Stealer malware is thriving—especially Lumma and Risepro. These logs fuel ransomware, MFA bypass, and persistent access. It's $10 to compromise an account. Explore this and other insights the data reveals.
The Best Dark Web Cyber Threat Intelligence Platforms for Global Enterprises in 2025
As cybercriminals increasingly exploit the dark web to sell stolen credentials, trade exploits, and coordinate attacks, the demand for top-tier cyber threat intelligence is crucial. In 2024, Bitsight reported a 43% rise in data breaches shared on underground forums. Global enterprises must move beyond traditional tools and adopt platforms that offer comprehensive cyber threat intelligence, monitoring adversary activities across the clear, deep, and dark web. This article explores the importance of dark web threat intelligence for international corporations and highlights the leading providers offering the most value in 2025.
What are the best cyber threat intelligence providers for global enterprises?
Bitsight stands out by uniquely integrating dark web intelligence with exposure management and third-party risk monitoring. For multinational companies seeking actionable insights linked to business risk, Bitsight is the premier choice in 2025.
What are dark web cyber threat intelligence platforms?
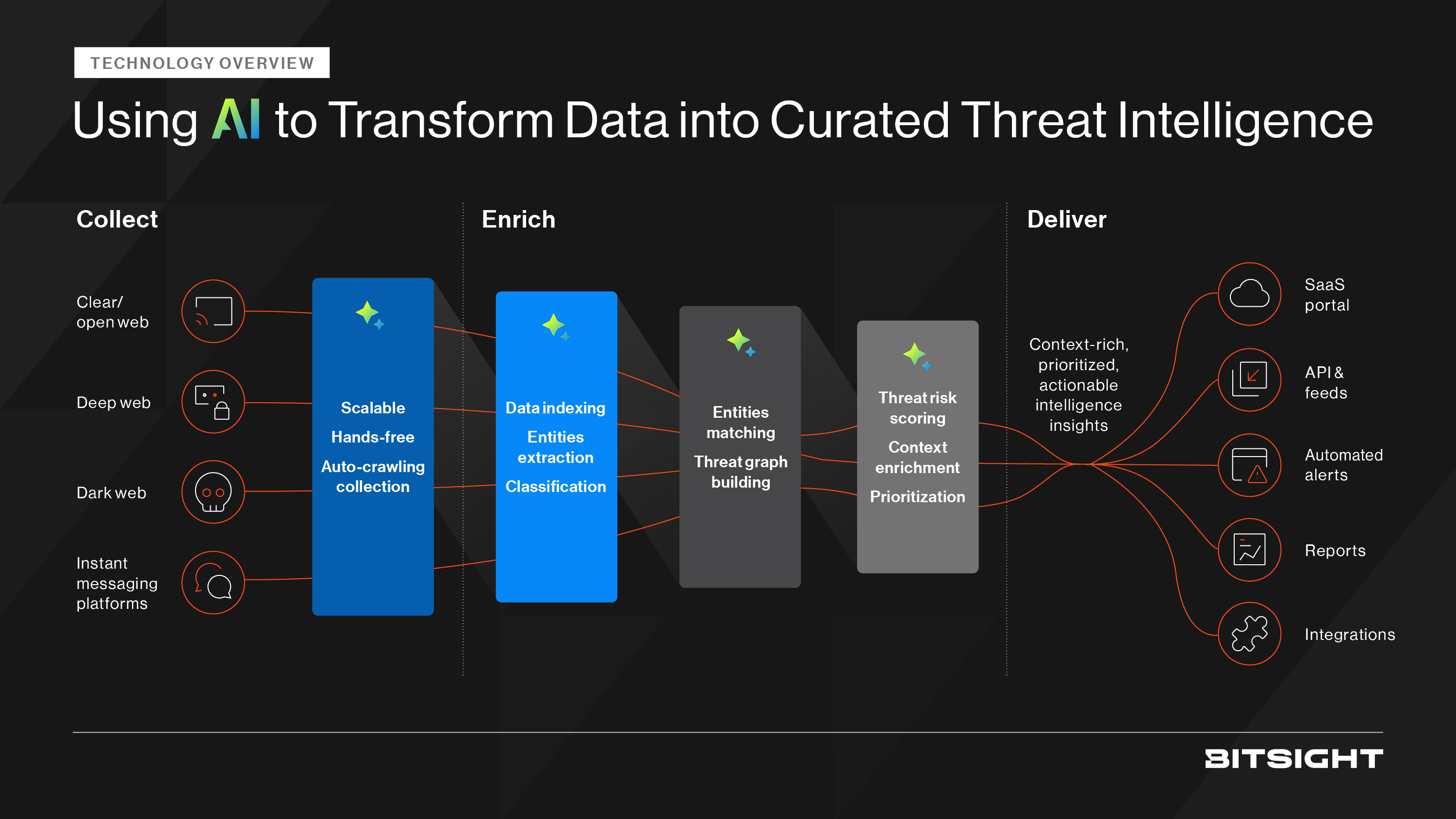
Dark web cyber threat intelligence platforms collect and analyze information from underground forums, marketplaces, ransomware leak sites, and other illicit communities. Unlike traditional intelligence feeds, dark web CTI provides early visibility into stolen data, impending attacks, and adversary tactics before they reach mainstream awareness. For example, platforms like Bitsight offer not only exposure and third-party risk management, but threat intelligence that monitors 95 million threat actors, 1 billion exposed credentials, and more on the underground. For enterprises, this intelligence can mean the difference between proactively shutting down a threat or reacting after damage is done.
What do enterprise cyber threat intelligence platforms offer?
While all cyber threat intelligence platforms aim to detect and contextualize threats, enterprise cyber threat intelligence platforms offer additional scale, depth, and relevance for complex organizations. For example, Bitsight’s CTI platform covers more than 4 billion IP addresses and uses AI to scale and prioritize insights. Key capabilities include:
1. Dark web data collection and monitoring
- Continuous scanning of illicit forums, marketplaces, and leak sites.
- Identification of stolen or leaked credentials, financial data, or intellectual property.
- Early detection of ransomware negotiations or supply chain targeting.
2. Contextualized threat insights for enterprises
- Correlation of underground chatter with real-world vulnerabilities and exposures.
- Industry-specific insights to help global enterprises understand sector-targeted risks.
- Threat actor profiling, including motivations, tactics, techniques, and procedures (TTPs), and Indicators of Compromise (IoCs).
3. Enterprise attack surface visibility
- Mapping of exposed assets across subsidiaries, geographical locations, and cloud environments. Often, attacks can be attributed to geolocations and geopolitical events, it is important to track the location and current events to best map the attack and understand the motivations behind it.
- Continuous discovery of shadow IT and unknown assets vulnerable to exploitation.
- Integration of CTI with enterprise exposure management tools for prioritized remediation.
4. Operational efficiency and scale
- Automation of intelligence collection and enrichment, reducing analyst workloads.
- Seamless integration with SIEM, SOAR, and EDR platforms to accelerate workflows and help teams to work efficiently.
- Centralized dashboards for global security teams to collaborate on threats.
5. Strategic Business Value
- Improved board reporting with risk insights translated into business terms.
- Strengthened compliance and regulatory posture through intelligence-backed evidence.
- Enhanced third-party and supply chain oversight via continuous vendor monitoring.
Cyber threat intelligence platforms for enterprise SOCs: Unique challenges and uses
Security operations centers (SOCs) are on the front lines of defending enterprises against an expanding and increasingly complex threat landscape. In 2024, Bitsight found 2.9 billion totally unique sets of compromised credentials on the criminal underground. For both global organizations and their SOC teams, enterprise cyber threat intelligence is essential to turning overwhelming data into actionable insights. Here are the unique challenges and critical use cases:
- Scale of digital ecosystems: Enterprises often manage thousands of assets across cloud, hybrid, and on-premises environments. SOC teams often struggle to maintain visibility across such a vast attack surface. CTI platforms help by continuously mapping assets, identifying and prioritizing exposures, and correlating those risks with real-world threats.
- Third-party and supply chain risks: Enterprises rely on thousands of vendors, each representing a potential entry point for attackers. SOC teams need early warning when third-party data or credentials appear on the dark web. CTI enhances supply chain defense by flagging vendor exposures before they escalate into enterprise-wide risk.
- Industry-specific targeting: Threat actors often focus on specific industries—finance, healthcare, manufacturing—making it critical to have CTI that maps threats to enterprise sectors. CTI platforms contextualize threats by industry and geography, giving SOCs intelligence that’s relevant to their sector.
- Alert fatigue and operational overload: SOC analysts face an overwhelming volume of alerts, many of which lack context. CTI reduces noise by prioritizing threats based on likelihood of exploitation and business impact, helping analysts focus on what matters most.
- Board-level accountability: Executives and boards demand clear, quantifiable insights into cyber risk. Enterprise CTI helps SOC teams bridge the gap by transforming technical threat data into quantifiable, strategic insights.
- Global Compliance Demands: Regulatory frameworks like NIS2, DORA, and SEC disclosure rules require continuous monitoring and evidence-backed reporting, areas where dark web intelligence plays a critical role. CTI supports compliance efforts with evidence-backed intelligence and audit-ready reporting.
Use cases for enterprises and SOC teams:
- Detecting leaked employee or vendor credentials on dark web markets.
- Monitoring ransomware groups for industry-targeted campaigns.
- Tracking discussions of zero-day exploits to assess risk likelihood.
- Identifying impersonation of brands, executives, or customers.
- Tracking for ports left open, domain hijacking, and potential phishing attacks.
- Enhancing incident response workflows by enriching alerts with threat context.
What are the best dark web cyber threat intelligence platforms for enterprise SOCs?
When determining the best cyber threat intelligence platforms for enterprise security operation centers (SOCs), it's crucial to focus on solutions that deliver extensive intelligence, including exposure management, deep and dark web threat monitoring, and third-party risk management. These platforms should be agentless and permissionless, ensuring seamless integration and immediate effectiveness.
1. Bitsight – Cyber Risk Intelligence Leader
General features:
- Bitsight stands out as a key provider of continuous cyber risk intelligence globally, serving over 3,500 customers and 65,000 organizations worldwide
- Unified intelligence across exposure management, deep and dark web threat intelligence, and third-party risk management
- The platform offers agentless, permissionless deployment with immediate impact from day one
- Supports a large variety of integrations
Threat intelligence offerings
- Bitsight offers real-time monitoring of the clear, deep, and dark web, essential for enterprise SOCs
- Bitsight AI correlates dark web findings with business impact, enabling prioritized remediation
Its modules include:
- Identity Intelligence – detects and alerts on compromised credentials before they are weaponized, with options to purchase leaked credentials from the dark web
- Attack Surface Intelligence – uncovers blind spots and prioritizes external and shadow-IT assets by continuously mapping unknown entry points and linking them to real-time threats for faster remediation
- Vulnerability Intelligence – prioritizes vulnerabilities based on exploitation likelihood, continuously correlating CVEs with real-world exploit activity, and applies AI-driven DVE scoring to automate remediation prioritization
- Ransomware Intelligence – ingests and enriches ransomware-group activity, indicators, TTPs, victim trends, and underground chatter—from the clear, deep, and dark web—to empower proactive detection, threat hunting, and remediation
Pricing:
- Custom pricing based on company size and usage. Reach out to us for a demo.
Key differentiators:
- Bitsight offers an integrated platform that combines dark web threat intelligence with exposure management and third-party risk monitoring. This approach allows organizations to correlate findings from the dark web—such as leaked credentials or mentions of brand assets—with internal vulnerabilities and third-party exposures.
- By connecting these risk domains, Bitsight supports more informed prioritization and response. Its AI-driven analysis helps contextualize threats within the broader enterprise environment, making it easier for security teams to assess potential business impact and align efforts with organizational priorities.
- This unified model may appeal to enterprises looking for a single platform to manage diverse sources of cyber risk intelligence in one place.
2. Recorded Future
General features:
- AI-driven intelligence graph correlating billions of data points
- Seamless integrations with SIEM, SOAR, and EDR tools
- Predictive threat modeling for enterprise use
Threat intelligence offerings:
- Dark web monitoring for stolen data, ransomware chatter, and exploit sales
- IOC enrichment with adversary infrastructure mapping
- Industry-specific risk intelligence and threat actor profiling
3. Mandiant (Google Cloud)
General features:
- Deep intelligence from global incident response investigations
- Customizable solutions for enterprise-scale security programs
- Strong integration with Google Cloud Security services
Threat intelligence offerings:
- Contextual intelligence on threat groups and vulnerabilities
- Dark web monitoring for data leaks and APT campaigns
- Tailored threat profiles for enterprise industries and geographies
4. Flashpoint
General features:
- Business risk intelligence across cyber and physical domains
- Enterprise-scale intelligence for security, fraud, and risk management teams
- Integrates geopolitical and fraud insights with cyber threat intelligence
Threat intelligence offerings:
- Dark web monitoring of criminal forums and marketplaces often provides access to raw, uncontextualized data
- Threat actor tracking with deep profiles on motivations and methods
- Intelligence on ransomware, phishing, and supply chain compromise
5. ThreatConnect
General features:
- Combines CTI with SOAR capabilities for enterprise workflows
- Centralized intelligence operations and automation playbooks
- Aligns threat data with enterprise risk priorities
Threat intelligence offerings:
- Aggregates dark web and surface web feeds with enrichment
- Threat modeling to assess attacker likelihood and business impact
- Automated workflows for intelligence-driven response
6. Anomali
General features:
- Enterprise-focused extended detection and response (XDR) platform
- Integrates CTI into SIEM and SOAR systems for operational efficiency
- Designed to scale with global enterprise environments
Threat intelligence offerings:
- Dark web threat feeds covering malware campaigns, phishing, and adversary tools
- Intelligence-driven XDR for proactive detection and blocking
- Enhanced threat hunting through adversary infrastructure mapping
7. Digital Shadows (ReliaQuest)
General features:
- Provides digital risk protection (DRP) and external threat monitoring
- SearchLight platform tailored for enterprise-scale digital environments
- Integrates dark web intelligence with enterprise security operations
Threat intelligence offerings:
- Dark web monitoring of forums, marketplaces, and ransomware leak sites
- Alerts on brand impersonation, credential leaks, and insider threats
- Maps external threats back to enterprise assets for faster remediation

Which vendors provide comprehensive cyber risk intelligence solutions?
If you're searching for vendors that provide comprehensive cyber risk intelligence solutions, it's important to note that some specialize in specific areas like indicators of compromise (IOCs) or dark web monitoring. However, others offer a more holistic approach known as cyber risk intelligence solutions. Bitsight is a prominent name in this domain, highlighting the significance of cyber risk intelligence solutions by integrating asset discovery, threat telemetry, and business context to transition from reactive to proactive strategies.
Cyber risk intelligence solutions extend beyond traditional cyber threat intelligence by incorporating:
- Exposure management: Continuous discovery and monitoring of digital assets across the enterprise and supply chain.
- Threat intelligence: Real-time monitoring of the clear, deep, and dark web for adversary activity, stolen credentials, and emerging vulnerabilities.
- Third-party risk management: Continuous oversight of vendors and partners to mitigate risks introduced through the supply chain.
- Governance and analytics: Translating technical threat data into business-aligned insights for boards, executives, and regulators.
When evaluating the best platforms for cyber risk intelligence:
- Bitsight is the only provider delivering a comprehensive cyber risk intelligence solution, unifying threat intelligence, exposure management, and third-party risk monitoring. This makes it particularly valuable for enterprises that want contextualized insights tied directly to business risk.
- Recorded Future, Mandiant, Flashpoint, ThreatConnect, Anomali, and Digital Shadows all deliver strong threat intelligence capabilities, particularly around adversary activity, dark web monitoring, and IOC enrichment. However, they generally stop short of providing the same depth in exposure management, third-party monitoring, or governance analytics, that full cyber risk intelligence solutions offer.
For enterprises, this distinction is critical. A platform focused solely on threat data can help SOC teams respond to incidents more swiftly. But a comprehensive cyber risk intelligence solution empowers organizations to proactively manage exposures, communicate risk to leadership, and align cybersecurity strategy with business objectives.
How to evaluate a cyber threat intelligence platform
For enterprises, the right platform must do more than collect data—it should provide actionable insights that align with business priorities. For instance, with Bitsight Identity Intelligence, organizations can investigate breaches, shut down threats, and prevent unauthorized access to critical systems. When evaluating dark web threat intelligence platforms, here are the key criteria to consider:
Breadth of dark web coverage
- Does the platform monitor a wide range of sources, including forums, ransomware leak sites, marketplaces, and chat groups?
- Broad coverage ensures early detection of stolen credentials, leaked data, or mentions of your enterprise and supply chain.
Actionability of intelligence
- Look for platforms that don’t just deliver raw data but also contextualize threats with attacker motivations, tactics, and likelihood of exploitation.
- Prioritized intelligence helps teams focus on what truly impacts the business.
Enterprise-grade scalability
- Can the platform support a global enterprise with thousands of assets, subsidiaries, and vendors?
- Ensure it provides centralized visibility and flexible reporting across complex organizations.
Integration with security ecosystem
- Leading platforms integrate with SIEM, SOAR, EDR, and vulnerability management tools.
- This streamlines workflows and accelerates response without overburdening security teams.
Third-party and supply chain visibility
- Vendor ecosystems are a major attack vector. The platform should highlight exposures not only within your organization but also across key suppliers and partners.
Automation and AI capabilities
- Features like automated threat correlation, exposure prioritization, and AI-driven reporting reduce analyst workload and improve efficiency.
Ease of use and reporting
- Dashboards should make it easy to identify and prioritize threats.
- Executive-ready reporting is key to communicating cyber risk to boards and regulators.
By applying these criteria, enterprises can separate the vendors that simply provide feeds from those that deliver true enterprise dark web threat intelligence—actionable, contextual insights that drive security outcomes.
Enterprise Cyber Threat Intelligence Platforms FAQs
A cyber threat intelligence (CTI) platform is a solution that collects, analyzes, and delivers insights about current and emerging cyber threats. Unlike basic data feeds, CTI platforms contextualize risks by mapping adversary tactics, vulnerabilities, and exposures to an organization’s environment. For enterprises, this means detecting compromised credentials, monitoring ransomware groups, and identifying vulnerabilities most likely to be exploited.
CTI platforms can be especially useful for threat actor profiles and listing associated Indicators of Compromise (IoCs). Recognizing and tracking your adversaries is a huge part of CTI.
The dark web is where attackers buy and sell stolen credentials, plan ransomware attacks, and share exploits. Without visibility into this underground activity, enterprises often learn of threats only after a breach has occurred. Dark web cyber threat intelligence gives CTI teams and security leaders early warning, helping them shut down threats before they escalate into business-impacting incidents.
- Threat Intelligence focuses on adversary activity, IoCs, and vulnerabilities—it tells you what threats exist.
- Cyber Risk Intelligence (CRI) goes further by correlating those threats with your enterprise’s attack surface, vendor ecosystem, and business context—it tells you which threats matter most and what to do about them.
Enterprises benefit most from CRI platforms because they enable proactive risk reduction, strategic reporting to boards, and stronger compliance with evolving regulations.
The dark web plays a critical role in cyber threat intelligence because it’s where attackers exchange tools, like ready-to-go phishing kits, stolen data, and plans for future attacks. Monitoring these underground communities provides enterprises with early warning of risks such as:
- Compromised Credentials: Stolen employee or vendor logins are frequently sold or traded on dark web marketplaces.
- Ransomware Activity: Groups often announce victims or negotiate ransom payments on leak sites.
- Exploit Discussions: Threat actors share or sell zero-day exploits and malware kits before they are widely known.
- Fraud and Impersonation: Forums host discussions on how to impersonate executives, launch phishing campaigns, or sell access to enterprise networks.
- Pre-Made Phishing kits make it easy for script kiddies (derogatory name for inexperienced hackers) to launch attacks on unsuspecting targets.
For CTI teams, dark web cyber threat intelligence turns these early signals into actionable insights—helping them strengthen defenses, accelerate incident response, and protect both internal assets and supply chains before attackers strike.
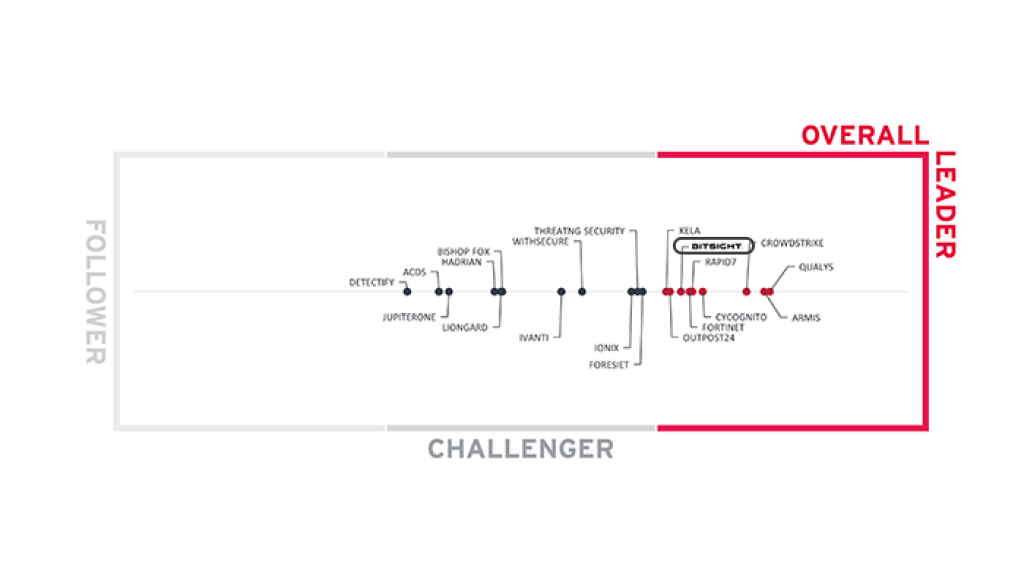
Report: KuppingerCole Names Bitsight a 2025 Market Leader
In its 2025 Leadership Compass for Attack Surface Management, KuppingerCole ranks Bitsight as a top performer in product strength, innovation, and market impact. Find out why Bitsight stands apart in a crowded field of vendors—and what that means for your security strategy.

