entry point for attackers. Even something seemingly harmless—like a smart fridge—can become a foothold for a much larger breach if it’s running outdated software with known vulnerabilities and isn’t properly segmented from critical systems. Beyond the sheer volume of new exposure points, IoT also introduces new attack dimensions, especially when devices are involved in, or have visibility into, sensitive operations.
The ubiquitous IP camera offers a perfect example of the many types of exposure that IoT devices open up. A study in June by Bitsight TRACE researchers found that there are over 40,000 exposed cameras streaming live on the internet with no passwords or other protections keeping unauthorized people from using and abusing these streams (unsurprisingly, it’s heavily focused on telecommunications).

“It doesn’t take elite hacking to access these cameras; in most cases, a regular web browser and a curious mind are all it takes, meaning that 40,000 figure is probably just the tip of the iceberg,” wrote João Cruz, principal security research scientist for Bitsight TRACE in a recent blog on the report, Big Brother is Watching (And So is Everyone Else).
This is what it means to have a device fully exposed on the internet, remotely accessible with either weak or non-existent credentials protecting them.
The link between Bitsight TRACE’s research and Cyber Threat Intelligence is both clear and significant. The research showed that threat actors are well aware of these exposed devices, even those with partial protections that remain vulnerable to exploitation. Access to internet-connected cameras, for example, is actively being bought and sold as a revenue stream in criminal markets. Because these devices are often located in sensitive areas, like data centers or ATMs, they can be leveraged in more sophisticated attacks to gather intelligence or exfiltrate sensitive data.
Based on our Bitsight threat intelligence and vulnerability research like the connected cameras study, as well as the preponderance of industry data, we believe the IoT estimates from our respondents to the State of Cyber Risk and Exposure report are realistic. While the number of exposures is alarming, it’s positive to see a high level of awareness of this risk and hope it’s tied to initiatives to start bringing those numbers down.
ICS/OT risk and exposure
When we compare ICS/OT exposure estimates from the State of Cyber Risk and Exposure survey to what we’ve observed in the field, the picture looks very different. Roughly half of survey respondents believe their organizations have ICS/OT devices exposed to the public-facing internet. But in reality, our research shows the number is closer to 0.306%—a nearly 100x difference.
While this gap can be seen as a sign of growing awareness, it is also evidence of some misunderstanding. And we suspect the confusion happens on two levels.
ICS/OT ≠ IoT
One likely explanation is that some respondents may have conflated ICS/OT with IoT devices, particularly those tied to smart building systems or other remote functions. While there is some overlap, ICS/OT is generally more specialized and much more sensitive. These are the systems that control critical processes: SCADA systems in power plants, programmable logic controllers (PLCs) on factory floors, and distributed control systems (DCS) that automate industrial environments.
Confusion on definition of ‘exposed to the internet’: Additionally, we suspect that since we didn’t explicitly define it in our question that some respondents weren’t 100% clear on what we meant by ‘exposed to the internet.’ We think it is likely that some respondents conflated internet-connected devices with exposure to the internet. To be clear, what we mean here are devices that are not protected by even a modicum of protection, such as placement behind a firewall and network segmentation.
Now, to be clear: this overestimation isn’t cause for celebration. Even a small percentage of exposed ICS/OT devices represents an outsized risk—these are the systems that run power plants, water treatment facilities, and other critical infrastructure. And from a volume standpoint, the numbers are far from small. We continue to see tens of thousands of these devices exposed worldwide.
In fact, the Bitsight TRACE team recently updated its long-term study, first published a few years ago, which revealed around 100,000 ICS/OT devices exposed to the internet each month. That figure has now climbed to more than 180,000 publicly reachable, unique IPs tied to the 13 most common ICS/OT protocols. At the current pace, global exposure is on track to exceed 200,000 IPs per month.
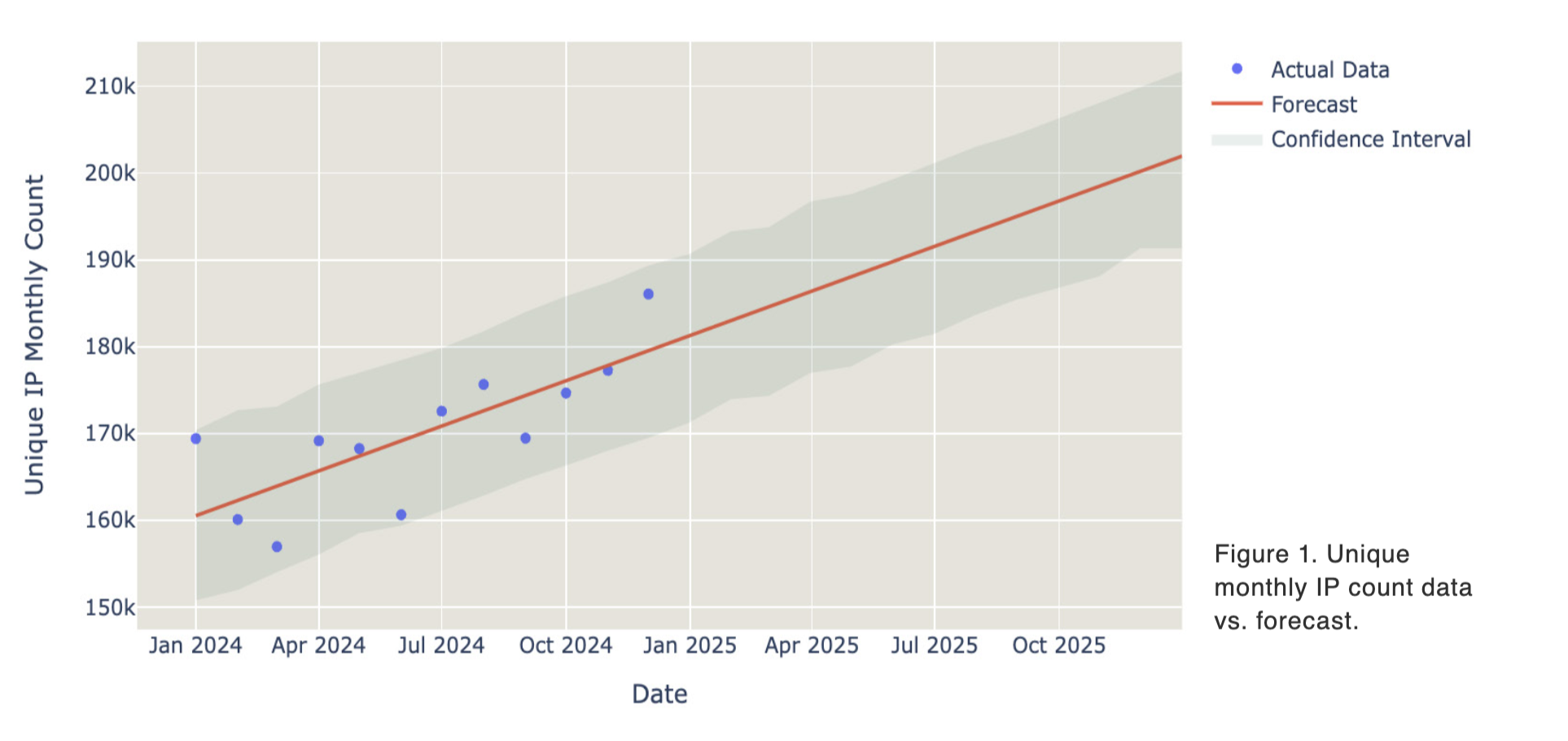
More critically, the fact that many organizations can’t accurately gauge their ICS/OT exposure highlights a larger issue: most enterprises still lack the visibility to fully understand what assets they own and the level of risk those assets introduce. This was one of the central findings of the State of Cyber Risk and Exposure 2025 report, and it bears repeating—fewer than half of organizations continuously monitor their environments to identify at-risk assets, whether they’re traditional IT, IoT, or ICS/OT. Building a clear asset inventory and understanding exposure levels are foundational steps for pinpointing the risks that truly matter to your business. Without that visibility, it’s nearly impossible to prioritize or effectively manage cyber-physical risk.



