New! The Security Ratings report is now the Executive Report. Request your report to see enhanced analysis such as your rating, likelihood of ransomware incidents, and likelihood of data breach incidents.
Bitsight Research Explores A Risk Frequently Ignored: Critical Updates
Tags:

Last month, thousands of computers across the world were infected by a strain of ransomware known as WannaCry. Estimates show that this massive attack impacted over 300,000 computers across banks, hospitals, telecommunications services, train stations, and numerous other critical services. Months before this attack, Microsoft had released a patch of all Server Message Block (SMB) vulnerabilities, including EternalBlue, which researchers believe is one of the vulnerabilities that criminals exploited to carry out the attack. Despite the available patch, it appears that many companies neglected to install the critical update (MS17-010) from Microsoft prior to the attack.

Bitsight researchers examined more than 35,000 companies from over 20 industries across the world to explore the use of outdated operating systems and outdated Internet browsers over the last year and their correlation to data breaches. The results demonstrate the importance for companies to establish robust security controls and continuously monitor the number of outdated endpoints on the networks of their trusted third parties with access to sensitive data.
Thousands of Companies Are Running Outdated Systems, Increasing Their Likelihood of Experiencing a Breach
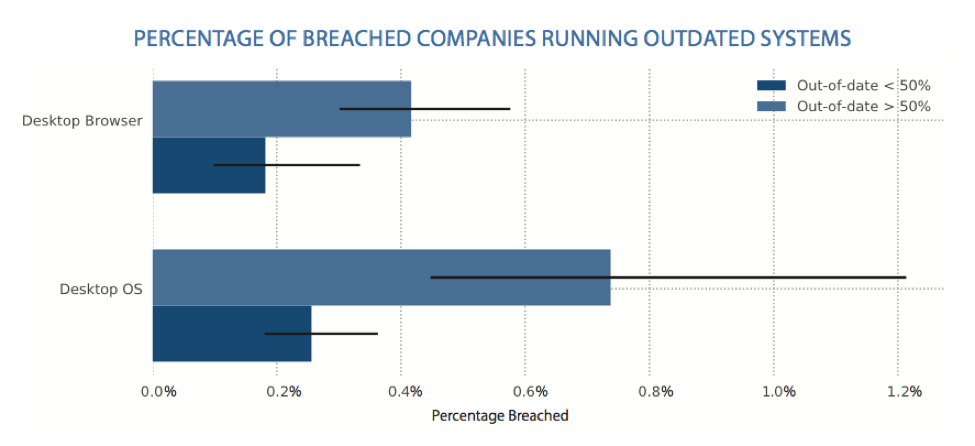
From the companies that Bitsight researchers studied, they found that thousands of them were running at least 50 percent of their computers on older Internet browsers, making them more than twice as likely to experience a publicly disclosed breach. Researchers also found that thousands of organizations also had more than 50 percent of their computers running outdated versions of an operating system, tripling their chances of experiencing a publicly disclosed breach.
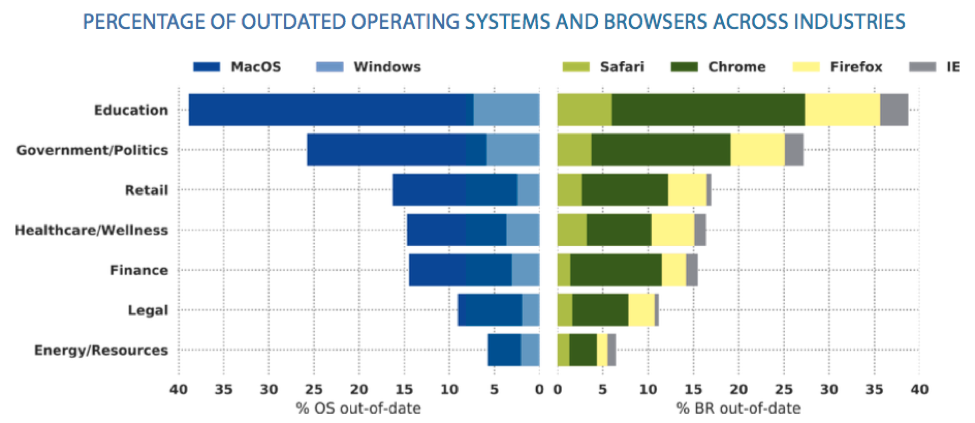
Industry Performance
Bitsight researchers examined seven major industries: Education, Government, Retail, Healthcare, Finance, Legal, and Energy. Among these industries, Education and Government had the highest usage rate of outdated operating systems and Internet browsers. In fact, more than 25 percent of the computers used in the Government sector (including state and local government) were running outdated versions of MacOS or Windows operating systems. The report also found that more than 120 companies in the Energy sector were running out-of-date or unsupported operating systems and hundreds of them were observed to have greater than 33 percent of Internet browsers out-of-date.
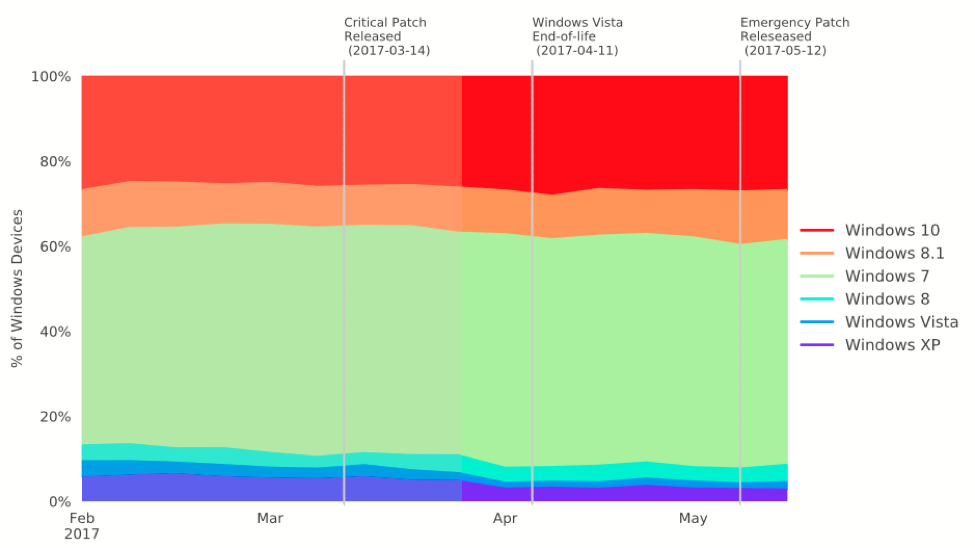
How Much Time Do Companies Take to Update Their Systems?
When large technology companies such as Google, Apple, and Microsoft release software updates, they not only provide patches for security vulnerabilities, but they also help end-users to protect their systems against cyber attacks. Despite the known value of maintaining updated systems, Bitsight researchers found that organizations take months to upgrade to the latest software versions. Nearly half of the Windows computers studied in this report were running Windows 7 instead of Windows 10. More surprisingly is that nearly 20 percent of these Windows computers were running Windows XP or Vista, which Microsoft no longer supports.
Bitsight’s latest Insights report has found that thousands of companies are using outdated operating systems and Internet browsers, which increases their chances of experiencing a publicly disclosed data breach. Companies without robust endpoint security controls or mature third party risk management programs will likely be exposed to more cyber attacks in the future.
Recommendations
Below are recommendations for organizations to approach cybersecurity with a sense of urgency to secure their networks and collaborate with third and fourth parties to protect their sensitive data.
- Apply critical system updates and monitor your attack surface from the outside. Although it may be difficult for large companies to update every computer on their networks, IT teams should at least examine whether any computers on their networks are using outdated versions of operating systems. This can be done from outside the network without solely relying on penetration tests or network scans.
- Update Internet browsers. Some browsers offer automatic updates, but because employees across the company may use different browsers to access the Internet, information security teams cannot solely rely on these automated features. Instead, they must proactively monitor their network and consider installing updates on systems with outdated browsers.
- Continuously monitor and evaluate your third parties. Organizations should confirm that their data is not managed by third parties with outdated endpoints connected to their network. If organizations cannot determine whether their critical vendors are using outdated operating systems or Internet browsers, they should consider restricting the vendor’s access to the company’s sensitive data so that the company’s data is not at risk in the event of a breach.
- Understand the business impact of cybersecurity decisions. Cybersecurity should be an important part of business discussions with the board of directors and senior executives. Knowing whether a potential vendor is using outdated systems can help the organization better understand the vendor and the level of risk that they present to the business.


