Discover how to safeguard your entire manufacturing footprint—from the shop floor to the supply chain and customer touchpoints—with real‑time insight into cyber risk and compliance. Click below to explore the white paper and unlock the visibility you need to proactively defend operations and protect innovation.
Supply Chains Under Siege: Top 3 Cyber Threats to Manufacturing


Audio Recap
In its 2025 State of the Underground report, Bitsight TRACE identified the manufacturing sector as the most targeted industry for the third consecutive year, accounting for 22% of the 4,853 cyberattacks where sector attribution was possible.
Manufacturing is the backbone of global supply chains, and when a cyberattack halts operations, even just briefly, the ripple effects can be enormous. Production delays, missed shipments, and service disruptions quickly cascade across industries. What’s more alarming is how invisible this dependency can be until an incident, like the COVID-19 pandemic, exposes just how fragile and interconnected these systems truly are.
One example was the outbreak-driven shutdowns in the U.S. meatpacking industry, which led to nationwide shortages of pork and other food products. At the same time, the global semiconductor industry faced a cascading crisis: factory closures, combined with shifting demand patterns, triggered a chip shortage that brought entire automotive production lines to a halt. Car manufacturers were forced to scale back or suspend operations, costing billions in lost output and delaying deliveries across the globe.
Why is manufacturing such a hot target?
The combination of operational technology (OT) systems, complex supplier networks, and high-value intellectual property makes manufacturing an especially attractive and high-impact target for threat actors. Manufacturing plants depend on uninterrupted operations; even short disruptions can cost millions. According to Siemens, unplanned downtime accounts for roughly 11% of annual revenue for Fortune 500 companies—about US $1.5 trillion worldwide. This makes them ripe targets for ransomware or extortion, where crippling operations can yield huge payoffs.
Increased attack surface due to digital transformation
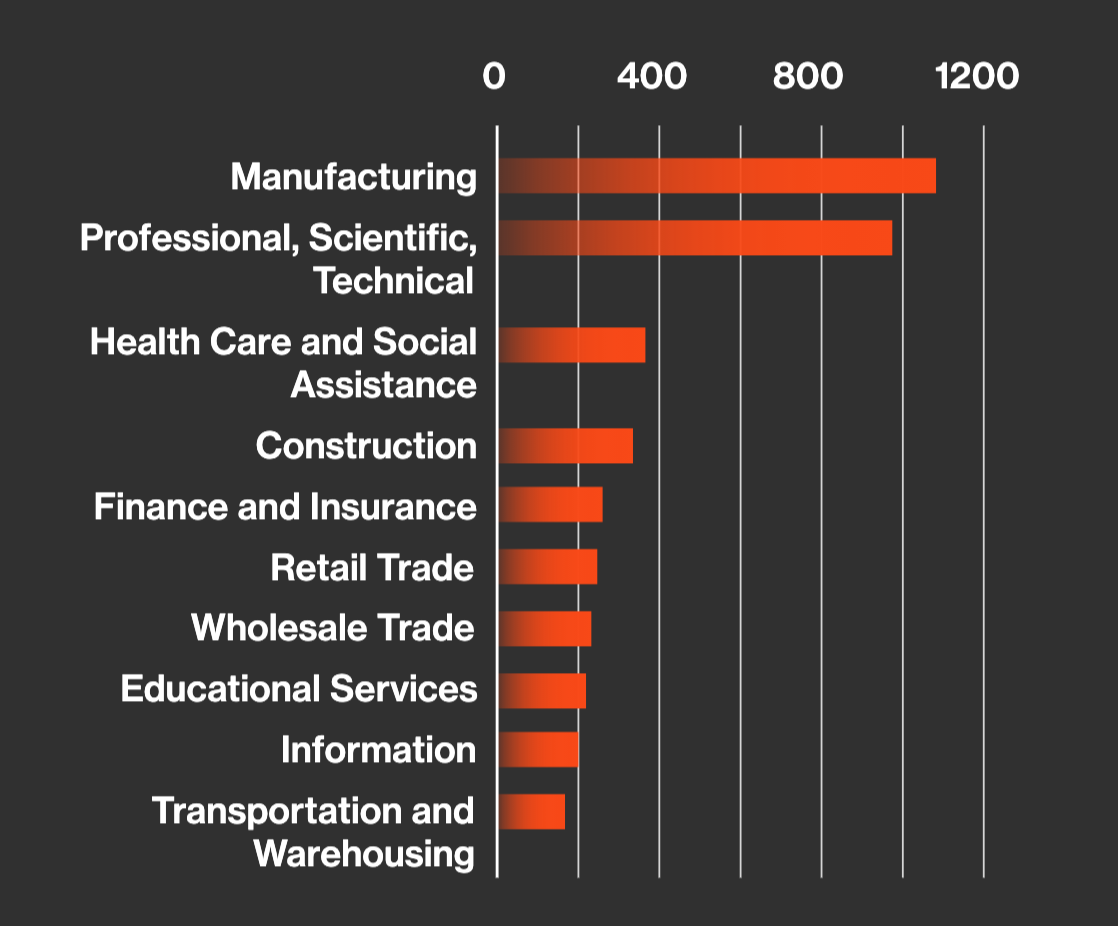
The manufacturing sector faces a growing threat landscape, particularly from nation-state actors. Chinese threat groups, for instance, are responsible for approximately 4% of all targeting activity against manufacturers, highlighting a meaningful risk of economic espionage and strategic disruption. As a critical component of national infrastructure, the sector remains a frequent target for sophisticated, state-aligned operations, underscoring the urgency for advanced cybersecurity defenses. Between 2024 and the first quarter of 2025, manufacturing saw a 71% surge in threat actor activity, with 29 distinct groups targeting the sector.
This risk is compounded by the rapid adoption of Industry 4.0 technologies such as artificial intelligence, IoT devices, and cloud computing. While these innovations significantly improve efficiency and productivity, they also introduce complex new vulnerabilities across both IT and OT environments. These gaps are increasingly being exploited by cyber adversaries who recognize the strategic value of manufacturing data, intellectual property, and operational continuity.
Given this convergence of national security and cyber risk, collaboration between public and private entities is more vital than ever. Bitsight has unique insight into the global supply chain and the variety of cyber threats that organizations face. The broader technology sector plays a pivotal role in supporting the cyber resilience of manufacturing, providing intelligence, tools, and frameworks that help defend against the full spectrum of cyber threats. This integrated approach to cyber defense is essential to safeguard not just individual manufacturers, but the broader economic and national interests they support.
Top 3 cyber threats in Manufacturing
Complex supply chains introduce easy entry points: Manufacturing often involves large, global supply chains with smaller partners that lack strong cybersecurity. These weaker links are frequently used as initial footholds to breach bigger targets, a classic supply‑chain attack. So what are the key threats to manufacturing?
1. Supply chain attacks
Modern cyberattacks increasingly bypass direct defenses by targeting the weakest links in the supply chain: third-party vendors, software suppliers, and hardware manufacturers. By infiltrating trusted partners, threat actors gain covert access to internal systems, making detection and response more complex and delayed.
2. Phishing as an initial vector
Phishing remains the top entry point for cyberattacks, with over 90% of incidents originating from deceptive emails. These socially engineered messages can compromise employee credentials or deliver malicious payloads, enabling attackers to pivot laterally through integrated systems—including supply chain platforms—amplifying disruption.
3. Open-source software vulnerabilities
The widespread use of open-source components in software supply chains introduces significant security blind spots. As cybercriminals increasingly exploit vulnerabilities in open-source package repositories, the risk of tainted or malicious code entering enterprise environments grows, especially when due diligence is lacking.
Impact on the business
Production delays & operational disruption
Successful cyberattacks can grind manufacturing operations to a halt—causing delays, corrupting product integrity, or sabotaging automation systems. The ripple effects often impact downstream partners and customers, leading to contractual penalties and lost revenue.
Financial losses
Remediating supply chain breaches is costly. From incident response and forensic investigations to system rebuilds and legal expenses, the financial toll can be severe. In sectors with narrow margins and high throughput, even short downtime can result in millions in lost output.
Reputational damage & trust erosion
Supply chain security is often seen as an indicator of an organization’s broader cybersecurity posture. Incidents affecting supply chain systems can influence perceptions among customers, partners, and regulators, potentially impacting business relationships, stakeholder confidence, and brand reputation over time.
Valuable intellectual property & espionage opportunity
State-sponsored threat actors are particularly drawn to manufacturing due to the sector’s high-value intellectual property, such as chip designs and proprietary industrial processes. For example, at least three distinct state-linked threat groups have been implicated in recent phishing campaigns specifically targeting Taiwan’s semiconductor ecosystem. Their targets included not only chip manufacturers but also companies involved in design, testing, and supply chain logistics, as well as financial analysts focused on Taiwan’s semiconductor sector.
To enhance credibility and increase infection rates, the attackers used employment-themed phishing emails sent from compromised Taiwanese university email accounts. These emails often contained ZIP or PDF files laced with malware, hosted on reputable file-sharing platforms like Zendesk and Filemail. The campaigns align closely with rising U.S. and Taiwanese export restrictions on advanced semiconductor technologies, further emphasizing the strategic value of this intellectual property to national development agendas.
Strategic implications
Taiwan’s semiconductor sector is a linchpin in the global technology supply chain. Any compromise or disruption could lead to significant ripple effects across global markets, influencing everything from consumer electronics to defense systems. The Biden administration’s export controls have only intensified the push for domestic semiconductor capabilities, prompting more aggressive cyber operations aimed at reducing reliance on foreign technology. As a result, these state-sponsored campaigns not only represent immediate cybersecurity concerns but also reflect long-term strategic moves that could reshape global tech power dynamics.
Operational Technology (OT) systems are especially weak
Manufacturing depends on legacy OT systems that were never built for cybersecurity. These systems are often under‑monitored, unpatched, and unsegmented — and any compromise can directly affect production or safety.
Diverse cyber threat landscape
Manufacturing is facing a barrage of threats:
- Ransomware: Nearly half of breaches in manufacturing are ransomware-related
- Spear-phishing: Used extensively to harvest credentials and deliver malware
- Remote Access Trojans (RATs) and backdoors: Deployed in long-term espionage or disruption campaigns
Why it matters
- Financial risk for manufacturers is immense, from operational shutdowns to ransom demands.
- National and economic security: Tampering with manufacturing capabilities can disrupt critical infrastructure and defense supply chains.
- Competitive standing: Letting others steal your trade secrets means losing edge and market share.
How Bitsight CTI can help
Bitsight provides contextual, intelligence-driven ratings by monitoring external indicators of security posture across OT systems and third-party suppliers. Key benefits include:
- Visibility across the ecosystem: Understand which suppliers or business units have weak defenses or are flagged in breach databases.
- Prioritized risk mitigation: Using security performance data, Bitsight enables you to identify and secure high-risk assets like exposed OT systems, unpatched devices, or misconfigured remote access points.
Threat Actor Identification & Prioritization
- Bitsight’s dark‑web monitoring and AI‑driven intelligence surface active threat campaigns targeting Industry 4.0.
- Continuous tracking of geopolitical-aligned APT activity (e.g., Chinese‑linked APT10, Volt Typhoon) helps prioritize defenses.
- Threat actor intelligence: Gain insights into tactics, techniques, and procedures (TTPs) being used by actor groups targeting your sector — such as phishing campaigns or RAT indicators — and prepare with tailored detection/enforcement.
External Exposure & Risk Dashboards
- Quantify remote-access and cloud service exposures.
Continuous Monitoring & Early Alerts
- Real-time notifications on new threat actor activity, zero-day tool usage, or shift in attacker behavior.
Strategic Reporting for Stakeholders
- Dashboards to show business leaders and board members impact and ROI.
- Demonstrate proactive posture against both cybercriminals and state-aligned threats.



