The 2025 State of Cyber Risk and Exposure report reveals why security leaders are under pressure: AI-driven threats, expanding attack surfaces, and misalignment with business priorities. Based on global survey data, it surfaces the root causes behind today’s risk fatigue—and what mature organizations are doing differently.
Dark Web Intelligence for Supply Chains: From Reactive TPRM to Threat-Led Defense
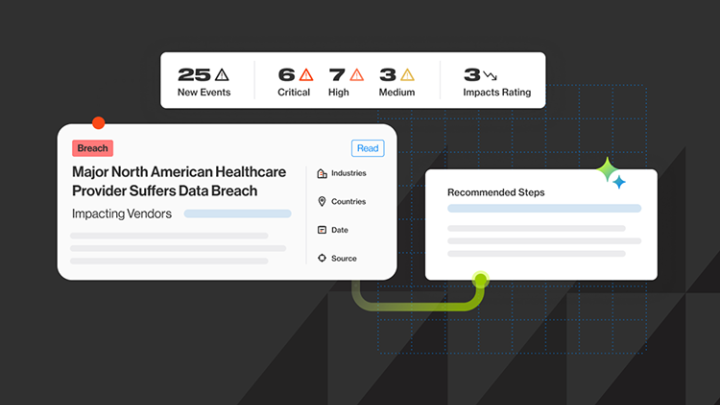

Modern cyberattacks rarely start where defenders are looking.
Instead of targeting the enterprise head-on, attackers increasingly move through sprawling ecosystems of vendors, suppliers, and partners, exploiting trust relationships, weak controls, and delayed visibility.
One such instance was the recent remote code execution (RCE) vulnerability disclosed in SolarWinds Help Desk. If successfully exploited, this flaw could allow attackers to gain unauthorized access to sensitive data and internal resources to include personally identifiable information (PII). Because SolarWinds Web Help Desk operates within enterprise IT environments and integrates with other systems, exploitation of this vulnerability poses an elevated supply chain and third party risk for organizations.
With the convergence of third-party risk and exposure management, it’s become clear that these indirect paths are no longer edge cases: they’re central to how modern attacks unfold. And by the time an organization learns a third party has been compromised, the damage is often already done. For GRC and Third-Party Risk teams, this reality creates an uncomfortable truth: traditional TPRM programs weren’t designed for today’s threat landscape.
The third-party risk blind spot
Most organizations manage third-party risk through periodic assessments, static risk tiers, and vendor self-attestations. On paper, this looks reasonable. In practice, it leaves teams exposed.
Three challenges consistently emerge:
1. Awareness comes too late
Organizations often learn about third-party breaches via delayed disclosures, regulatory filings, or news reports, long after attackers have already gained access. Mean Time to Remediate (MTTR) grows, while business impacts compounds.
2. Risk and security teams are siloed
GRC, TPRM, and SOC teams speak different languages and rely on different tools. Risk insights don’t translate cleanly into security action, and active threats across vendors go unnoticed until it’s too late.
3. Measuring real resilience is nearly impossible
Large vendor ecosystems limit visibility into which suppliers actually pose the greatest risk. Leaders struggle to answer basic questions:
- Are we safer than we were six months ago?
- Are we better than our peers?
- Is our investment in TPRM actually working?
Without real-world signals, resilience becomes a guess, not a measurable outcome. The result? A reactive posture where preventable incidents turn into full-scale crises.
Why Dark Web Intelligence changes the game
To get ahead of third-party–rooted attacks, organizations need to move beyond static scoring and compliance-driven assessments. What matters isn’t just who is exposed, but who attackers are actively targeting right now.
That’s where Dark Web Intelligence for Supply Chains comes in.
Bitsight’s approach brings real-world threat intelligence directly into third-party risk management, connecting exposure, attacker behavior, and prioritization into a single, actionable view.
Why static TTPs fall short during active attacks
Threat actor behavior changes quickly. Activity shifts based on financial incentives, operational pressure, world events, and access to tooling. As these conditions change, three things tend to happen:
1. TTPs evolve, often quickly
During one reported incident, a ransomware operator associated with Akira adapted during an active intrusion after endpoint detection and response (EDR) controls blocked their initial deployment. After realizing traditional endpoints were protected, the attacker pivoted to an unsecured webcam on the same network that lacked EDR coverage. The device was then used to deploy ransomware and encrypt systems across the environment.
This rapid adaptation highlights how threat actors can adjust their approach in real time when defenses interfere with their original plan.
2. Activity levels can spike or disappear (or reappear) with little warning
Well-known threat actors often enter hibernation after significant law enforcement pressure or operational disruption. Activity may drop sharply as infrastructure is seized or key operators are impacted. That pause is frequently temporary. After regrouping, actors often reappear months later with new tactics, new targeting priorities, or a renewed focus on higher impact organizations such as critical infrastructure. A lack of recent activity does not mean the risk is gone, only that it has changed.
3. Targeting priorities shift
Targeting priorities also evolve. After coordinated law enforcement action disrupted LockBit operations in early 2024, activity slowed significantly. When campaigns reemerged in 2025, reporting indicated a shift away from broad, opportunistic attacks toward more sensitive and higher-impact targets, including healthcare and critical services organizations. The change reflected a strategic pivot toward victims where operational disruption and data sensitivity increased extortion leverage.
Because of this, stale or static TTPs do not help during an active attack. When activity is unfolding, teams need accurate, up-to-date intelligence that reflects how threat actors are operating right now, not how they operated yesterday. Threat actors can pivot rapidly and outdated, stale information can result in catastrophe.
Static scoring and compliance-driven assessments can identify baseline exposure, but they do not explain who attackers are actively targeting today, their motivations, or how they are doing it.
Dark Web Intelligence for Supply Chains
To get ahead of attacks stemming from third parties, organizations need visibility into attacker behavior as it evolves.
Bitsight’s Dark Web Intelligence for Supply Chains connects real-world threat intelligence with third-party exposure, helping teams move beyond theoretical risk and focus on what matters now.
Through Threat Insights, teams can:
- See which vendor exposures align with active attacker tactics
- Understand how vulnerabilities and access paths map to current MITRE ATT&CK techniques
- Prioritize third-party risk based on how attackers are exploiting organizations today
Instead of asking, “Is this vendor risky?” teams can ask, “Is this vendor exposed in ways threat actors are actively exploiting now?”
Prioritize what matters now: Dynamic Vulnerability Exploitability (DVE)
Not all vulnerabilities are equal and not all exposed vendors require the same urgency.
Dynamic Vulnerability Exploitability (DVE) scoring helps teams focus on what matters most by prioritizing vendors based on:
- Active exploitation by known threat actors
- Real-world attacker behavior observed in the wild
- Current threat relevance, not just CVSS severity
This allows GRC, TPRM, and SOC teams to align around a shared priority list, directing limited resources toward vendors that pose immediate business risk, not hypothetical exposure.
Gain environmental context: CTI Sectoral Reports
Threats don’t exist in a vacuum.
Sector-specific CTI reports provide broader context on:
- Threat actors actively targeting specific industries
- Common attack paths and techniques observed across peer organizations
- Emerging trends that may affect suppliers within your ecosystem
This helps teams understand not just isolated vendor risk, but how threats propagate across entire supply chains.
Bridging GRC and SOC with shared intelligence
One of the biggest breakthroughs with Dark Web Intelligence for Supply Chains is collaboration.
By grounding third-party risk in threat intelligence:
- GRC and TPRM teams gain credibility and urgency in their findings
- SOC teams receive context they can act on tightening access, enforcing MFA, increasing monitoring, or triggering incident response playbooks
- Risk insights translate directly into security controls, reducing handoff friction and response delays
This is threat-led defense, not score-led reporting.
What’s next: Knowing what is happening
Today, Dark Web Intelligence for Supply Chains helps organizations understand what could happen and where to prioritize based on active attacker behavior.
What’s coming next builds on that foundation: Breach Intelligence, giving teams visibility into when vendors or partners have actually been compromised, so response can begin immediately, not weeks later.
Together, this evolution shifts TPRM from a compliance exercise into a proactive defense capability.
From reactive to resilient
Third-party risk isn’t going away. Supply chains are only growing more complex and attackers know it.
Organizations that continue to rely on static assessments and delayed disclosures will remain reactive. Those that embrace threat intelligence will gain something far more valuable: time, clarity, and control.
Dark Web Intelligence for Supply Chains helps teams stop reacting to vendor breaches and start anticipating them.



