This report shows what’s possible with Bitsight—live ratings, breach alerts, and tiered risk views. It’s a model you can use. Even better—we’ll produce a version specific to your third-party ecosystem, so you can act with confidence.
Threat-Informed TPRM: A New Standard for Supply Chain Security


Third-party attacks: A growing threat
Third-party attacks have emerged as one of the most critical threats in the modern cyber landscape. Adversaries increasingly exploit vulnerabilities within external vendors, suppliers, contractors, and service providers to gain indirect access to target organizations, often with severe consequences. These breaches can lead to significant data loss, operational disruption, regulatory penalties, and reputational damage. As a result, third-party risk management (TPRM) is no longer just an IT concern, it’s a board-level imperative essential to protecting sensitive data and maintaining customer trust.
In our 2025 State of the Underground report, we observed a 43% year-over-year increase in data breaches shared on underground forums, with US organizations representing nearly 20% of all identified victims.
Moreover, we uncovered 2.9 billion unique sets of compromised credentials leaked throughout 2024, marking a sharp rise from the 2.2 billion recorded in 2023. I don’t mean to be dramatic, but that is a HUGE increase. These findings underscore the escalating urgency for organizations to implement robust TPRM frameworks that extend visibility and control far beyond their own digital perimeters.
Why your GRC team needs access to CTI, too
Security Operations Centers (SOCs) are stretched thin. Their mandate is to defend the company’s own assets: patching, monitoring, and responding to threats targeting the enterprise directly. But today’s risks don’t stop at the perimeter. Increasingly, attackers are exploiting vulnerabilities in the extended ecosystem, vendors, partners, and service providers, where visibility is often weaker.
This is where Governance, Risk, and Compliance (GRC) teams come in. GRC is already responsible for monitoring vendor risk and the company’s broader attack surface. With access to Cyber Threat Intelligence (CTI), and powered by AI, GRC teams can move from passive oversight to active defense. They can identify where vulnerabilities in the supply chain might become backdoor entry points and flag them before they escalate into full-blown incidents.
A real-world example: CVE-2025-10035
Recently, a critical vulnerability (CVE-2025-10035) was identified in GoAnywhere MFT, a widely used file transfer solution for moving sensitive data such as financial records, HR files, legal documents, and PII.
- Severity: CVSS score 10.0 (critical) and 9.23 on Bitsight’s Dynamic Vulnerability Exploit (DVE) scale.
- Impact: Similar to the MOVEit breach, it shows how one flaw can trigger a chain reaction of exposures across countless organizations.
Even if your enterprise has patched systems and strong defenses, the real risk lies in your third- and fourth-party vendors. One unpatched vendor instance could compromise your sensitive data and ripple across your entire ecosystem.
Why this matters for TPRM
CVE-2025-10035 underscores the role of Third-Party Risk Management (TPRM) as a frontline defense. Vulnerabilities like this don’t just affect internal systems—they put the entire supply chain at risk.
For GRC teams, this is both a challenge and an opportunity:
- Vendor Assessments: Move beyond check-the-box questionnaires to real-time intelligence on vendor vulnerabilities.
- Prioritization: Use CTI and risk analytics to separate the signal from the noise—focusing on the vulnerabilities most likely to be exploited.
- Proactive Defense: Work hand-in-hand with SOCs, flagging risks in the extended ecosystem before attackers can exploit them.
SOCs can’t fight this battle alone. By integrating CTI into GRC workflows, organizations gain a powerful new layer of defense, one that keeps the backdoor to the enterprise closed, even when vendor ecosystems are under fire.
Key findings
- Third-party data breaches occur when a vendor or supplier system is compromised, leading to unauthorized access to sensitive data. The fallout often includes identity theft, financial fraud, and large-scale data loss.
- Supply chain attacks are a particularly damaging form of third-party exploitation. By compromising trusted vendors, whether through malicious code injection, software vulnerabilities, or tampered physical components, threat actors can efficiently access entire ecosystems of sensitive data.
- Case in point: The MOVEit breach. A critical vulnerability in Progress Software’s MOVEit Transfer product was exploited by the Cl0p ransomware group, impacting more than 2,700 organizations worldwide and exposing the data of over 93 million individuals. This event underscores the systemic risk introduced through vendor dependencies.
The path forward: Threat-informed TPRM
To mitigate these risks, organizations must adopt a threat-informed TPRM strategy that goes beyond compliance checklists. This includes:
- Continuous monitoring of vendor security postures.
- Correlating threat intelligence (IOCs, TTPs, actor targeting) with vendor exposures.
- Enforcing compliance with recognized security standards.
- Prioritizing vendors based on exposure to active threat activity, recognizing that not all vendors are equal.
Bottom line: As attackers increasingly exploit the supply chain, organizations that fail to integrate CTI and TPRM risk being blindsided by the vulnerabilities of their partners. The good news? Our 2025 State of Cyber Risk and Exposure Report shows that security leaders are prioritizing continuous monitoring in the year ahead, as it moved from the #7 investment priority to #1.
Threat actors shifting focus to the supply chain
Rather than attacking organizations directly, adversaries are increasingly targeting third- and fourth-party vendors, where defenses are often weaker. They exploit exposed CVEs, leaked credentials, and unmanaged shadow IT to establish footholds and move upstream.
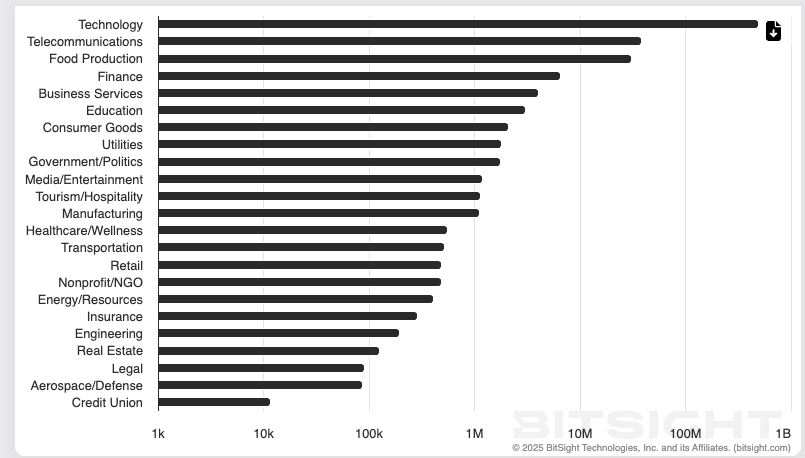
Bitsight’s Groma Explorer highlights this trend, identifying technology, communications, and food as the most frequently targeted sectors through CVEs, with 40% of those vulnerabilities concentrated in the United States. These industries represent critical infrastructure and essential services, making them high-value targets for adversaries seeking both disruption and leverage.
Previously, we highlighted the surge in attacks targeting the manufacturing sector, where adversaries most often rely on Remote Access Trojans and backdoors, ransomware, and spearphishing as primary attack vectors. These techniques allow attackers to quietly infiltrate environments, steal sensitive data, and disrupt operations. But the critical question remains: Is one of your vendors susceptible to an undetected backdoor or a sophisticated spearphishing campaign? Without visibility into these risks, organizations may be blindsided by threats introduced through their supply chain.
Why CTI + TPRM matters
This reinforces why the combination of Cyber Threat Intelligence (CTI) and Third-Party Risk Management (TPRM) is essential. CTI delivers visibility into who is targeting what and how campaigns cascade across the vendor ecosystem. Organizations must move beyond monitoring only their own vulnerabilities to also tracking:
- Which threat groups are targeting their industry and vendors.
- The IOCs and TTPs associated with those actors.
- The specific vulnerabilities and exposures of their supply chain partners.
The real question is not just “Who is targeting us?” but also “Who is targeting our vendors and what are they vulnerable to?” Without this visibility, organizations remain blind to the most consequential risks entering through their supply chain.
Bitsight CTI advantage
Bitsight CTI delivers actionable intelligence by surfacing deep and dark web chatter contextualized to your company and your vendors. With on-demand threat actor profiles, TTP tracking, and alerts for leaked credentials, security leaders gain a proactive view of adversary activity.
Bitsight CTI insight: Most-referenced vendors in threat actor channels
- Tactics observed: ransomware deployment, credential harvesting, exploitation of remote access services.
- Actor-activity mapping: linking threat actor TTPs directly to vendor services: enhanced by EASM tie-ins for external exposure mapping.
- Risk prioritization: demonstrating that not all vendors are equal; those most frequently referenced or exploited by actors demand elevated monitoring and faster remediation.
Outcome: By fusing CTI with TPRM, Bitsight enables organizations to move beyond generic vendor assessments to threat-informed prioritization, ensuring resources are focused where adversaries are most active.
Strategic recommendations
- Enhance Third-Party Risk Management Programs: Develop and operationalize a comprehensive third-party risk management framework. This should include vetting the security of external parties, setting clear expectations for data protection, and continuously monitoring their security posture.
- Adopt the Principle of Least Privilege (POLP): Limit access rights for third-party vendors to only those necessary for their tasks. This reduces the risk of unauthorized access and potential data breaches.
- Invest in Threat Intelligence Tools: Utilize tools that automate vendor risk management and provide real-time alerts on changes in vendor security postures. This proactive approach can help identify and mitigate potential threats before they escalate.
- Conduct Regular Audits and Assessments: Regularly audit third-party operations to ensure compliance with security standards. This includes reviewing System and Organization Control (SOC) reports to identify potential fourth-party risks.
- Strengthen Supply Chain Security: Implement security measures to protect against supply chain attacks, such as verifying the integrity of software and hardware components and ensuring vendors adhere to strict security protocols.