Stealer malware is thriving—especially Lumma and Risepro. These logs fuel ransomware, MFA bypass, and persistent access. It's $10 to compromise an account. Explore this and other insights the data reveals.
The Business of Malware: Inside the MaaS Economy


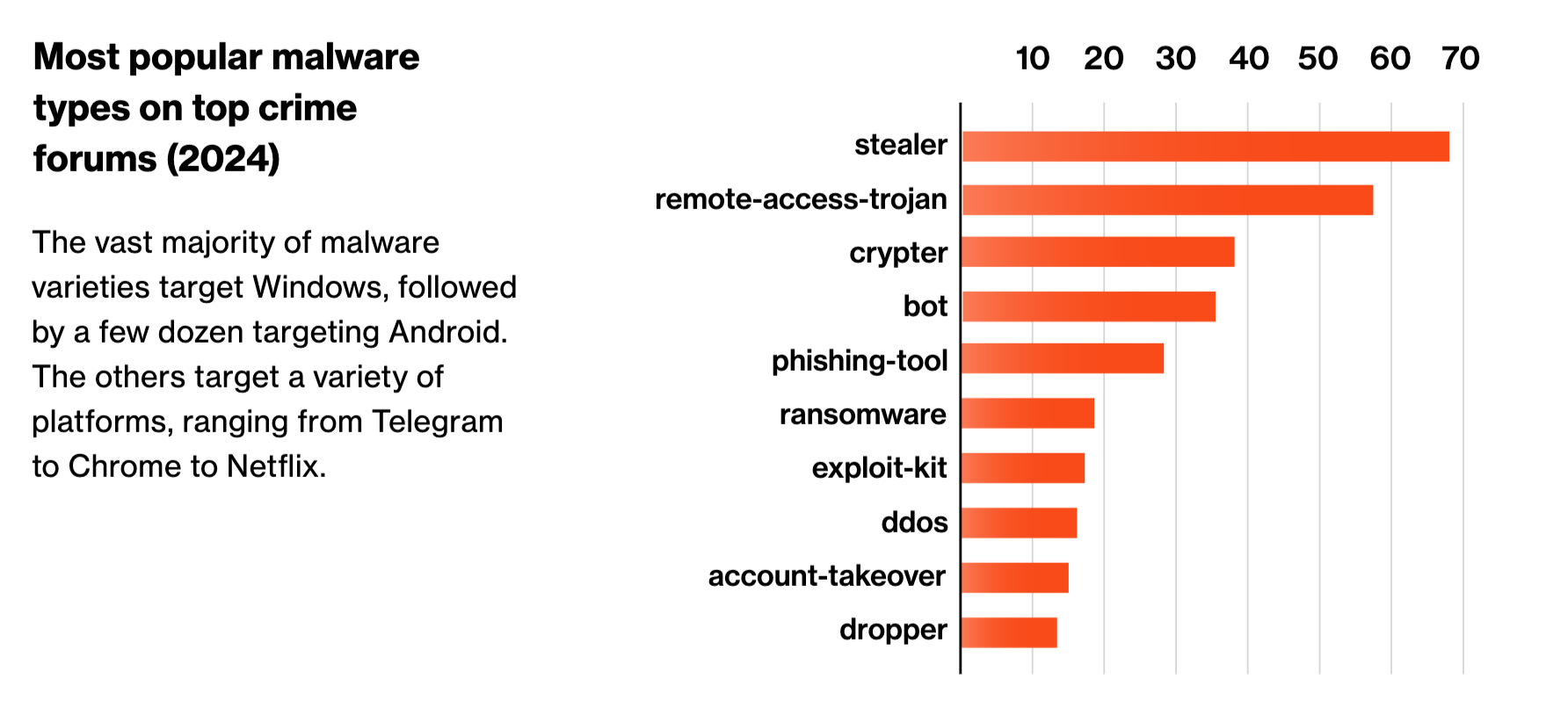
In our 2025 State of the Underground report, we found that 384 unique varieties of malware were sold across the top three criminal forums in 2024, a 10% increase from 349 in 2023, signifying an expansion in the underground malware marketplace. These figures reflect malware explicitly offered for sale (not shared freely), and each distinct version or naming variation is counted independently.
The malware market is diverse and evolving, with some stand-out players. For the past three years, stealers have consistently ranked as the most prevalent malware type sold, followed closely by Remote Access Trojans (RATs). The popularity of stealers is unsurprising given their ability to quickly monetize information from the targeted computer. According to Bitsight Threat Intelligence, the vast majority of these malicious tools target Windows systems, while a smaller segment focuses on Android. Other specialized malware variants have emerged targeting major tech platforms, underscoring how cybercriminals innovate to exploit new opportunity gaps.
In this blog post we’ll give an introduction to the Malware-as-a-Service economy, highlight some notable examples, and provide advice on how to protect your organization.
What is Malware-as-a-Service?
Malware‑as‑a‑Service (MaaS) replicates legitimate Software-as-a-Service (SaaS) in structure but serves the underground; developers offer pre-built malware (e.g. ransomware, spyware, trojans, adware) for rent or purchase. This allows threat actors, even those with minimal technical skills (derogatorily called “script kiddies”), to conduct complex cyberattacks without ever developing code. This model is particularly attractive to individuals with limited technical expertise, as it empowers them to launch effective cyberattacks, often with the ultimate goal of extorting victims through ransomware, without needing to develop or understand the underlying malware code.
Key features
Malware-as-a-Service (MaaS) platforms offer a broad range of malicious software tailored to different attack objectives. These include ransomware for extortion-based campaigns, trojans that enable remote access and system compromise, spyware for surveillance and data theft, and adware used to generate fraudulent ad revenue. Buyers can select specific malware types depending on their goals, such as stealing credentials, constructing botnets, or disrupting operations.
Much like legitimate Software-as-a-Service (SaaS) offerings, MaaS platforms typically operate on a subscription-based model with tiered pricing. Higher-tier subscriptions often include advanced features such as obfuscation modules to bypass detection, geofencing capabilities to target victims in specific regions, custom payload creation tools, and even 24/7 technical support and usage analytics.
These services are designed to be highly accessible. Many include user-friendly dashboards, admin consoles, and control panels that make it easy to launch and manage malware campaigns, no deep technical expertise required. This “plug-and-play” approach has effectively commercialized cybercrime and broadened the pool of potential threat actors.
Impact on organizations
By lowering technical barriers, MaaS has increased the scale and sophistication of cyber threats. As a result, less experienced attackers can mount high-impact campaigns rapidly. The resulting consequences for organizations include financial loss, operational disruption, reputational damage, and broader erosion of trust in digital systems.
Malware-as-a-Service examples
Ransomware-as-a-Service (RaaS)
Criminal groups rent out ransomware toolkits and infrastructure, often in exchange for a fixed fee or a share of ransom profits. RaaS models often come with affiliate portals, campaign builders, and technical support. In a recent post, we did a deep dive on RansomHub, a well known Ransomware-as-a-Service group.
Phishing-as-a-Service (PhaaS)
These services provide pre-built phishing kits, spoofed landing pages, and email distribution tools. Some even include backend dashboards to track victim engagement, making phishing scalable and cost-effective.
Notable MaaS threats
Lumma Stealer:
In May 2025, Bitsight, in close partnership with the FBI, Microsoft, and other global cybersecurity stakeholders, assisted in dismantling significant portions of the Lumma Stealer malware infrastructure. This disruption temporarily destabilized the malware’s operations and limited its reach across underground markets. However, Lumma has proven resilient. According to researchers at Trend Micro, the malware resurfaced within weeks of the takedown, with operators re-establishing their presence on Russian-language dark web forums.
What’s particularly notable is the tactical shift in infrastructure. Lumma operators are now relying on alternative service providers, including cloud and data center hosts based in Russia. One such provider was reportedly used extensively throughout June, allowing operators to regain operational capacity while attempting to stay under the radar of Western law enforcement. These adaptations suggest a flexible and determined threat actor group capable of pivoting quickly after disruption.
In terms of visibility, Bitsight Threat Intelligence observed over 98,000 mentions of Lumma Stealer across underground Russian forums in the past month alone. While this volume is considerably lower than the 3 million+ mentions tracked over the previous 12 months, it underscores the malware’s ongoing relevance and persistence in the underground economy, albeit at a potentially more focused or restricted scale.
Agent Tesla:
Agent Tesla is one of the most enduring Remote Access Trojans (RATs) currently circulating in the Malware-as-a-Service ecosystem. Written in .NET, this malware has been in operation for several years and remains widely available on criminal marketplaces due to its affordability, functionality, and low barrier to entry. Originally designed for data exfiltration, Agent Tesla is adept at capturing sensitive information such as credentials, keystrokes, clipboard contents, screenshots, and data from commonly used applications including web browsers, email clients, and VPN software.
Its effectiveness lies not only in its capabilities but also in its adaptability. Agent Tesla supports various exfiltration protocols: HTTP, SMTP, FTP, and even Telegram, allowing attackers to tailor campaigns to their infrastructure and evade detection. More recent variants incorporate persistent deployment techniques, ensuring continued access to compromised systems, as well as Tor-based anonymized C2 channels that enhance operational stealth.
Because of its plug-and-play usability and consistent development updates, Agent Tesla remains a top choice among low- to mid-level threat actors, who often pair it with phishing kits or exploit loaders to gain initial access to target environments.
Emotet:
First discovered in 2014, Emotet began as a banking Trojan targeting financial credentials through malicious macro-laden Word documents. Over time, it evolved into a powerful modular loader, enabling the delivery of secondary malware payloads such as TrickBot, a credential and data harvesting tool, and Ryuk, a ransomware variant used in large-scale enterprise extortion campaigns.
Emotet’s operational model aligned closely with the Infrastructure-as-a-Service (IaaS) framework. The malware’s developers rented access to their global botnet, allowing other threat actors to distribute their own payloads across compromised networks. According to Bitsight Threat Intelligence, at its height, Emotet’s infrastructure supported hundreds of thousands of infected devices worldwide and featured layered command-and-control (C2) architecture, encrypted payload delivery, and automated lateral movement capabilities, making it both resilient and highly effective.
In January 2021, a coordinated takedown effort led by Europol, the FBI, and authorities in Germany, the Netherlands, and Ukraine temporarily dismantled Emotet’s infrastructure. But the group behind Emotet adapted. By late 2022, the malware had reemerged with new tactics, improved obfuscation, and fresh partnerships in the criminal ecosystem reinforcing its place as one of the most durable and influential MaaS platforms in cybercrime history.
Conclusion
MaaS fundamentally reshapes the cybercrime landscape: it democratizes access to powerful offensive tools, enabling scalable, sophisticated attack campaigns. Addressing this threat requires investment in layered defenses, proactive threat intelligence, endpoint detection, and continuous user awareness training. As MaaS evolves, so too must organizational resilience strategies.
Recommended prevention actions
1. Strengthen credential security
- Use strong, unique passwords for each account—ideally, at least 12–16 characters with a mix of letters, numbers, and symbols.
- Implement multi-factor authentication (MFA) across all systems, especially for email, VPNs, and administrative accounts. MFA significantly reduces the risk from leaked or stolen credentials.
- Monitor for leaked credentials: Bitsight offers Cyber Threat Intelligence solutions to help protect you and your company from threats. We proactively scan the deep, dark, and clear web for stolen credentials, collecting 13.2B credentials with 1.23B unique URL-credential pairs in 2024.
2. Use endpoint protection and EDR
- Deploy Endpoint Detection and Response (EDR) tools that offer real-time detection and containment of suspicious activity.
3. Maintain secure backups
- Keep regular, encrypted backups of critical data—stored offline or in immutable cloud storage.
- Test backup restoration procedures regularly. Backups must be isolated from your network so they can’t be encrypted by attackers.
4. Train employees and simulate phishing
- Conduct security awareness training to help employees spot phishing emails, social engineering, and suspicious behavior.
- Run phishing simulations to identify weak points in your human firewall.
5. Implement network segmentation and least privilege
- Use network segmentation to limit lateral movement if an attacker gains access.
- Apply least privilege access—users should only have access to the data and systems necessary for their job.
6. Monitor and detect
- Use a platform to monitor for anomalies. Bitsight Cyber Threat intelligence can provide early warning of threats targeting your industry or assets.



