Explore expert perspectives, data-driven strategies, and the latest trends in cybersecurity, third-party risk management, and cyber threat intel — all from the leader in cyber risk intelligence.
Blog

Featured blog
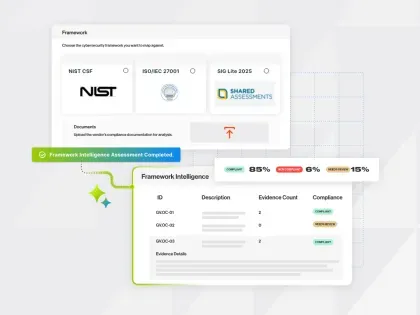
With DORA enforcement set for January 2026, is your compliance strategy ready? Learn how Bitsight makes the invisible visible across systems & supply chain.