Stealer malware is thriving—especially Lumma and Risepro. These logs fuel ransomware, MFA bypass, and persistent access. It's $10 to compromise an account. Explore this and other insights the data reveals.
Defending Digital Trust: Fighting Brand Impersonation in the Wild


Audio Recap
Just do it.
Think different.
The happiest place on earth.
Nike, Apple, Disney are three iconic brands that have forever cemented themselves in our consciousness. How did they get there? A catchy slogan? A flashy logo? Sure, while slogans and logos change over time, they still make an impact. But what truly secures a brand’s reputation is trust. And trust is built over years, even decades, through consistency, authenticity, and relentless effort.
But in today’s digital world, brand trust is fragile. And increasingly, it’s being exploited.
The new battleground for brand trust
Your company’s brand no longer lives solely on billboards, commercials, or your own website. It’s scattered across social media platforms, email inboxes, mobile apps, and search results. And unfortunately, that ubiquity makes it a prime target for cybercriminals.
How many times have you spotted a sketchy version of Nike on X (formerly Twitter)? Have you ever received an email from your “bank” urging you to log in, only to realize the logo’s fuzzy and the email address ends in @secure-updates.net.io?
That’s not just spam. It’s a brand impersonation campaign in action, and it’s one of the most dangerous ways threat actors erode the trust you’ve spent years building.
Here are the top tactics cybercriminals use to exploit your brand and why it’s getting easier for them to pull it off.
Phishing for access (now with AI)
Phishing, a form of social engineering, is a type of cyber attack in which attackers impersonate a trusted entity. Threat actors pretend to be banks, employers, or service providers by replicating the look and feel of an organization to trick individuals into revealing sensitive information like passwords, credit card numbers, or personal details. They usually accomplish this via email, messages, or fake websites.
Attackers are now using tools to spin up fake login pages in seconds. Incredibly, these pages look eerily like the real thing. Imagine the implications of cloning an identity management login portal provider. Threat actors can gain immediate access to user credentials (username + password) and gain privileged access within organizations, potentially leading to a full-on breach. A realistic-looking phishing site, generated in under 30 seconds with just a few prompts, is all it takes for someone to get their feet inside a company’s digital perimeter.
Brand impersonation going viral
Brand impersonation on social media is when malicious actors create fake accounts that mimic legitimate brands to scam followers and spread misinformation. From fake X (formerly Twitter) accounts to phony Instagram shops, brand impersonation on social media is booming.
In one high-profile case, scammers cloned Australian retailers like Blue Illusion and Millers, luring customers with “closing down sales” that never existed. The sites looked real. The logos were spot-on. The payments went through…but not to the stores they thought they were buying from. Investigators eventually uncovered more than 140 of these “ghost stores,” many traced to operators overseas. Meanwhile, consumers were left empty-handed, and major digital platforms were criticized for their slow or inadequate responses, raising concerns about platform accountability and consumer protection online.
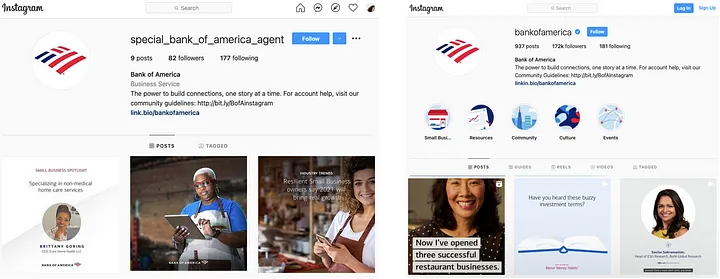
Rogue apps, real consequences
Rogue apps, commonly found on mobile app stores (Apple App Store, Google Play, Amazon Appstore, etc.), are lookalike apps used to steal user data or distribute malware.
Recently, a 72-year-old from Mahim, India lost nearly $60,000 after falling victim to a rogue app posing as a banking group. The fraudsters impersonated representatives of the bank and persuaded the senior citizen to trade shares with them.
Mimicking company branding is simple, as logos, colors schemes, and app design are copied directly into the rogue app. To make the app more convincing, threat actors usually flood the app store with fake 5-star reviews to boost credibility. These posts mimic real user behavior and even post helpful comments, all in an effort to look like the real thing.
The high price of inaction
When your brand is exploited by threat actors, it’s not just an IT problem, it's a business problem.
Without a brand protection strategy in place, organizations risk:
- Loss of customer trust
- Revenue losses due to scams
- Legal and reputational consequences
Without a brand protection strategy, years of brand equity can vanish in moments. Connect with Bitsight Threat Intelligence to learn more about our brand protection capabilities.



