Stealer malware is thriving—especially Lumma and Risepro. These logs fuel ransomware, MFA bypass, and persistent access. It's $10 to compromise an account. Explore this and other insights the data reveals.
The Rise of Acreed Infostealer in the Post-LummaC2 Threat Landscape


Acreed, a new malware-as-a-service (MaaS) platform, appears to have taken the top spot in the infostealer ecosystem. We suspect this is due to the takedown of Lumma Stealer (LummaC2) in May 2025. In just its first week, Acreed was observed uploading over 4,000 stolen credential logs to a dark web Russian Market.
Acreed on the rise
In March 2025, Bitsight observed no activity from Acreed on dark web marketplaces. By April, that number rose to 50 credential logs on prominent Russian dark web markets, and by May, their activity increased to 864. By June, that number surged to more than 118,000 logs on prominent Russian dark web markets, according to Bitsight Threat Intelligence. This demonstrates Acreed’s rapid growth in the cyber threat community.
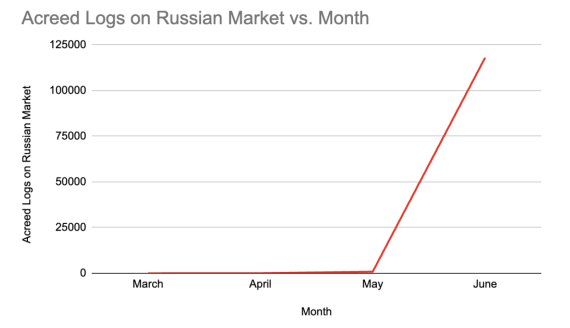
This surge comes on the heels of a global operation involving Bitsight TRACE, Microsoft’s Digital Crimes Unit, the U.S. Department of Justice, and others that dismantled LummaC2’s infrastructure and seized more than 2,300 malicious domains. The operation dealt a significant blow to one of the most prolific credential theft tools to date, LummaC2. LummaC2 was responsible for over 394,000 infections in just two months and 10 million total before its takedown. Although LummaC2 previously accounted for nearly 92% of credential theft logs on this marketplace, Acreed has quickly filled the void.
Numbers point to cybercriminals pivoting to Acreed, although this has not been definitively confirmed. With sophisticated data exfiltration capabilities, advanced evasion techniques, and the ability to hijack session tokens and bypass MFA, Acreed represents a potent and growing threat to enterprises worldwide.
Targeting SaaS and SSO credentials
Analysis of logs on the Russian market to include Acreed samples reveals that 61% of credentials are tied to software-as-a-service (SaaS) platforms, and 77% include single sign-on (SSO) credentials. These credentials are particularly dangerous because they can provide access to broad enterprise systems when compromised. In Russian Markets, the professional, scientific, and technical services sectors are among the most impacted (30%), followed by the information sector (28%).
Like other malware stealers, Acreed is engineered to exfiltrate high-value data, including saved passwords, cookies, cryptocurrency wallets, and credit card information. Its initial access vectors include phishing emails with malicious attachments or links, "ClickFix" attacks using fake CAPTCHAs, malvertising campaigns promoting cracked or premium software, and malicious tutorials on social platforms like YouTube and TikTok.
Once inside a system, Acreed extracts credentials from browsers such as Chrome, Edge, and Firefox. It hijacks session tokens from cloud platforms including Microsoft 365, Google, AWS, Azure, and Salesforce. This allows them to effectively bypass Multi-Factor Authentication (MFA) and allows the attackers to impersonate users without being detected. Additionally, Acreed collects host-level data including hardware IDs, IP addresses, and software inventories. Acreed employs advanced techniques to evade detection, such as JSON-based exfiltration and Dynamic Link Library (DLL) side-loading. These methods help the malware avoid traditional security measures.
Acreed’s expansive toolbox
Acreed’s impact goes beyond traditional credential theft. By hijacking session tokens, it bypasses MFA and enables lateral movement within enterprise networks. This can facilitate ransomware deployment or advanced persistent threat (APT) operations. A single compromised endpoint may lead to domain-wide breaches, affecting partners and clients.
The rapid emergence of Acreed in the wake of LummaC2's takedown underscores the resilience and adaptability of cybercriminal networks. As threat actors pivot to new tools, the infostealer landscape continues to evolve, placing persistent pressure on organizations to stay vigilant.
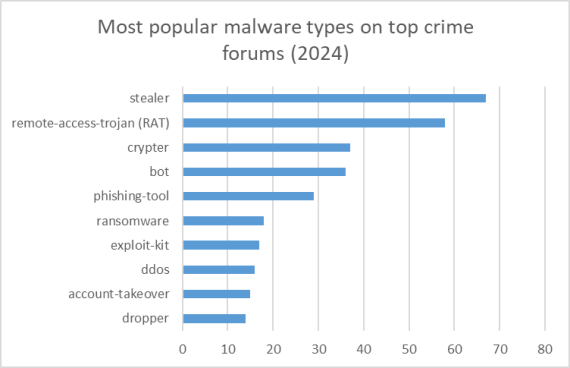
Because of Acreed’s expansive toolbox, organizations must not only implement robust preventative controls but also maintain continuous visibility into emerging threats to stay ahead. Bitsight plays a critical role in this effort, offering vendor risk assessments, proactive intelligence, dark web monitoring, and real-time alerts that empower security teams to detect, respond to, and recover from threats like Acreed before they escalate into full-scale breaches. In our 2025 State of the Underground report, Bitsight researchers addressed the most popular malware types on criminal forums, and it’s clear: infostealers aren’t going anywhere anytime soon.
How Bitsight helps defend against Acreed
Bitsight’s solutions are essential for mitigating threats like Acreed:
- Continuous Monitoring: Bitsight tracks emerging threats like Acreed in real-time, providing timely IOCs and threat intelligence.
- Dark Web Surveillance: We monitor dark web marketplaces for credentials tied to your organization, enabling swift response to breaches.
- Vulnerability and Risk Assessment: Bitsight identifies and prioritizes exploitable weaknesses to reduce attack surface.
- Security Ratings and Benchmarking: Our platform provides visibility into your cyber posture, helping you compare and improve relative to industry peers.
Recommended defensive actions:
- Prioritize Threat Monitoring
- Why: Acreed spreads quickly via phishing and malvertising. Early detection prevents escalation.
- Bitsight advantage: Real-time IOC tracking and alerting.
- Enhance Your Security Posture
- Why: MFA and software updates block common infection paths.
- Bitsight support: Vendor exposure analysis and posture benchmarking.
- Educate Users
- Why: Users are often tricked into downloading malware from fake ads and social media.
- CTI Insight: Bitsight provides tailored awareness content and briefings.
- Prepare and Test Incident Response Plans
- Why: Quick and informed response limits damage.
- Bitsight value: Real-world threat modeling and scenario planning.
To learn more about using Bitsight to stay ahead of infostealers, talk to our team or check out Bitsight Pulse, your personalized, AI-driven stream of cyber threat intelligence.



