Ransomware, breach sharing, stealer logs, credentials, and cards. What has shifted and how to respond.
Shadow IT: The Haunting Inside Your Network
Tags:


According to Bitsight TRACE’s 2025 State of the Underground report, the most exposed devices tied to critical vulnerabilities were found in the United States, and the most affected sectors included Information (telecom, IT) and Professional, Scientific, and Technical Services (including security and software vendors).
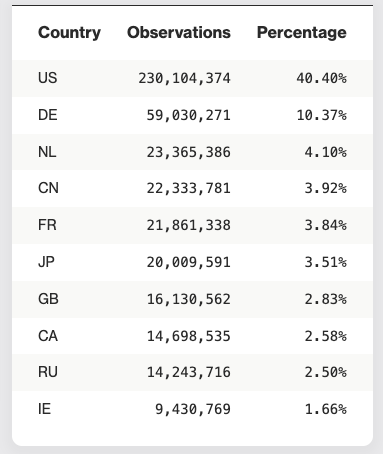
Even the most security-conscious industries are struggling to maintain visibility over exposed assets, especially those introduced by third parties. As of this blog’s publication, Bitsight threat research has identified over 230 million exposures in the U.S. alone, representing more than 40% of all exposures worldwide. That’s a staggering number, one that should stop any security leader in their tracks. How many of those 230 million exposures are you at risk for? Are your vendors at risk for? Are their vendors at risk?
In a recent study, Bitsight’s Dr. Ben Edwards predicted up to 59,000 new CVEs would be published in 2025. But with the NVD (NIST’s vulnerability database) still struggling to keep up, many of these vulnerabilities aren’t being fully analyzed thus creating a growing intelligence gap. As the volume of CVEs rises, the odds increase that a truly dangerous vulnerability slips through the cracks, especially on untracked, unmanaged, or vendor-owned assets. In other words, Shadow IT.
Without visibility into your full digital footprint, including assets you didn’t know existed, high-risk vulnerabilities can sit unpatched and exploited. You can only patch what you are aware of.
A simple analogy
Imagine your parents know every toy in your room. But one day, your friend brings a toy and hides it under your bed. That toy might be fun, it could also be sharp or dangerous and no one knows it’s there to check.
That’s what Shadow IT is like: unauthorized tech that’s introduced without oversight. And when it’s your vendors—or even their vendors—bringing it in, the risk becomes harder to control and nearly impossible to see.
What is third- and fourth-party shadow IT?
Shadow IT refers to devices, apps, cloud services, or infrastructure spun up without IT’s knowledge or approval. This includes:
- Marketing microsites hosted on your subdomains
- Dev or staging environments containing live data
- Public cloud buckets or SaaS portals using your brand
- DNS delegations managed by vendors
While third-party Shadow IT involves assets introduced by your immediate vendors, fourth-party Shadow IT refers to assets introduced by your vendors’ vendors—integrators, cloud hosts, subcontractors—often outside your direct line of sight. Those assets can still carry your domain, your logo, or your data.
These assets might not appear in any inventory, but they’re visible to attackers, indexable by search engines, and exploitable like any other exposed infrastructure.
Examples of shadow IT that could live on your network:
- Messaging apps used on corporate-owned devices (Snapchat, WhatsApp, Slack, Facebook Messenger, Signal, Skype)
- Physical devices not monitored by IT but connected to your network, including:
- Personal smartphones
- Laptops (we will hit on more later but this can include your family’s devices connected to your home internet while you’re working from home)
- Flash drives
- Cloud storage (Dropbox, Google Drive, AWS)
- Workplace efficiency apps meant to increase productivity (Trello, Airtable, Wrike, Monday.com, etc.)
- And more...
Why shadow IT happens
Shadow IT, (first, third, or fourth party), is usually not malicious. It’s driven by:
- The need to move fast
- Bypassing lengthy approval or onboarding processes
- Vendors building “quick fixes” or campaign infrastructure without oversight
But lack of visibility is lack of control. And when it comes to fourth-party risk, you may not even know the vendor exists, let alone what they’ve exposed on your behalf.
Real-world risks of Shadow IT
- Subdomain takeovers: If a vendor (or their vendor) forgets to decommission a hosted microsite, attackers can hijack it under your brand.
- Data exposure: Dev, staging, or storage environments can leak sensitive customer information.
- Malware hosting: Dormant vendor assets can be used to serve phishing or malware from trusted domains.
- Compliance failures: Regulatory bodies like GDPR, DORA, and NIS2 don’t differentiate between 1st-, 3rd-, or 4th-party when it comes to responsibility for exposed data.
Example:
A fintech firm hired a digital marketing vendor for a three-month campaign. That vendor outsourced hosting to another provider (a 4th party), spinning up a microsite under securepromo.finbrand.com. The campaign ended. The 4th-party host kept the site live (intentionally or unintentionally). Months later, it was quietly compromised and redirected users to a phishing site mimicking the fintech's login portal.
IT never knew the asset, or the 4th party, existed. But the brand and customer damage was real.
This is why it is important to monitor your company, your vendors, and your vendors’ vendors. The attack surface is vast, ensure you are protected.
How Bitsight helps: Exposure Management in action
Manual inventories and static assessments can’t catch vendor- or 4th-party Shadow IT. You need continuous, outside-in visibility that spans your entire digital supply chain.
That’s where Bitsight Exposure Management delivers. Combining the strengths of External Attack Surface Management (EASM) and Third-Party Risk Management (TPRM), Bitsight provides the only solution that helps you:
- Discover unknown assets, including those introduced by third and fourth parties
- Trace ownership across the digital supply chain
- Assess risk for each asset and prioritize what matters
- Monitor changes to third- and fourth-party infrastructure in real time
- Proactively respond to Shadow IT before attackers can exploit it
Best practices to reduce third- and fourth-party Shadow IT
- Require asset disclosure: Ensure vendors and their subcontractors disclose all external-facing assets tied to your environment.
- Enforce contractual visibility: Mandate security and asset transparency throughout the vendor ecosystem.
- Integrate EASM + TPRM: Use Bitsight Exposure Management to monitor brand-related assets, even when you don’t directly control them.
- Audit delegated DNS: Minimize and review subdomain assignments, especially those handed off to third parties.
- Educate vendors and staff: Reinforce that even “temporary” assets can introduce permanent risk.
- Offboard with discipline: Include asset teardown and DNS cleanup in every vendor and campaign offboarding checklist.
The bottom line
Shadow IT isn’t just an internal challenge anymore. It’s an ecosystem-wide risk that includes your third and fourth parties, and it’s being actively exploited.
With Bitsight Exposure Management, you get the visibility and control needed to detect, assess, and mitigate risk across the entire digital footprint, not just what you own, but what’s tied to your brand.
Don’t let hidden infrastructure become your next breach. Shine a light on Shadow IT, wherever it lives.
Shadow IT FAQs
Shadow IT can refer to a number of different IT applications, cloud software, outside technologies, and devices (laptop, smartphone, etc.) that are connected to an organization’s network without the knowledge of the IT department. These non-approved technologies aren’t vetted through the usual IT vendor onboarding process, which means they might have security standards that are below your organization’s normal risk-thresholds.
It can be hard to believe that your IT department would miss critical vendors being given access to your network, but research shows that the average organization houses over 900 unknown cloud services, and 80% of workers surveyed admit to using SaaS applications at work without getting approval from IT.
It might be hard to believe in the danger of shadow IT if security managers aren’t constantly talking about it. In reality, when the sources of data breaches are not always made public, it can be because security teams are embarrassed to admit to having shadow IT. Major data breaches, like SolarWinds, are impacting large numbers of companies because IT departments weren’t aware that SolarWinds software was present because it had been downloaded by an employee for free.
Shadow IT is there, and it’s worth your worrying about. With today’s remote office environment, employees around the world are accessing their organization's network from home internet points. This means that anyone else using that same internet is also connected to the company’s network, which dramatically expands the attack surface for bad actors to infiltrate.
Your employees most likely are not trying to welcome bad actors onto your network by choosing to bypass IT protocols. In reality, the most common reason for shadow IT on your network is because your employees are trying to work more efficiently, and are trying out a new service or cloud provider. Sometimes the team leaders don’t realize even the seemingly smaller integrations still need to be run through IT, and other times the need is urgent and employees don’t want to wait for the IT audit to be completed.
In other instances, employees might be very conscious of their cybersecurity decisions on the company network, but don’t know how using a remote internet connection or using personal devices for work could impact the company. Including shadow IT in your employee cybersecurity training is the best way to educate your workforce about the potential danger of their decisions.
Protecting your organization from bad actors requires a monitoring technique that scans for shadow IT. Manual processes or tools requiring oversight from a member of the IT department can be time consuming, and can fail to monitor every corner of your network.
Attack Surface Analytics from Bitsight
With Bitsight for Security Performance Management, customers are given access to Attack Surface Analytics. Attack Surface Analytics specifically helps program managers discover hidden assets and cloud instances on your network. Bitsight then will assess the discovered areas of shadow IT for their inherent risk to your business, and then help bring them into line with your corporate security policies.
If you’re curious about what shadow IT is lurking in your network, you can request an Attack Surface Analytics report with Bitsight today.



