Stealer malware is thriving—especially Lumma and Risepro. These logs fuel ransomware, MFA bypass, and persistent access. It's $10 to compromise an account. Explore this and other insights the data reveals.
Don’t Be Tricked by Open Ports: Unmasking Hidden Cyber Dangers
Tags:


Open ports are foundational to network operations, allowing devices, services, and applications to communicate through data exchange. However, when these ports are left exposed or misconfigured, they can become prime targets for cyberattacks. This report explores the role of open ports in today’s threat landscape, focusing on threat detection, prevention, threat hunting, and incident response.
What are open ports?
Open ports are TCP or UDP endpoints configured to accept incoming network traffic. They are essential for enabling services such as:
- Web browsing: HTTP (Port 80), HTTPS (Port 443)
- File transfer: FTP (Port 21)
- Remote access: SSH (Port 22), Telnet (Port 23), RDP (Port 3389)
- Email delivery: SMTP (Port 25)
- Domain name resolution: DNS (Port 53)
All communication that happens over the internet is exchanged via ports. These virtual communication endpoints help computers—from your laptop to the cloud—understand what to do with internet-based traffic.
These ports support business-critical functionality, including remote troubleshooting by IT teams. However, they are often left open unintentionally, creating hidden vulnerabilities.
How do open ports work?
Every device that connects to the internet is given a unique identifier (IP address). Each IP address contains two kinds of ports, TCP and UDP. Think of these as doors that can receive information. There are lots of these doors—up to 65,535 of each for any given IP address. One port sends email traffic to your inbox (either a POP3, IMAP, or SMTP port) and another (a web server port) handles website traffic and so on.
Ports need to be open so they can receive information or packets of data and for everything to work smoothly. If a port is closed it will reject or ignore packets. It’s like not answering the door when someone comes knocking.
Why are open ports a security risk?
Open ports can act as unintended entry points for attackers. Threat Actors can use vulnerable, unpatched, misconfigured, or infected underlying services in conjunction with open ports to move laterally across the network and gain access to sensitive data. When not properly secured, open ports may expose:
- Misconfigured or outdated services that can be exploited.
- Wormable vulnerabilities, such as SMB (Port 445), which was targeted by malware like WannaCry.
- Unsecured remote access protocols like SSH or RDP that enable unauthorized control.
Threat actors frequently scan the internet using tools like Shodan or masscan to find open, exploitable ports, making exposed systems easy initial targets
Studies have shown that open ports pose a high security risk:
- A study by Marsh McLennan compared the security performance data of thousands of organizations that experienced cybersecurity incidents against those that did not and found that open ports are strongly correlated with the risk of cyberattacks.
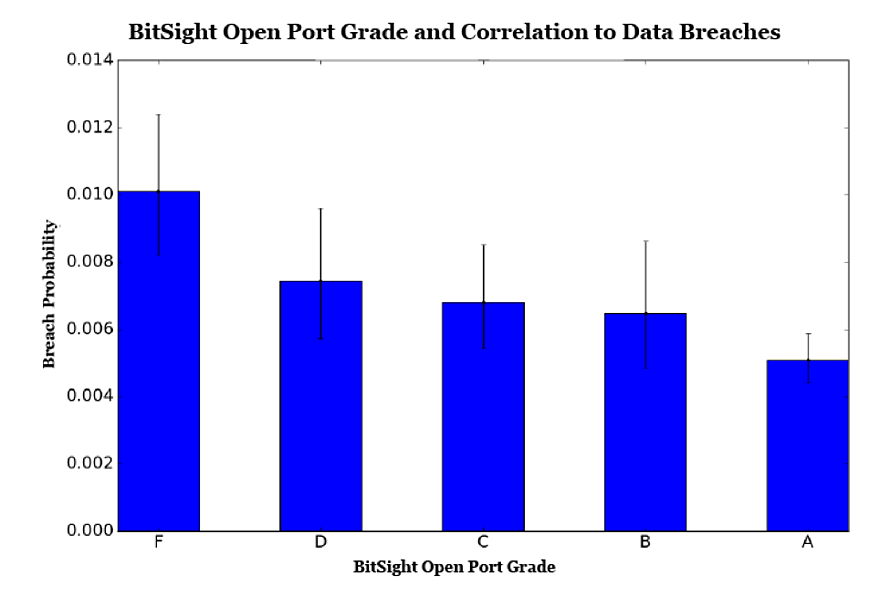
- Reinforcing these findings, Bitsight researchers found that organizations with an open port grade of F are more than twice as likely to experience a breach as companies with an A grade. If Bitsight can see this information, that means cyber criminals can too.
Monitoring and prevention strategies
Effective management of open ports requires visibility, control, and collaboration beyond the enterprise perimeter:
- Conduct regular scans using tools such as Nmap or Zmap to identify open or misconfigured ports, and use traffic analysis tools like Wireshark to detect anomalies.
- Disable unused ports and services to minimize the attack surface and limit potential entry points.
- Restrict external exposure so that only essential services are accessible from the internet.
- Implement firewalls and intrusion detection/prevention systems (IDS/IPS) continuously monitor for unusual or malicious activity.
- Extend monitoring to third parties. Open or misconfigured ports within a vendor’s environment can pose significant risks to your organization. Use external scanning and security ratings tools to identify exposed services across your vendor ecosystem.
- Establish a remediation workflow. When issues are detected, communicate findings to affected vendors, verify corrective actions, and track resolution through your third-party risk management process.
By extending monitoring and remediation efforts to include vendors and partners, organizations gain a more complete view of their external attack surface and can act quickly to reduce systemic exposure
Threat hunting and incident response
Open ports often serve as the entry point in early-stage attacks. Incorporate them into detection and response workflows:
- Monitor for scanning behavior or anomalies related to specific ports, which may signal reconnaissance activity
- During a security incident, identify which ports were used or exploited to guide containment and remediation
- Combine endpoint and network telemetry to trace attacker movements and detect lateral spread within the environment
Best practices for discovering and securing open ports
To reduce your organization’s exposure:
- Understand and scan your external attack surface so that you can visualize your digital ecosystem
- Enable multi-factor authentication on all services accessed remotely.
- Regularly patch and update systems and applications exposed via open ports.
- Audit physical access, especially to Ethernet or console ports in sensitive areas.
- Continuously monitor and audit your attack surface, particularly after infrastructure or service changes.
- Grade your open port performance as an important cybersecurity KPI
What can you do to fix open ports?
CIS Critical Security Controls list open ports as a substantial network risk and recommends that only those ports with a valid business requirement—such as those associated with a legitimate service—are left open or running on a system.
System administrators can use port scanners or vulnerability scanners to discover and close open ports that are exchanging information on their networks. However, closing open ports requires knowing which ports are required by the services running on a network. Some of these are universal—for example, port 80 is the port for web traffic (HTTP). Others are reserved by specific services. Many scanning tools provide information about whether the open port is in use.
Once the administrator knows which ports must remain open, they can conduct a scan to identify open ports that might be exposing their systems to cyberattacks. If a port is open and not associated with any known service on the network, it should be closed immediately.
Conclusion
Open ports are both essential and risky. When left unmanaged, they can expose your organization to threats ranging from opportunistic malware to targeted attacks. By incorporating cyber threat intelligence into ongoing monitoring, detection, and response, organizations can turn a common vulnerability into a managed security control and significantly improve their overall security posture.
How does Bitsight help?
Bitsight’s Cyber Threat Intelligence helps organizations manage open port risks with contextual, actionable insights. This includes:
External attack surface visibility
Bitsight continuously monitors the public-facing infrastructure of organizations, including open ports. It identifies which services are exposed and flags misconfigurations or risky behaviors, giving security teams real-time awareness of their external footprint.
Threat actor and botnet attribution
Bitsight correlates port-based threats with known threat actors, botnets, and malware campaigns. For example, if an exposed RDP port is being scanned or exploited, Bitsight can help identify whether it is linked to a known ransomware group or a commodity botnet, allowing teams to prioritize based on risk.
Dark web monitoring and threat chatter
Bitsight’s deep and dark web intelligence collection detects when open ports or services are being discussed, listed, or targeted in underground forums. This provides added context to scanning activity and supports proactive defense.
Threat alerts and early warnings
Bitsight delivers automated alerts when critical ports such as SMB, RDP, or Telnet are exposed or actively being scanned. These alerts are mapped to real-world threat actor tactics, techniques, and procedures, enabling faster triage and response.
Third-party risk insights
Organizations may inherit risk from partners and suppliers. Bitsight extends visibility into the cybersecurity posture of vendors, highlighting open port exposures and helping reduce risk across the supply chain.



