Practical advice to secure your expanding attack surface

The other week, Bitsight published research identifying thousands of organizations using internet-facing and exposed webcams with many video and audio feeds susceptible to spying. The potential consequences are serious – an attacker could potentially view private activities and eavesdrop on sensitive conversations, presenting a variety of privacy and security concerns. Below are some of the screenshots Bitsight captured from exposed devices (blurred for privacy):
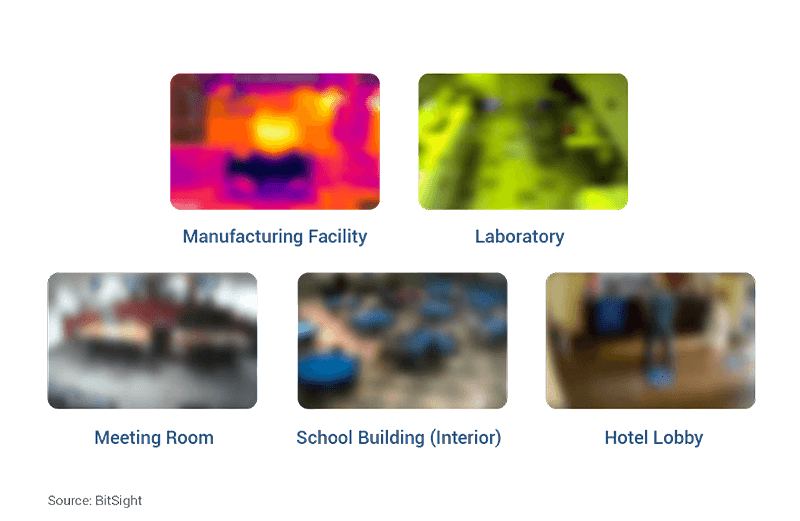
Internet of things (IoT) devices like webcams have attracted recent attention from the United States government. In March 2023, the White House released the U.S. National Cybersecurity Strategy, highlighting its strategic cybersecurity objectives. A major focus is on improving security of IoT devices:
“Many of the IoT devices deployed today are not sufficiently protected against cybersecurity threats. Too often they have been deployed with inadequate default settings, can be difficult or impossible to patch or upgrade, or come equipped with advanced — and sometimes unnecessary — capabilities that enable malicious cyber activities on critical physical and digital systems. Recent IoT vulnerabilities have shown just how easily bad actors can exploit these devices to construct botnets and conduct surveillance.”
Bitsight’s research — and the White House’s focus on IoT risk — sheds light on a larger issue. The overarching problem is that the attack surface is expanding, bringing with it many unorthodox threats not limited to IoT device risk. Organizations must develop a keen understanding of what factors contribute to the expanding attack surface and then prioritize exposure management, vulnerability management, and other frameworks to mitigate risk in their first- and third-party ecosystems.
Exposure management amid an expanding attack surface
Plain and simple, a larger attack surface gives attackers more ways to attack your organization. Three factors greatly contribute to the expanded attack surface, each carrying its own risks. But, exposure management can help mitigate these risks.
1. Cloud adoption
Risks:
Cloud services offer many benefits, such as mass storage and system management without the need for physical infrastructure. However, their adoption also poses certain risks to organizations. When using cloud services, organizations must trust their cloud service provider (CSP) to safeguard the sensitive data stored on their infrastructure. Unfortunately, CSP misconfigurations — and software vulnerabilities exploited by threat actors — can compromise this data and even allow attackers to deploy malware like ransomware.
Application programming interfaces (APIs) further compound these security risks by facilitating communication between applications, including those hosted in the cloud. A single breach can have far-reaching consequences, and the rising number of cloud-based applications may exacerbate the consequences of future breaches. The proliferation of remote work arrangements has also increased multi-cloud adoption, creating a larger attack surface for potential cyber threats to exploit.
As organizations increasingly shift their assets and infrastructure to the cloud, attacks on cloud services continue to rise. To effectively mitigate these risks, reliable cloud security monitoring solutions are crucial. However, one of the most significant challenges is gaining complete visibility across the ecosystem, especially with remote workforces and the constantly expanding attack surface. Organizations must have a thorough understanding of their attack surface because they can’t secure what they can’t see.
Solutions:
Bitsight offers an effective solution for visualizing, understanding, and managing cyber risks in your expanding digital ecosystem. This technology not only monitors internal assets but also serves as a robust cloud security monitoring solution. By using Bitsight, you can continuously monitor your network to better protect it from vulnerabilities.
With advanced attack surface monitoring, Bitsight provides the necessary visibility to assess your current risk exposure, prioritize assets that are at greatest risk, and take steps to minimize risk.
Using a centralized dashboard, Bitsight offers visibility across all your attack surfaces, making it easier to visualize areas of critical or excessive risk and prioritize remediation. Furthermore, Bitsight uses a cloud security audit to discover hidden assets and cloud instances common to shadow IT, which helps to align with corporate security policies. By visualizing your digital ecosystem, you can assess cyber risk and prioritize remediation for areas of highest risk exposure.
In addition to these benefits, Bitsight can monitor the risk of data stored in cloud environments, which solves the challenge of the shared responsibility model for security. Bitsight helps to discover risk on remote networks and provides visibility into the risk of insecure home and remote offices, simplifying attack surface management.
In summary, Bitsight:
- Identifies concentrated risk areas by monitoring cloud security controls
- Allows effective allocation of security resources by providing clear visibility into digital ecosystem
- Helps focus remediation efforts in multi-cloud environments
- Pinpoints security risk locations with a map-based view on the dashboard
2. Rising asset inventories
Risks:
The greater the number of technology assets an organization possesses, the greater the probability that at least one of these assets will have a vulnerability that attackers can exploit to gain entry into the company's internal systems and data. Security teams have the daunting task of safeguarding an average of 165,000 cybersecurity assets, ranging from cloud-based devices, applications, data assets, and users.
The proliferation of remote work has only compounded the issue of cybersecurity threats. Remote employees typically use home networks that are less secure than corporate-controlled networks, making it easier for attackers to gain access to the company's network and devices. For example, employees may not change the default passwords for their routers, providing further opportunities for attackers to infiltrate the network. Home networks also typically have a range of connected devices, giving attackers more opportunities to gain access to the network and ultimately to company-issued machines. Bitsight research has found that work-from-home remote office networks are 3.5 times more likely than corporate networks to have at least one family of malware and 7.5 times more likely to have at least five distinct families of malware.
Another significant issue is shadow IT, where employees use devices, software or services without the knowledge of the employer's IT department. Shadow IT can create problems because it can be difficult for IT departments to monitor and protect against cybersecurity threats when they are not aware of all the devices and services in use. According to a report, Forbes and IBM found that even when organizations know about shadow IT, they often do not include it in their threat assessments.
Solutions:
To effectively safeguard your digital assets, it is critical to have a clear and up-to-date inventory of all your assets and their associated cyber risks. Make asset visibility a top priority, and take steps to secure endpoints, limit the use of shadow IT, and continuously monitor your ecosystem for potential vulnerabilities.
In addition, focus on cybersecurity analytics that have been proven to have significant correlations to cyber incidents. For instance, Bitsight's Patching Cadence risk vector measures an organization's vulnerability management program's effectiveness, and has a significant correlation to cybersecurity incidents, making it an important metric to track.
Bitsight offers a comprehensive view of your attack surface in both on-premise and cloud environments. This solution enables you to detect cyber risks, identify shadow IT, and visualize areas of high risk to effectively identify and remediate vulnerabilities. Bitsight helps you drive accountability, develop security controls, and report evidence of your program's performance to stakeholders, thereby building trust and confidence.
3. Rising third-party footprints
Risks:
Third-party vendors and partners are essential components of modern businesses, driving competition, operational efficiency, and digital transformation. However, managing these partners' exposure to vulnerabilities can be a daunting task, especially given the rapid growth of the modern supply chain. Unfortunately, the 2022 Verizon Data Breach Investigations Report highlights a startling statistic: 62% of breached companies report that the attacker gained network access via a vendor, partner, or another third-party. This finding emphasizes the need for organizations to prioritize robust security measures to safeguard against such risks and protect their sensitive data. Attackers often exploit software vulnerabilities within third-party ecosystems, enabling them to move laterally into internal systems. Continually evaluate and improve security measures to maintain a strong security posture against these evolving threats. Ultimately, taking proactive steps to secure third-party partners is one of the most impactful ways to achieving long-term success and minimizing security risks.
A successful attack on your third-party partners could potentially result in negative effects for you, including business disruption, financial loss, reputational harm, and even compromise of your internal systems and data. But managing third-party cyber risk is anything but simple. Many organizations rely on time-consuming processes to evaluate cyber risk in their third-party ecosystems, opting to send mass emails and spreadsheet questionnaires to collect subjective information. This approach makes it difficult to swiftly and accurately assess and address cyber risks, particularly regarding new vulnerabilities that may arise.
Solutions:
A solution like Bitsight allows you to gain visibility into cyber risks impacting your entire third-party ecosystem. Bitsight takes you beyond the typical annual assessment, empowering you to continuously monitor risk in your third-party ecosystem so you can quickly mitigate risks when they arise.
Bitsight helps organizations streamline cyber risk detection, management, and mitigation within their third party ecosystem, including vulnerabilities. Through surfacing actionable vulnerability data based on severity and enabling scalable vendor outreach through built-in questionnaire capabilities, organizations are empowered to efficiently remediate risk. Bitsight’s solutions help organizations:
- Detect, manage, and mitigate emerging zero-day vulnerabilities and events with speed
- Scale and track vendor outreach efforts with precision
- Remediate risk quickly with better prioritization of vendor outreach efforts
- Confidently adhere to growing regulatory pressure with easy access to vulnerability data
Next steps
The expansion of the attack surface has increased the risk of cyber threats for organizations. With the adoption of cloud services, the rising inventory of digital assets, and increasing third-party footprints, the challenges of managing cyber risk have become more complex.
However, solutions like Bitsight can help organizations mitigate these risks. Bitsight provides visibility across all attack surfaces, identifies concentrated risk areas, prioritizes remediation efforts, and monitors the risk of data stored in cloud environments. By focusing on cybersecurity analytics and building a comprehensive security performance management program, organizations can effectively manage cyber risk and build trust and confidence with stakeholders. Ultimately, to stay ahead of evolving cyber threats, it is essential to prioritize exposure management and take proactive steps to safeguard digital ecosystems.
Contact Bitsight today to learn how we can help.


