Ransomware, breach sharing, stealer logs, credentials, and cards. What has shifted and how to respond.
Paying the Ransom: A Short-Term Fix or Long-Term Risks?


According to our 2025 State of the Underground report, ransomware attacks rose by nearly 25% in 2024, and the number of ransomware group leak sites jumped 53%. This surge sets the stage for a critical question: if compromised, should you pay ransomware demands or not? The stakes are enormous, including downtime, data loss, brand damage, and legal risk all hang in the balance. Choosing not to pay can send a message that your organization will not give in, potentially making you a less attractive target in the future. But the trade-off can be brutal—losing access to your data, exposing sensitive information, facing regulatory penalties, massive financial losses, and dealing with major reputational and operational fallout. View the latest ransomware stats on Underground Explorer.
As Stephen Boyer, Co-Founder and Chief Innovation Officer at Bitsight, has pointed out, “What’s clear is that these attackers are targeting known vulnerabilities … It’s no longer just an IT problem. A company’s security is starting to have a growing impact over key parameters such as insurance rates, stock price, and board votes.”
The global debate over whether to pay ransom has only intensified as governments take stronger stances. The UK’s recent decision to ban ransom payments for public sector organizations, for instance, reflects a growing desire to break the business model of ransomware groups. As Stephen Boyer noted in his commentary on the ban, prohibitions are symbolically powerful but rarely sufficient on their own. Attackers adapt quickly, shifting tactics and targeting private organizations instead. Real progress comes from prevention — actionable intelligence, visibility, and resilience — rather than from bans or blanket policies.
What are the different levels of extortion?
Ransomware groups have evolved far beyond simply locking files. Today, there are several levels of extortion designed to maximize pressure on victims:
- Single extortion is the original model, where attackers encrypt data and demand payment for a decryption key.
- Double extortion adds a layer of pressure by stealing data before encrypting it and threatening to leak it publicly if the ransom isn’t paid.
- Triple extortion expands the impact even further, with attackers reaching out directly to customers, partners, or employees, or launching Distributed Denial of Service (DDoS) attacks to intensify the disruption.
- Some groups take things even further with quadruple extortion, combining all previous tactics with threats like stock manipulation, false reports to regulators, or targeted harassment of executives.
- Newer campaigns have introduced multi-extortion methods, blending various techniques in unpredictable ways to keep victims off balance.
- There’s also a growing trend of email extortion, where attackers use stolen data to send direct threats to individuals within or outside the organization, aiming to embarrass the company and escalate pressure to pay.
The case for paying ransom
There are several reasons some organizations decide to pay. When backups are unavailable or compromised, paying can be the fastest path to recovery and resuming operations. After an attack, the pressure to get back online is intense, especially from leadership and stakeholders who want business as usual restored as quickly as possible. Paying can sometimes minimize downtime and the financial fallout that comes with prolonged disruption. In highly targeted industries like manufacturing, every hour of downtime can ripple across customers and partners, much like the global semiconductor shortage during the COVID-19 pandemic, which brought production in automotive and electronics to a standstill. In some cases, organizations that refused to pay ended up spending far more on recovery than the original ransom demand. In manufacturing, time truly is money, and every minute of halted production can translate directly into lost revenue.
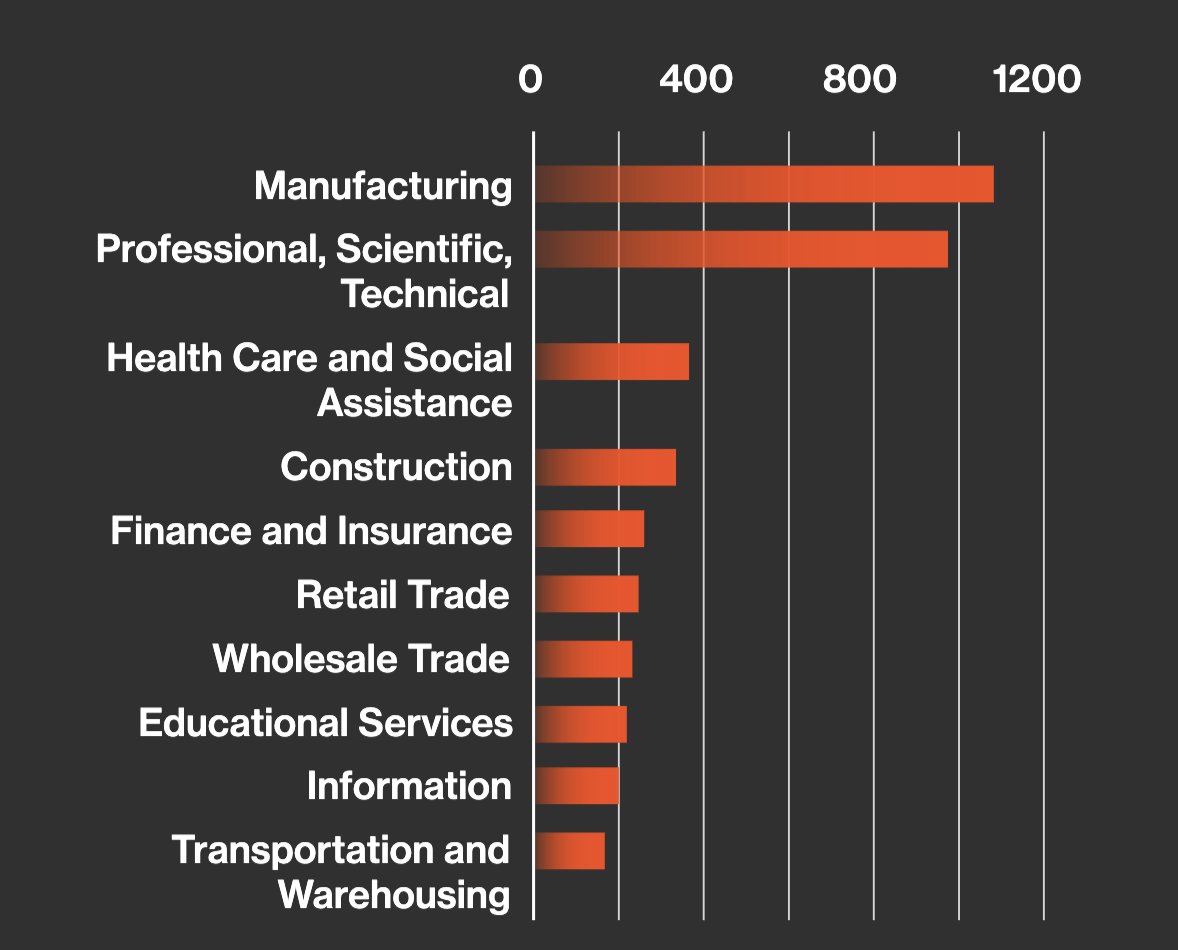
Paying can also help avoid public exposure, embarrassment, or legal consequences if attackers are threatening to leak sensitive information. As Boyer pointed out in his discussion of the UK ransomware ban, outright prohibitions remove the ability to make a rational business decision. In some situations, paying may be the least damaging financial path, especially when recovery costs and reputational fallout exceed the ransom itself.
Threat insight: Bitsight Threat Intelligence (TI) can help assess whether the actor is known to honor payments or has a history of double extortion, getting paid and then leaking data anyway.
The case against paying ransom
Paying the ransom comes with real risks. There is no guarantee the attackers will deliver what they promise. In many cases, victims have paid only to receive a broken decryption key or nothing at all.
Even when a key is provided, decryption tools do not always work as intended. Files can still be corrupted or only partially restored, leaving organizations paying for an incomplete fix.
Every payment also fuels the ransomware economy, reinforcing the idea that these attacks pay off. That money often funds future operations and keeps the criminal ecosystem alive.
Legal and compliance risks are another serious concern. Paying could violate laws if the attackers are linked to sanctioned groups, and in regulated industries, this can result in fines or investigations. According to the HIPAA Journal, roughly 71 percent of ransomware victims choose not to pay, often after weighing these very risks.
While not paying may seem appealing from a morality standpoint, it often costs the victims more in recovery efforts and down time than the initial ransom demand. Still, as the UK’s stance reflects, payment bans aim to break the financial incentive that fuels these attacks. Whether that approach will prove effective remains to be seen. Ransomware groups are resilient businesses in their own right, adapting quickly to maintain profit.
Threat insight: Bitsight can provide threat actor attribution and flag if the group is under sanctions, helping organizations avoid inadvertent legal violations.
Alternatives to paying ransom
If you choose not to pay, or if paying simply is not an option, there are still ways to recover. Preparation and layered defense make all the difference.
Offline or segmented backups are the best starting point. When your backups are separated from your main network or stored offline, you can restore critical data without relying on a criminal’s decryption key. It is a simple but powerful safeguard that can prevent feeding into the ransomware cycle. While this is a good alternative to paying, you are risking the threat actor leaking privileged information like personally identifiable information (PII) thus leading to further legal consequences.
Cloud recovery solutions can also help restore systems and data quickly, especially if on-premise backups are affected. Having a tested cloud recovery plan can mean the difference between a few hours of downtime and several weeks of disruption.
Beyond recovery, an incident response plan with tested playbooks is essential. It ensures your team knows exactly what to do, who to contact, and how to contain the damage quickly when ransomware hits.
Cyber insurance can also help offset some financial losses, but it is not a catch-all. Policies vary widely, and not all cover ransom payments or related expenses, so it is important to understand the details before you need them.
How do ransom payments work?
When a ransomware attack occurs, victims are typically greeted with a pop up directly on their computer containing a ransom note from the attackers. The note often explains that the victims have been attacked and their systems are now encrypted, sometimes even double encrypted, and that access to their files and data has been compromised. It usually includes instructions on how to contact the attackers, how to make the payment, and how long the victim has to respond or pay the ransom before the demand increases or the data is leaked.
Sometimes threat groups even have a countdown on their data leak sites showing how long a victim has left to pay before the information is leaked. Most communication with the threat actors is routed through channels like telegram, privacy focused email providers like proton mail, tuta, and Guerrilla Mail, payments are commonly made through bitcoin or Monero. Certain groups offer instant messaging options on their data leak sites in place of email or telegram communications.
Real world cases
Across industries, organizations have faced ransomware attacks that disrupted operations, exposed sensitive data, and caused significant financial and reputational fallout.
In one incident, a global healthcare organization refused to pay after criminals stole sensitive medical and claims data belonging to millions of patients. The attackers later published portions of the data on the dark web, including diagnostic codes and personal information, after the organization publicly stated it would not meet ransom demands. The case became one of the most high-profile examples of double extortion, where attackers combine encryption with the threat of public exposure, showing how reputational and regulatory damage can persist even when ransoms go unpaid.
A northern European therapy provider experienced one of the earliest examples of email extortion, when attackers stole private therapy records from more than 30,000 to 40,000 patients and then contacted individuals directly. Each victim received an email demanding a small Bitcoin payment—typically around €200 within 24 hours or €500 within 48 hours—in exchange for keeping their personal therapy notes, home address, and identification details from being published online. The messages referenced each person’s unique ID number to prove the data was real, creating panic among patients and outrage across the country. The attack demonstrated a deeply personal and invasive shift in extortion tactics, one that blurred the line between organizational and individual targeting and marked a turning point in how threat actors weaponize stolen personal information.
In the United States, a ransomware attack on a major healthcare payments processor disrupted hospital billing nationwide, with recovery and remediation costs exceeding $20 billion across the healthcare sector. The ripple effect showed how ransomware targeting a single node in the supply chain can paralyze an entire ecosystem.
In another case, a city government refused to pay after attackers encrypted municipal data and disrupted online services. Recovery took several weeks and cost an estimated $18 million in losses, but the organization used the incident as a turning point to strengthen its defenses, implement segmented backups, and improve its overall response capabilities.
Financial analysts have also seen ransomware incidents ripple into credit markets. One major hospital system’s credit rating was downgraded following a cyberattack that interrupted reimbursements and weakened cash flow, underscoring that ransomware has become a financial-risk event, not just a security issue.
Understanding the attacker
To make informed decisions, organizations need to understand who they’re dealing with and how these groups operate. When it comes to ransomware, knowledge is power. Not all threat actors operate the same way, and understanding who you are dealing with can shape your entire response strategy.
Bitsight Threat Intelligence profiles ransomware groups in depth, tracking their tactics, techniques, and procedures (TTPs), their reliability, and their payment histories. These insights help organizations make better, faster decisions during an attack instead of reacting blindly.
Bitsight’s new TTP feature takes this a step further by providing real-time visibility into the behaviors and attack patterns of specific ransomware groups. Security teams can see how a threat actor typically gains access, moves through networks, and deploys their payloads. By mapping this activity to frameworks like MITRE ATT&CK, organizations can better understand where they are most vulnerable and proactively strengthen defenses before an incident occurs.
Knowing whether an attacker typically provides working decryption keys, or if they operate as part of a ransomware-as-a-service (RaaS) model, can inform how you respond. Some groups are known to deliver on their promises (as strange as that sounds), while others vanish after payment. The reality is, threat actors aren't exactly known for their honesty, even when they do decrypt data, there’s no guarantee they will delete the data they’ve stolen or refrain from selling it later. Understanding those patterns helps you evaluate your true risk before taking action.
Conclusion: Making an informed decision
Ransomware isn’t just an IT issue anymore; it’s a systemic business and operational risk that reaches from the server room to the boardroom. While bans and moral arguments dominate headlines, the real opportunity lies in prevention, visibility, and intelligence. Paying might buy time, but it doesn’t solve the root problem. Refusing to pay can be painful in the short term, but it pushes organizations to build long-term strength.
Symbolic gestures may set the tone, but measurable, intelligence-driven action is what will truly shift the balance of power away from cybercriminals. Organizations that invest in resilience, through visibility into attacker TTPs, actionable threat intelligence, and strong governance, will be best positioned to respond decisively and recover stronger.
To learn more about how Bitsight’s new MITRE ATT&CK TTP visibility helps organizations identify and understand ransomware actors before an attack, visit the Bitsight Threat Intelligence platform or connect with our team to see it in action.



