The 2025 State of Cyber Risk and Exposure report reveals why security leaders are under pressure: AI-driven threats, expanding attack surfaces, and misalignment with business priorities. Based on global survey data, it surfaces the root causes behind today’s risk fatigue—and what mature organizations are doing differently.
What’s In an Identity? The Executive Attack Surface and Rising Threat of VIP Impersonation


With time, effort, and a blessing from the LinkedIn networking Gods, a high-level executive's identity can be transformative for a company. More than just a name and title, these executives become symbols of authority and trust, someone employees, customers, and partners instinctively follow.
Personas like Elon Musk and Tim Cook instill confidence and belief in their employees and consumers by championing their products and their ethos. Their identities become truly enmeshed with their organization's brand.
The spotlight on leadership cuts both ways. While it builds influence, it also makes executives prime targets for cybercriminals. And when that happens, the very same identities that instill trust are also viewed as the ‘master keys’ to sensitive data, financial assets, and employee influence. And while an organization’s brand may be carefully managed and protected, an executive’s digital footprint is often scattered, spanning professional networks (like LinkedIn and X, formerly Twitter) to personal platforms (like Instagram and TikTok). This creates a broad, fragmented, and often less protected attack surface.
Attackers know this. Executives are targeted precisely because they are the gateway to compromising the broader organization. An impersonated identity becomes the ultimate weapon in the hands of cybercriminals, crumbling the trust that took years to build in seconds, and leaving behind a reputation that may take forever to repair.
The three primary digital threats targeting VIPs
How exactly do cybercriminals impersonate an identity? They use every available piece of information to exploit their targets. From company bios to curated social media posts, they assemble detailed profiles to build convincing fake identities and exploit executive authority. The three primary attack vectors are:
- Personalized phishing
- Public impersonation
- Credential theft
These vectors are easier to exploit than ever before. The rise of AI has made them cheaper, faster, and far more convincing, lowering the barrier to entry for threat actors while simultaneously raising the stakes for organizations.
1. Catching Moby Dick: “Whaling” and AI-powered spear phishing
Whaling is a highly targeted form of spear phishing aimed at senior executives—the “big fish.” Attackers craft hyper-personalized messages that appear to come from trusted sources, often leveraging urgency and authority to bypass normal security checks. With AI, these attacks have reached a frightening new level of realism.
In 2024, cybercriminals used AI-generated deepfakes of a British engineering startup’s CFO and other key executives to manipulate a member of the finance team to transfer $25 million to bank accounts in Hong Kong.
The deepfake replicas looked and sounded like their intended targets, over video conferencing, in a live meeting. Unbelievably, this is the new reality of executive-targeted attacks.
2. Mirror images: Executive impersonation on social and professional media
Cybercriminals frequently create fake profiles (especially on high-reward social platforms like LinkedIn and X) that mirror real executives. These accounts are used to spread misinformation, scam employees and partners, or damage reputations.
In November 2022, during Twitter’s launch of its paid verification system, Twitter Blue, a user paid $8 to create a verified account that looked identical to the official profile of a pharmaceutical giant. The fake account posted a fraudulent message that went viral. It caused the company’s stock price to plummet by $15 billion in a single day, sparking panic and forcing immediate damage control. This attack had detrimental implications for the company.
3. Access for sale: Credential theft and dark web exposure
Attackers steal corporate credentials (username and password) through malware, info-stealer logs, or purchase them from data breaches of third-party services. These data breaches work exceptionally well when an executive reuses the same password (a mistake many of us are guilty of), which is why tracking the personal as well as corporate email of a VIP persona is crucial.
Using the Bitsight Threat Intelligence Investigative Portal, we uncovered a prime example (see below) where corporate access credentials were sold by Initial Access Brokers (IABs).
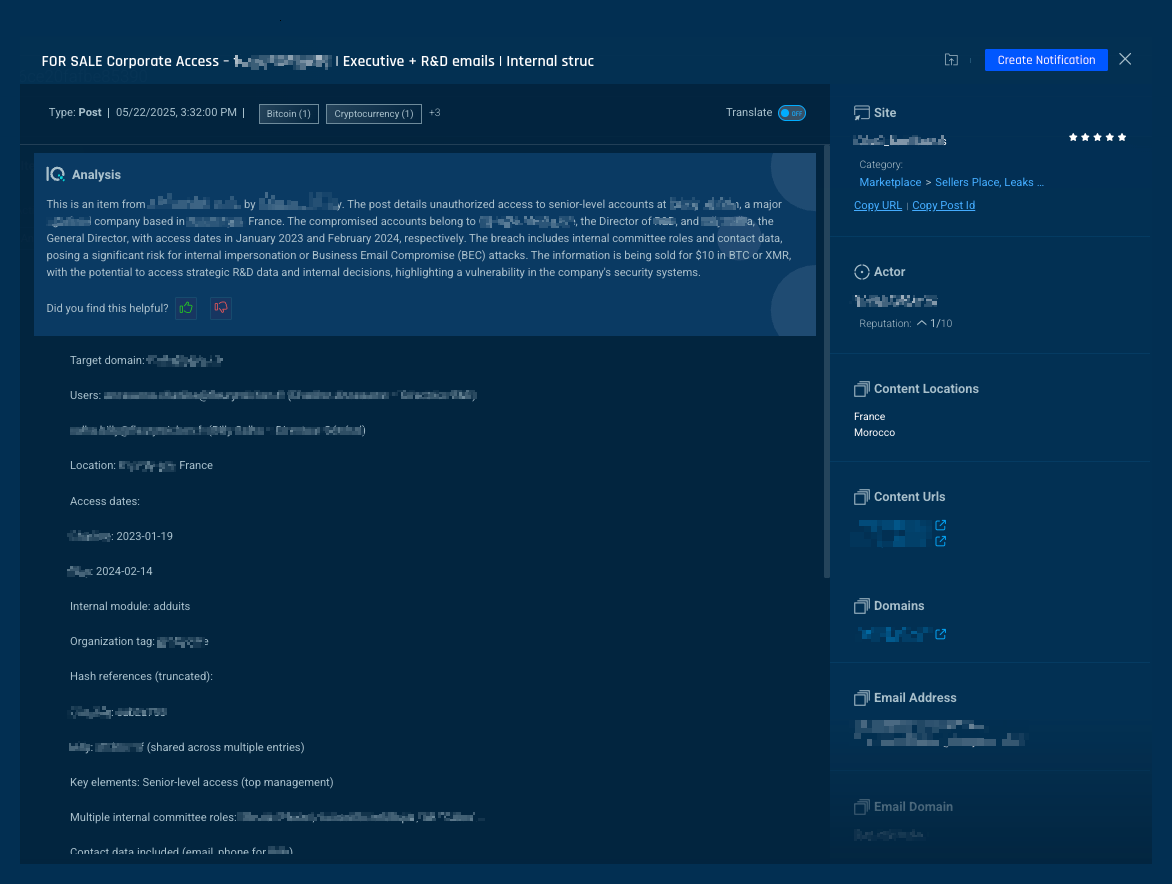
Endpoint compromises have also contributed significantly to the problem: in 2024 alone, 7.7 million logs and 2.9 billion credentials from new malware families like Lumma and RisePro flooded illicit markets. (Read more about this in our State of the Underground report.)
Paying the price: The cost of executive compromise
Unlike a standard data breach, an attack that leverages an executive's identity has a devastating and immediate blast radius that impacts the entire organization. The consequences can include:
- Fraudulent wire transfers and unauthorized payments
- Severe reputational damage when an executive’s name is tied to fraud
- Data breaches and espionage through stolen credential
- Internal chaos as employees scramble to verify every communication
The ripple effects extend far beyond the executive, destabilizing the entire organization.
Protect your leadership to from VIP impersonation
Executive impersonation is easy to launch, hard to detect, and extremely costly to repair. The examples above show why executives are such attractive targets for cybercriminals. By the time a fake profile or leaked credential surfaces, it may already be too late.
Reactive defenses are no longer enough. Organizations need proactive strategies that continuously monitor the digital landscape for impersonations, phishing attempts, and credential leaks, before they are weaponized. Protecting your leadership has become a fundamental part of modern corporate security.
Talk to our team about how Bitsight can help protect your brand and executives.



