Making DORA Strategy Practical: What Cybersecurity Leaders Need to Succeed in 2026




For many cybersecurity teams, the race to comply with the Digital Operational Resilience Act (DORA) is well underway, but clarity and confidence remain elusive. With enforcement set to take effect in January 2026, the countdown is on for financial institutions and their ICT providers to prove that they can withstand and recover from digital disruptions.
The regulation sets high expectations for cross-functional coordination, ICT risk oversight, third-party accountability, and real-time monitoring. Yet many leaders find themselves at the center of the storm, interpreting complex legal frameworks, driving compliance execution, and delivering resilience with limited visibility and fragmented ownership.
DORA isn’t just another box to check; it’s a mandate for sustained operational resilience. The biggest blockers? Translating regulatory language into actionable controls and maintaining continuous visibility across systems, business functions, and vendor networks. Without a unified view of risk, organizations stay reactive—racing against the 2026 compliance deadline instead of building proactive, data-driven resilience that endures.
What cybersecurity leaders say about DORA needs in 2026
Based on current guidance and industry observations, here’s what’s emerging as most critical:
- Clarity in control mapping: Leaders need a way to translate DORA’s regulatory language into actionable, measurable controls, preferably using existing frameworks like NIST CSF or ISO 27001.
- Visibility without silos: Real-time insights across internal systems, cloud environments, and third-party ecosystems are essential. That means connecting asset inventories, vulnerability detection, and incident response in a single, integrated workflow.
- Integrated reporting and oversight: Boards and regulators are asking harder questions, faster. Leaders need executive dashboards, pre-built reporting templates, and automation to reduce manual overhead while maintaining audit readiness.
- A program, not a project: Organizations that are making real progress are those treating DORA as a continuous program with cross-functional ownership instead of a one-time IT initiative.
Fast-track digital operational resilience with Bitsight
For cybersecurity teams navigating these demands, Bitsight offers pragmatic support:
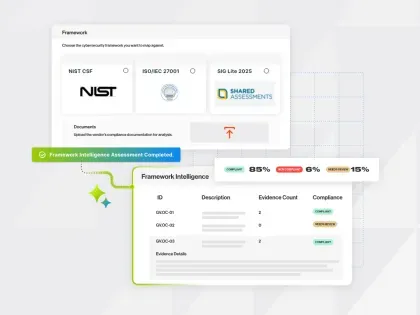
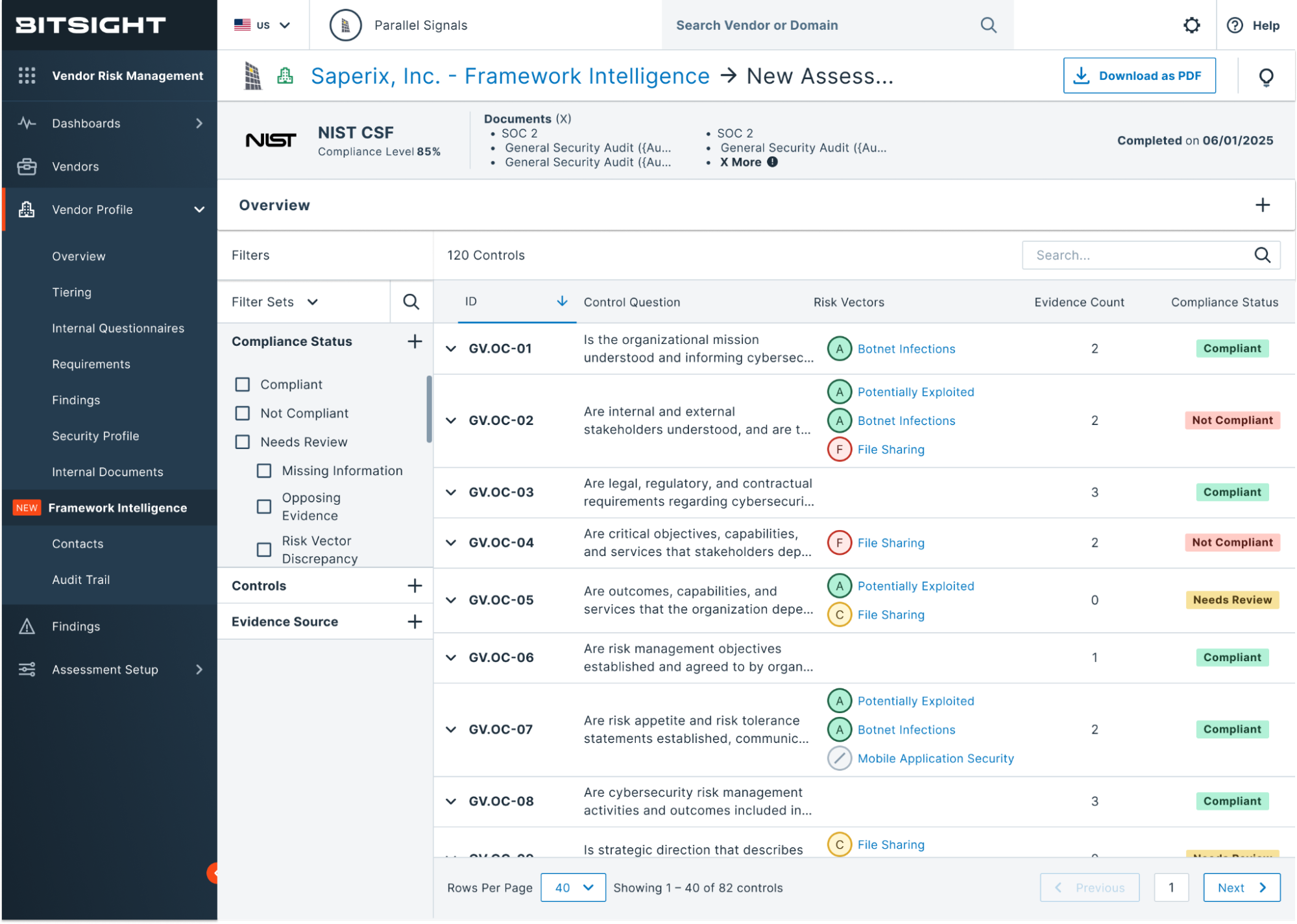
- Bitsight Framework Intelligence - an AI-powered capability across solutions - helps map control evidence to DORA-aligned frameworks, reducing the time and complexity of documentation audits.
- Bitsight Security Performance Management delivers external attack surface visibility and risk trending data that informs ICT risk governance.
- Bitsight Third Party Risk Management solution automates third-party assessments and incident response workflows, enabling proactive vendor risk oversight at scale. The DORA Compliance questionnaire within Bitsight Vendor Risk Management assesses vendors’ DORA compliance on day 1.
- Real-time dashboards and executive reporting bring clarity to DORA alignment and make it easier to communicate risk posture to senior stakeholders.
- Vulnerability Intelligence from Bitsight Threat Intelligence enables collaborative intelligence sharing directly for data-driven vendor discussions.
None of this replaces the need for cross-functional leadership. What it provides security teams with are the tools they need to execute faster, prove progress, and shift from reactive compliance to strategic resilience. Let’s take a closer look at what the first 90 days might look like.
DORA in action: First 90 days with Bitsight Third-Party Risk Management
When it comes to DORA, the hardest part is knowing where to start. Many cybersecurity leaders are balancing the demands of mapping requirements, coordinating across teams, and managing a growing vendor ecosystem.
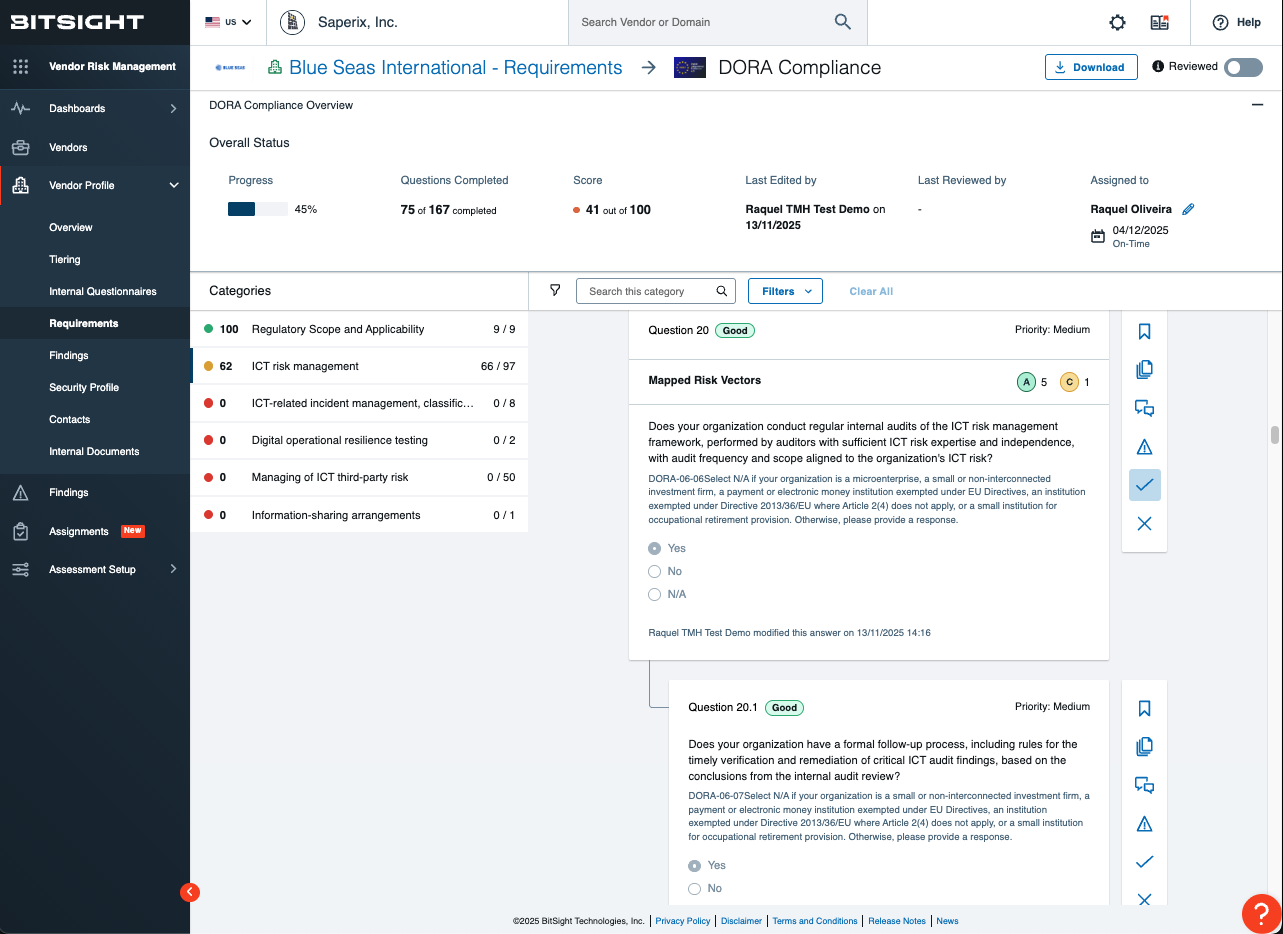
Depending on the maturity of your program and its existing tools, you may not need to rebuild from scratch. The key is to strengthen specific areas across DORA’s five pillars: ICT risk management, incident reporting, digital resilience testing, third-party oversight, and information sharing. Your priority decides where you invest the most, but often the right solution supports multiple pillars. If the vendor ecosystem is your focus, Bitsight Third Party Risk Management (TPRM) will be one such example. Here’s how the first 90 days can look.
First 30 days: Build visibility
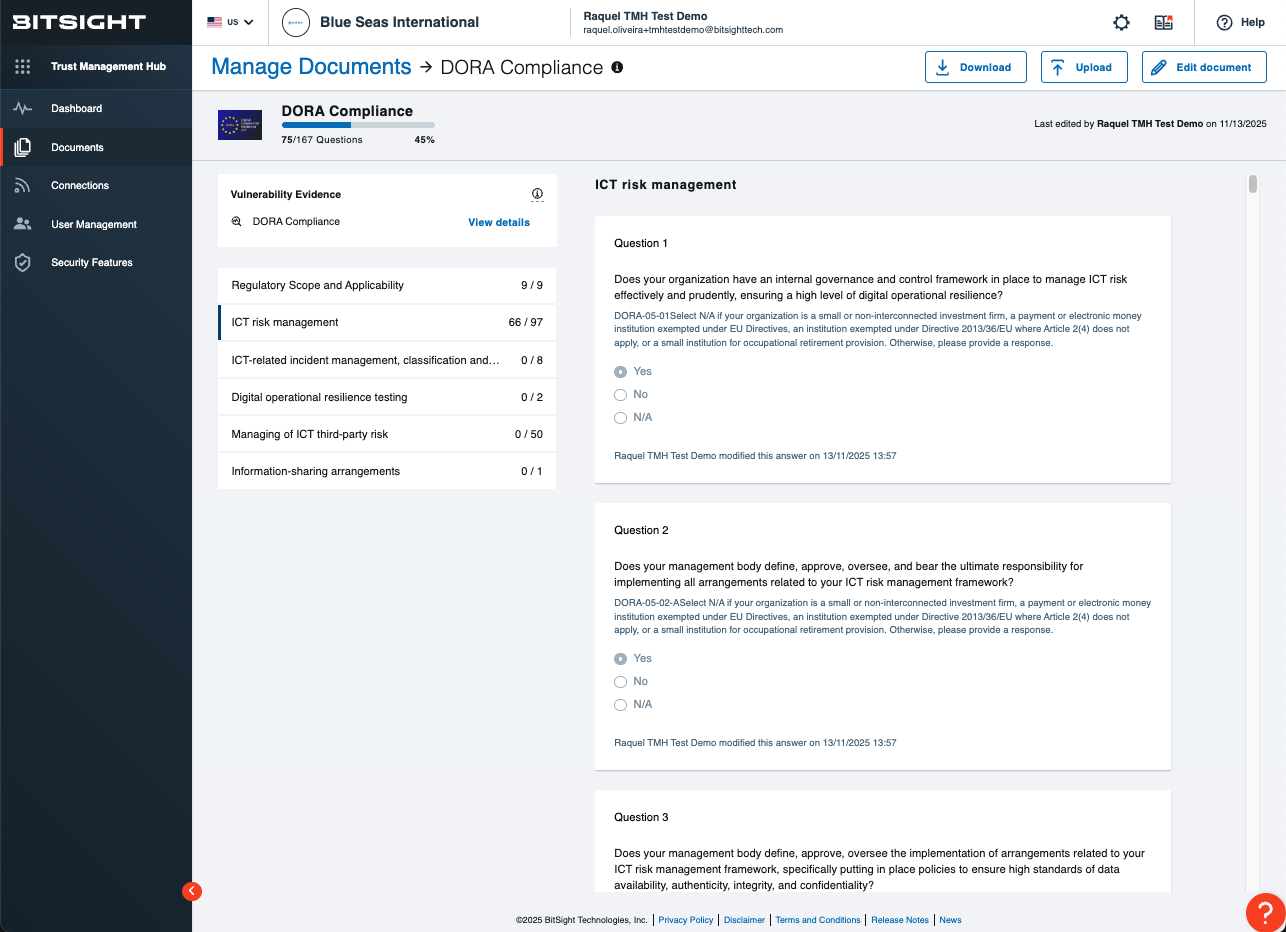
In the first month, focus on establishing your baseline. Bitsight TPRM connects your vendor ecosystem and enriches it with cyber risk data. The Dora Compliance questionnaire in Bitsight Vendor Risk Management allows you to assess vendors in direct DORA lenses, paired with AI-powered Framework Intelligence to map controls into the Dora framework within seconds from vendor artifacts. The continuous risk view from Bitsight Continuous Monitoring enhances your visibility after the point-in-time assessments, maintaining a data-driven, well-informed status of your vendor risk portfolio.
You’ll quickly gain visibility through Continuous Monitoring and begin building your Register of Information with critical vendor details and risk indicators.
31–60 days: Operationalize oversight
Once visibility is in place, it’s time to put governance into motion. Automated assessments and standardized workflows, powered by Bitsight Framework Intelligence, Instant Insights, and a network of 68,000+ vendors, help you evaluate vendor resilience, track remediation, and align documentation with DORA expectations. Reporting dashboards simplify board and regulator updates, transforming fragmented oversight into a coordinated process.
61–90 days: Prove and scale
The final phase focuses on demonstrating control maturity and preparing for supervisory reporting. Evidence mapping connects DORA requirements to supporting documentation, resilience testing validates processes, and regular reporting cadences establish ongoing compliance. By day 90, your organization shifts from reactive compliance to continuous improvement.
Start where you are, but build with intent
DORA isn’t about generating more paperwork; it’s about ensuring that organizations can survive and thrive in the face of ongoing digital threats. With the right tools and support, compliance can evolve from a burden into an enabler of resilience. And that starts with making the invisible visible, across your systems, your supply chain, and your strategy.
Ready to get started? Talk to our team to see how Bitsight can help your DORA strategy.