Stealer malware is thriving—especially Lumma and Risepro. These logs fuel ransomware, MFA bypass, and persistent access. It's $10 to compromise an account. Explore this and other insights the data reveals.
From Ransomware to Exposed ATMs: Top 4 Cyber Threats to the Financial Sector


Overview of threats facing the Financial sector
The financial sector remains one of the most targeted industries for cybercriminals and nation-state actors due to the sensitivity of customer data, the high value of financial transactions, and the critical role these institutions play in global stability.
Bitsight’s 2025 State of the Underground report found that underground markets listed nearly 14.5 million compromised credit cards in 2024, representing a 20% increase over 2023. This growth was driven entirely by a surge in US-issued cards. While listings for non-US cards actually declined by 1.6 million, US card listings rose by 4.5 million, making up over 80% of all compromised card data posted in underground forums and markets.
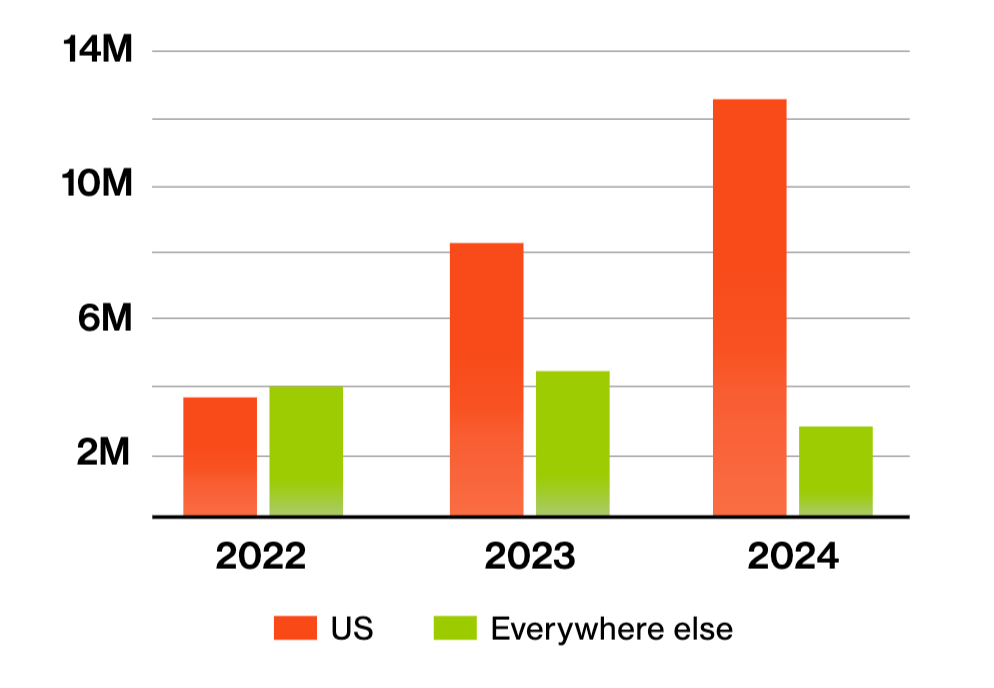
This shift highlights a growing focus by threat actors on US financial data and signals increased risk for US-based financial institutions and consumers.
In our TRACE REPORT: Researching Exposed Cameras in the Wild, we identified over 40,000 exposed internet-connected cameras globally. Some of these were discovered inside banks and near ATM sites. In one case, a live feed showed a camera positioned directly over an ATM keypad:

This exposure lowers the barrier for fraud. Traditionally, criminals rely on card skimmers, keypad overlays, or hidden pinhole cameras. With exposed ATM cameras, adversaries can remotely capture PINs or surveil ATM usage without leveraging hardware. According to Bitsight Threat Research, this provides opportunities for both remote fraud and physical follow-on attacks.
Top 4 threats to the Financial sector and MITRE ATT&CK mappings
1. Ransomware
Ransomware groups have been observed by threat researchers as targeting financial institutions across the United States, Germany, India, and Taiwan.
TTPs:
- Initial Access: Phishing (T1566.001), exploitation of public-facing apps (T1190), and use of valid accounts (T1078).
- Execution: PowerShell (T1059.001), Command and Scripting Interpreter (T1059).
- Persistence: Scheduled Task/Job (T1053), Registry Run Keys (T1547.001).
- Privilege Escalation: OS Credential Dumping via Mimikatz (T1003.001).
- Exfiltration and Impact: Exfiltration Over Web Services (T1567.002), Data Encrypted for Impact (T1486), Exfiltration to Cloud Storage (T1567.002).
2. Distributed Denial of Service (DDoS)
According to Bitsight Threat Research, financial services remain the most targeted industry for Distributed Denial of Service (DDoS) attacks. Attackers are increasingly combining volumetric floods, application-layer disruptions, and supply-chain exploitation.
TTPs:
- Botnet Use: Exploitation of IoT devices (T1498.001 – Direct Network Flood).
- Application-Layer Attacks: HTTP Flooding (T1499.004).
- Infrastructure Abuse: Reflection/Amplification using DNS/NTP (T1498.002).
- Supply-Chain Targeting: Resource Hijacking of third-party service providers (T1496).
3. Phishing and social engineering
Phishing continues to drive compromises, especially in Asia-Pacific and Japan (APJ) where digital banking adoption is high. A new variant, QR code phishing (Quishing), redirects victims to credential harvesting sites.
TTPs:
- Delivery: Spearphishing Link (T1566.002), Spearphishing Attachment (T1566.001).
- Credential Harvesting: Input Capture (T1056.001) and Web Services Credential Capture (T1556).
- Domain Abuse: DNS Spoofing and Homoglyph Domains (T1584.001 – Acquire Infrastructure: Domains).
- Bypassing MFA: Valid Accounts (T1078).
4. Exposed cameras and IoT exploitation
According to Bitsight TRACE, more than 40,000 exposed cameras stream unprotected feeds, including inside financial institutions and ATMs. These IoT exposures can serve as both direct fraud enablers (e.g., ATM PIN theft) and indirect infrastructure risks (e.g., botnet recruitment for DDoS).
TTPs:
- Reconnaissance: Gather Victim Org Information – Security Posture (T1591.004).
- Surveillance: Capture Video from Information Repositories (T1113).
- Fraud Enablement: Use of exposed ATM cameras for PIN theft (T1056.001 – Input Capture).
- Botnet Recruitment: Exploitation of Vulnerable Services (T1190) to conscript IoT cameras into botnets for DDoS (T1498).
Why do IoT devices matter?
For banks, financial services, and fintechs, IoT devices create both cyber and physical security risks:
- Exposed cameras at ATMs: Adversaries can capture customer PINs without installing physical skimmers.
- Smart building devices: Connected HVAC, lighting, or badge systems can be entry points for attackers to move into critical networks.
- IoT devices in data centers: Poorly secured cameras or sensors can be compromised and conscripted into botnets for DDoS attacks.
Threat Actors
- Nation-State: Chinese APT activity represents ~3% of financial attacks, primarily espionage driven.
- Cybercriminal: Motivated by profit, leveraging ransomware, phishing, and ATM fraud.
- Hacktivists: Disruptive DDoS campaigns aligned with political or social agendas.
Recommendations for Financial institutions
Threat Monitoring
Deploy continuous monitoring for C2 beaconing (T1071), unusual API calls (T1071.001), and abnormal authentication patterns (T1078).
Threat Prevention
- Harden IoT devices by changing default credentials (T1078 Mitigation).
- Apply strict patch management for exposed services (T1190 Mitigation).
- Enforce phishing-resistant MFA.
Threat Hunting
- Hunt for persistence mechanisms such as Scheduled Tasks (T1053) and Registry Keys (T1547.001).
- Search for suspicious use of PowerShell or WMI (T1059).
- Identify anomalous outbound traffic volumes indicating exfiltration (T1041).
Incident Response
- Prepare playbooks for ransomware scenarios (Data Encrypted for Impact – T1486).
- Test DDoS response readiness, including mitigation through cloud scrubbing services (T1499.004).
Conclusion
According to Bitsight Threat Research, the financial sector faces a growing range of multi-vector threats, ranging from ransomware and phishing to IoT exposures like ATM surveillance cameras. These risks are magnified by adversaries’ ability to chain TTPs across different attack surfaces, making layered defenses and proactive intelligence essential.
By mapping adversary activity to MITRE ATT&CK, defenders can prioritize detection engineering, improve hunt operations, and develop incident response playbooks that directly address observed TTPs.
Learn more about how you can stay ahead of attacks targeting the financial sector with Bitsight Pulse.



