Bitsight identifies thousands of organizations using Internet-facing and exposed webcams

Bitsight has identified thousands of organizations around the world using Internet-facing webcams and similar devices, finding many video and audio feeds susceptible to eavesdropping.
To measure device exposure, Bitsight studied hundreds of thousands of organizations from around the world. Our analysis revealed that nearly 3% of Bitsight-tracked organizations have at least one Internet-facing video- and/or audio-enabled device, contrary to best practices. Of these organizations, 9% were found to have at least one device with exposed video and/or audio feeds, allowing an attacker to directly view video feeds and/or eavesdrop on conversations. Therefore, one in 12 Bitsight-tracked organizations with Internet-facing webcams and/or similar devices are susceptible to video and/or audio compromise.
We identified exposed video and audio feeds from organizations spanning a variety of sectors, including those from the hospitality, education, technology, and government sectors. Education is most at risk – nearly one in four Bitsight-tracked education organizations with Internet-facing webcams and/or similar devices are susceptible to video and/or audio compromise.
Fortune 1000 organizations are among the exposed, including a Fortune 50 technology subsidiary; a Fortune 100 entertainment company; a Fortune 50 telecommunications company; a Fortune 1000 hospitality company; and a Fortune 50 manufacturing company.
Our findings indicate that personal privacy and organizational security are potentially at risk. Additionally, these findings come at a time when governments are assessing the security implications of webcams. Security leaders should review their organization’s attack surface and take steps to reduce exposure.
Internet of things (IoT) device risk growing
Public and private concern about risks associated with Internet-connected devices is growing. In March 2023, the White House released the U.S. National Cybersecurity Strategy, highlighting its strategic cybersecurity objectives. A major focus is on improving security of IoT devices:
“Many of the IoT devices deployed today are not sufficiently protected against cybersecurity threats. Too often they have been deployed with inadequate default settings, can be difficult or impossible to patch or upgrade, or come equipped with advanced—and sometimes unnecessary—capabilities that enable malicious cyber activities on critical physical and digital systems. Recent IoT vulnerabilities have shown just how easily bad actors can exploit these devices to construct botnets and conduct surveillance.”
What devices did Bitsight analyze?
Bitsight analyzed video- and audio-enabled devices deployed by organizations around the world. The devices we analyzed overwhelmingly use the Real-Time Streaming Protocol (RTSP) to communicate over the Internet but some use the HTTP and HTTPS protocols. The RTSP protocol is used to transmit multimedia content like video and audio; client commands like record, pause, and play are made possible by the RTSP protocol.
Many of the researched devices are webcams; other devices include network video recorders (NVR), smart doorbells, smart vacuums, and more. Some of the devices we analyzed are suspected to be deployed for security purposes.
Data and methodology
Bitsight assembled an Internet-wide dataset of IP addresses owned by organizations with at least one open RTSP/HTTP/HTTPS port. These IPs were then mapped to Bitsight’s inventory of organizations, allowing us to determine rates of exposure found among Bitsight-tracked organizations.
Among other objectives, we aimed to answer the following questions:
- What percentage of Bitsight-tracked organizations have at least one Internet-facing video- and/or audio-enabled device?
- What percentage of the above organizations use at least one video- and/or audio-enabled device with exposed video and/or audio feeds?
Vulnerabilities and misconfigurations identified
Bitsight’s analysis revealed that many organizations are using Internet-facing video- and/or audio-enabled devices, with a subset of those organizations using devices with exposed video and/or audio feeds (exposed devices). Exposed organizations are those identified as using at least one exposed device.
Internet-facing devices
Contrary to best practices, these Internet-facing devices are not behind a firewall or virtual private network (VPN). Such devices are open to fingerprinting, information gathering, and other activities of bad actors.
Exposed devices
Exposed devices in our analysis are either misconfigured or suffer from a software vulnerability. The former could arise because the user failed to set a password, while the latter is typically attributable to a specific kind of access control vulnerability called an insecure direct object references (IDOR) vulnerability. Either way, the video/audio feed should be protected by access control measures but is not. Therefore, the device’s security controls can be bypassed, allowing an attacker to view video feeds and/or eavesdrop on conversations. Sophisticated attackers could also potentially alter exposed feeds.
IDOR vulnerabilities are a reoccurring problem
IDOR vulnerabilities have caught our attention in recent months. In 2022, Bitsight discovered several critical vulnerabilities in a popular vehicle GPS tracker, presenting a myriad of threats to personal privacy, safety, and organizational security. We discovered an IDOR vulnerability – tracked as CVE-2022-34150 – that potentially allowed an attacker to access information from any device ID regardless of the logged-in user.
This particular type of vulnerability has presented itself in two major Bitsight security research efforts, highlighting secure authentication as a critical area of vulnerability management.
Potential consequences are serious
Organizations identified as using exposed devices – including their customers, business partners, employees, and contractors – should be alerted to potential threats.
Personal privacy and security
-
An attacker could potentially view private activities and eavesdrop on sensitive conversations. Individuals in an exposed device’s proximity could potentially expose personal details and other valuable or compromising information via video and/or audio.
-
The locations of individuals could be potentially revealed.
Organizational privacy and security
-
An attacker could potentially view business-related activities and eavesdrop on professional conversations, potentially exploiting the sensitive business information of the target and/or third parties.
-
Physical security could be threatened. We observed webcams overlooking access-controlled doors and rooms, potentially providing bad actors with key information relating to physical security.
-
Organizational cybersecurity could be potentially impacted. Deploying Internet-facing and exposed video and/or audio devices increases an organization’s attack surface, potentially threatening your – and your third parties’ – internal systems and data.
Sector and geographic impact
Spanning 54 countries, exposed organizations are concentrated in the education, technology, government/politics, and media/entertainment sectors.
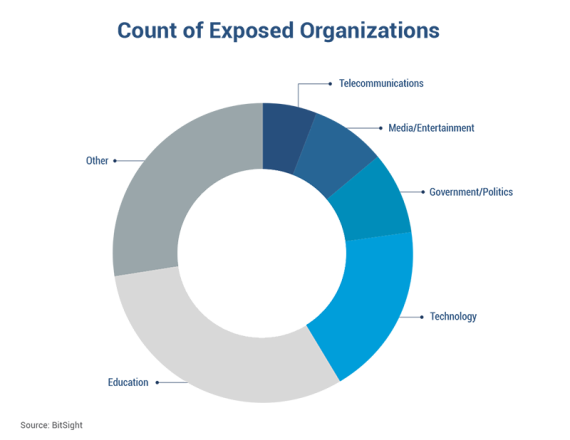
The top 10 countries with the most exposed organizations are:

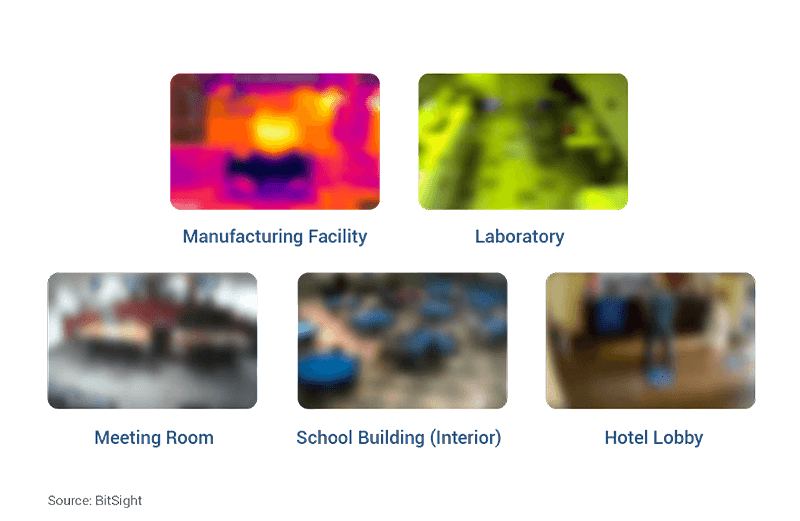
Webcams overlooking sensitive areas
We observed webcams overlooking intimate spaces across a variety of sectors. Below are some of the screenshots we captured (blurred for privacy):
Education most at risk
Most exposed organizations are in the education sector. Nearly one in four education organizations tracked by Bitsight with Internet-facing webcams and/or similar devices are susceptible to video and/or audio compromise; that’s three times higher than the rate for all Bitsight-tracked organizations.
The increased presence of minors at these educational organizations could present additional challenges to personal privacy and security.
Major organizations exposed
We identified major organizations using devices with exposed video and/or audio feeds:
-
A Fortune 50 technology subsidiary
-
A Fortune 100 entertainment company
-
A Fortune 50 telecommunications company
-
A Fortune 1000 hospitality company
-
A Fortune 50 manufacturing company
Rate of exposure for large organizations
Organizations with many employees seem more likely to have devices with exposed video and/or audio feeds. Nearly one in 50 large organizations in Bitsight’s inventory with Internet-facing webcams and/or similar devices are susceptible to video and/or audio compromise.

Short-term recommendations to protect your organization
Our analysis reveals video- and/or audio-enabled devices as yet another consideration when assessing your organization’s attack surface.
Using webcams and similar devices to serve any purpose in your organization could expose your organization to a variety of unorthodox attacks and compromising scenarios. Exposed webcams allow an attacker to be a “fly on the wall,” potentially listening in on key conversations and viewing potentially sensitive video feeds in real time. They also increase the number of entry points an attacker can leverage to attack your systems.
Organizations without any video- and/or audio-enabled devices could be indirectly exposed via a third party. Your vendor or business partner’s use of an exposed device could potentially expose sensitive information you share with that third party during a meeting or a video conference call. An attacker could also potentially leverage Internet-facing and exposed devices used by your third party to subsequently attack your organization.
Organizations should immediately engage in outreach and remediation efforts:
-
Identify any video- and/or audio-enabled devices deployed by your organization and/or your third-party business partners, and promptly assess the security of these devices.
-
If the devices are not behind a firewall or VPN, then prioritize doing so.
-
If the devices lack authentication to access video and/or audio feeds, then prioritize setting up access control measures to protect them.
-
Unfortunately, some of the exposed devices we identified suffer from a software vulnerability, leaving the developer as the only route to remediation. In this case, we recommend you stop using the exposed device and change brands if the vendor is not able or willing to remediate.
-
Our findings should alert organizations to the potential threats presented by video- and/or audio-enabled devices. In an effort to reduce similar threats as those presented in this research, we urge organizations to responsibly manufacture, adopt, and distribute IoT devices. We also encourage organizations to consider video- and/or audio-enabled devices as potential threats to first-party and third-party cyber risk.
*Tiago Martins is no longer an employee of Bitsight but made substantial contributions to this research.



