Stealer malware is thriving—especially Lumma and Risepro. These logs fuel ransomware, MFA bypass, and persistent access. It's $10 to compromise an account. Explore this and other insights the data reveals.
Get Ahead of Digital Impersonation with Brand Threat Intelligence


Trust isn’t just a nice-to-have. It’s the foundation your organization is built on, fueling everything from customer loyalty to stronger partnerships and confident employees.
But today, trust must be built across more digital channels than ever: websites, social platforms, app stores, and much more. Every new touchpoint is also a new opportunity for cybercriminals to exploit and damage that trust, with corporate brands and executives alike finding themselves increasingly in the crosshairs of impersonation attacks—and with AI only making those attacks more sophisticated, 90% of cybersecurity leaders say managing their cyber risk is harder today than it was five years ago.
The rising cost of brand and executive impersonation
Impersonation attacks come in many forms, but they all share a common goal: to exploit the trust others place in your brand and employees. Common impersonation attacks include:
- Brand website and social impersonation: Fake domains or social media profiles and typosquatted websites can be spun up in seconds, distributing malware or luring unsuspecting customers into sharing their personal information or credit card details.
- VIP impersonation: Fraudulent executive accounts on social media are increasingly being used to spread misinformation and launch phishing campaigns, while AI deepfakes are being used to gain access to sensitive systems and commit fraud.
- Rogue applications: Like fake domains, malicious apps in public app stores imitate legitimate brand software and trick users into downloading it and entering sensitive details.
- Credential exposure: Stolen executive credentials are often found circulating on underground marketplaces, where they can be weaponized by attackers to break into critical systems. According to our latest State of the Underground report, over 2.9 billion credentials were leaked onto illicit markets in 2024.
The impacts from threats can stack up quickly. Reputational damage hurts customer loyalty and invites negative media scrutiny. Fraud, remediation costs, or regulatory penalties all lead to large financial losses. And executive impersonation creates openings for targeted attacks like phishing and extortion.
Why traditional approaches fall short
Most organizations address threats to their brand reactively, relying on periodic scans, generic threat feeds, or manual takedown requests once incidents are discovered. Such a fragmented approach means there can be any number of blind spots across social media, app stores, DNS records, and the dark web.
Without centralized visibility and contextualized intelligence, security teams often struggle to assess severity of a threat, prioritize their response, or prove impact to leadership before the damage is already done.
A proactive approach to brand defense
Brand Intelligence, Bitsight’s latest Threat Intelligence module, takes a proactive approach to brand defense, looking out for both corporate brands and their executives with AI-powered contextualized intelligence and response workflows.
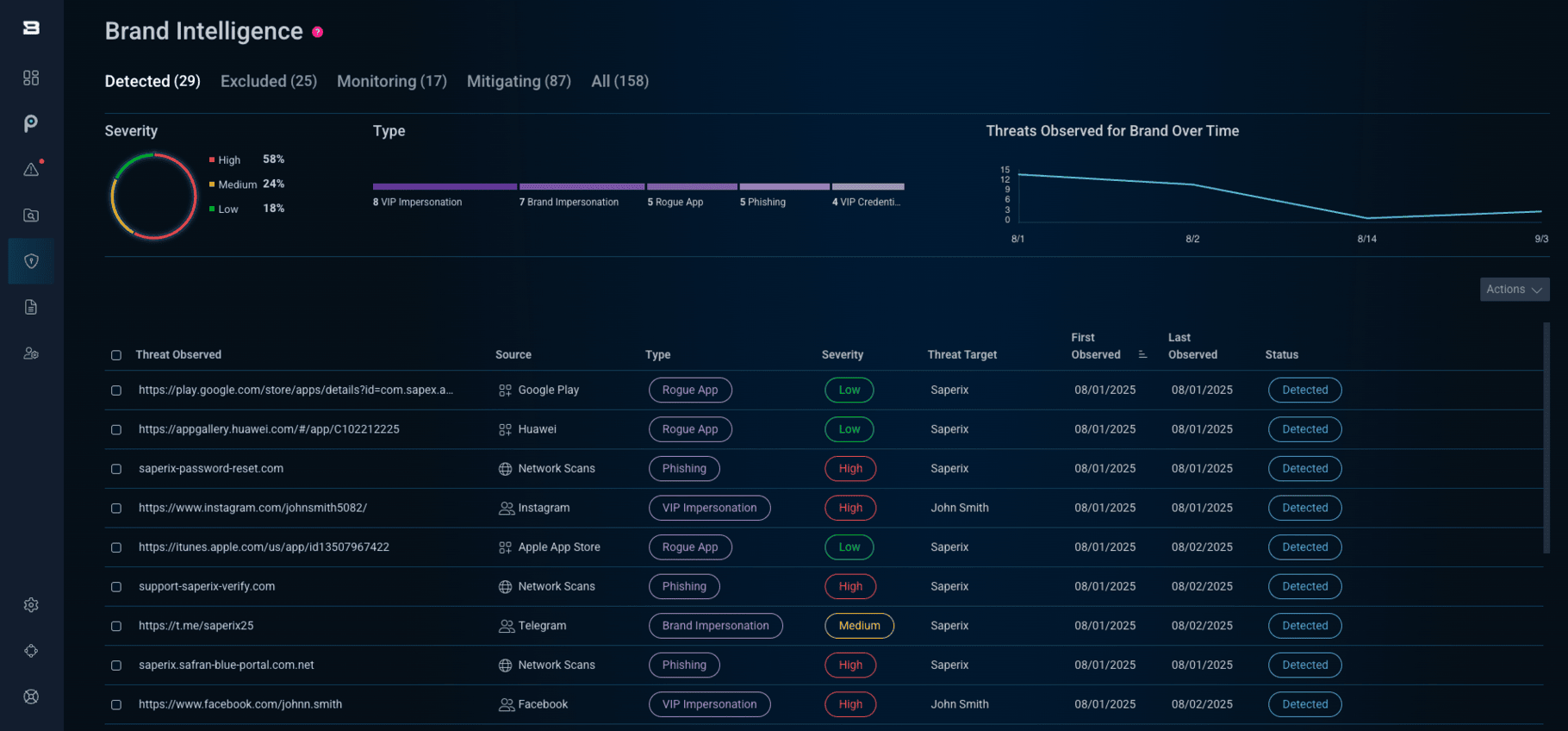
The Brand Intelligence module:
- Monitors and detects threats in real-time across websites, social media, mobile app stores, DNS, and the dark web, from brand abuse to impersonation.
- Scores maliciousness, analyzes risk, and provides contextual intelligence with every detection, so teams can triage faster while making more informed decisions.
- Provides transparent workflows for tracking every incident from detection through mitigation, enabling teams to better collaborate throughout the response process.
- Enables rapid takedown of malicious websites, rogue apps, and impersonation accounts with an 85% success rate — even in hard-to-enforce regions.
When tracking, triaging, and takedown all happen in one place, teams can spot threats early, react quickly, and focus their resources where they are needed most.
Why this matters to security leaders
Brand impersonation is a real business risk with direct — and sometimes permanent — impact on market perception, revenue, and stakeholder confidence, and it’s essential for CISOs and security leaders to be able to communicate these risks clearly.
With enriched intelligence and executive-ready reporting, Bitsight TI Brand Intelligence provides the insights security leaders need to demonstrate the importance of brand protection to the board, and enables organizations to shift from reactive takedowns to proactive defense.
Get ahead of impersonation threats
Bitsight TI Brand Intelligence gives your organization the visibility and control to track, triage, and take down threats before they escalate. Get a proactive brand defense strategy that protects both your organization and your executives, and ensure you’re building the trust your brand and customers deserve.



