Petya / NotPetya: What Security Diligence Tells Us
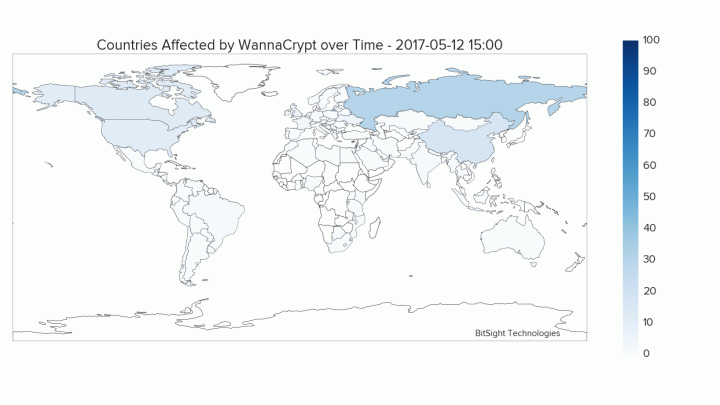
There are many details of yesterday’s ransomware attack are still being worked out, and its impact is still being assessed. Yet, there are many security diligence steps organizations can take to reduce exposure to these types of attacks. Below are best practices security and risk teams should be aware of, and implications for organizations who fall behind.
Bitsight recommendations
1. Assess Geographic Breakdown & Product Reliance In Your Business Ecosystem
Reports indicate that NotPetya may first have spread through a software update of M.E.Doc, an accounting product used by many Ukrainian companies. The update process was allegedly hijacked to drop the malware, but the company has denied that it was the initial infection vector in a Facebook post. As illustrated with recent cyberattacks on Dyn and Cloudflare, an outage or compromise of one product can affect thousands of organizations.
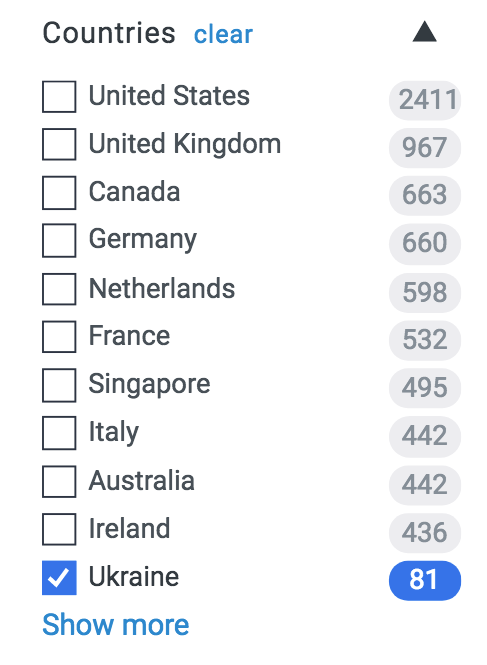
Using Bitsight, organizations can identify organizations in their business ecosystem that are tied to a potentially risky product or service. Once identified, organizations can invite their third parties to review their security posture, and investigate and remediate any security issues.
Additionally, since companies with a presence in Ukraine were particularly hit, users can leverage the country filter in Bitsight to search for any organizations with IP space in the country and reach out.
2. Close Any Ports That Are Left Unnecessarily Open
WannaCry spread through ports that were left unnecessarily open. Given the spread of NotPetya, organizations should disable SMBv1 block outside access to ports 137, 138, 139 and 445.
A Bitsight study showed that out of thousands of companies studied, 60 percent of breached organizations had 10 or more ports susceptible to unauthorized use.
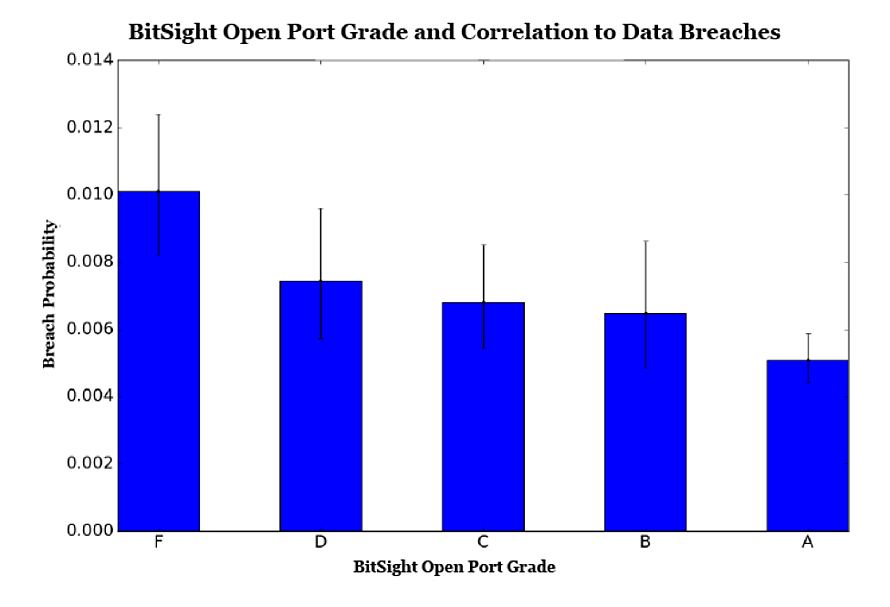
We recently strengthened that finding, discovering that organizations with an “F” as their Bitsight Open Port (meaning many risky services are exposed to the internet) grade are more than twice as likely to experience a breach than companies with an “A.”
3. Ensure Devices on a Network's Endpoint Are Updated with the Latest OS Version
The exact affected versions of Windows operating systems from yesterday’s attack are not yet known, but as with the WannaCry attack, installing the latest OS version can often protect against major exploits. Bitsight researchers recently found that thousands of organizations are running more than half of their computers on outdated operating systems, nearly tripling their chances of experiencing a publicly disclosed breach.
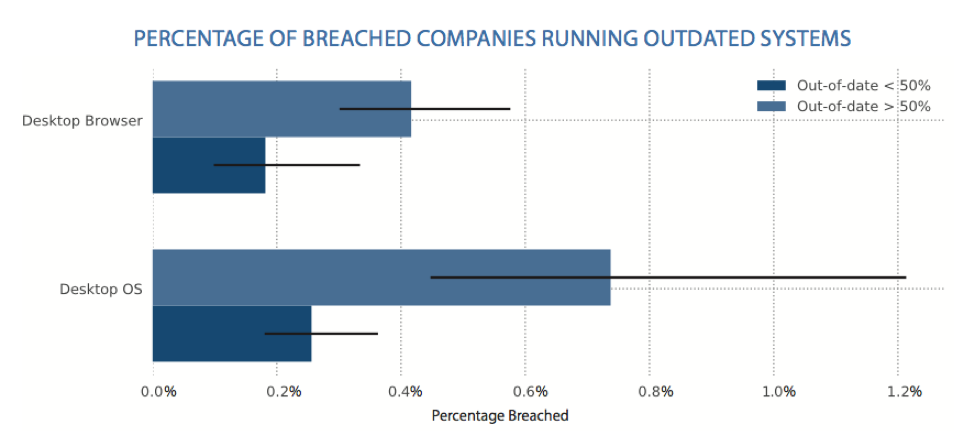
Given the correlation between outdated systems and data breaches, organizations should consider taking a proactive approach to securing their networks before these vulnerabilities are exploited by cyber criminals. They should also be aware of the third parties with access to their data and whether they fall behind in their patching processes. As the use of personal tablets, mobile devices, and laptops continues to grow, companies without robust endpoint security controls or mature third party risk management programs will likely be exposed to more cyber attacks in the future.


