With this ebook, we'll help you prioritize which vendors need the most attention with an in-depth security assessment – such as those with low security ratings, or critical vendors that maintain constant contact with your company’s systems.
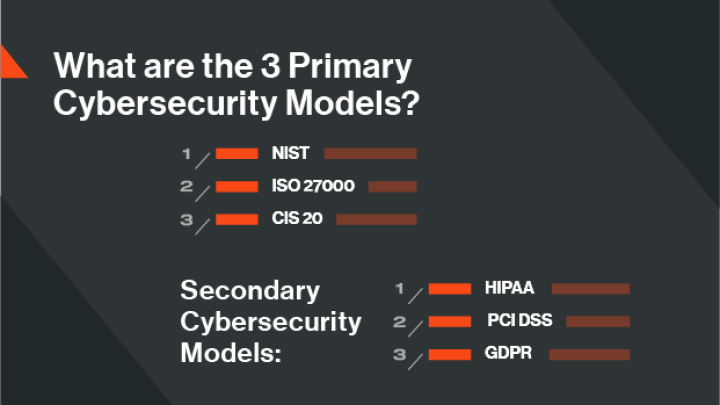
The 3 Most Common Cybersecurity Models
Tags:
Security risk managers often face a lot of the same roadblocks, even if they’re managing programs of different sizes or in different industries. Basing security practices on well-known, and sometimes government-regulated cybersecurity models will mature your program to overcome process inefficiencies.
What is a cybersecurity model?
A cybersecurity model is the cyber security plan or framework used by an organization to measure an organization's level of maturity and ability to identify cybersecurity threats and risk and to guide the selection of policies, strategies, and programs to defend against threats and mitigate risk. A cybersecurity model also includes methodology for assessing the performance of programs to heighten security and minimize risk.
Which security framework is right for you? Are there regulations in your industry that outline a specific framework your security program has to follow? We’ve highlighted three of the most popular primary cybersecurity models that organizations globally follow to reach a maturity program level. We also laid out three of the more common secondary, industry-specific cybersecurity models.
3 Standard cybersecurity models
1. NIST
National Institute of Standards and Technology (NIST) is a cybersecurity framework commonly used by organizations in the US. Establishing and communicating your organization’s tolerance for risk is key to increase program maturity, in accordance to this model. The NIST framework also accounts for the rapidly changing nature of cybersecurity threats, and advises its followers to continuously adjust their monitoring techniques and remediation strategies to match the ongoing threat environment.
The NIST cybersecurity model follows five key phases to reaching a mature security management program:
- Identify - In the first phase, organizations establish a business-wide approach to cybersecurity management, including an understanding of the current risks to the network, what sensitive information lives throughout the organization, and what critical business operations exist that need to be protected from cybersecurity threats
- Protect - The next step in building program maturity according to NIST’s cybersecurity model is to organize and define the defenses necessary to protect the identified critical pieces of your security program.
- Detect - This phase is probably what most organizations dive right into when it comes to cybersecurity program management, including establishing the most effective and encompassing monitoring tools to identify risks efficiently and effectively.
- Respond - The fourth step to increase program maturity according to NISTs cybersecurity model is to tackle the threats to your organization. This is more than just patching your network, but means proper containment of the impact of malicious activity.
- Recover - Just as detection and remediation are important to program maturity, having it in your management process to schedule time to recover and reflect on damages will allow for real program improvements and better protection of your network in the future.
The NIST cybersecurity model acknowledges the current practices most organizations use to protect their network. Instead of starting new, it guides organizations to better use what they’re already doing and add in the right steps to reach program maturity.
2. ISO 27000
ISO 27000 is an international standard, created by the Internal Organization for Standardization (ISO) to highlight best practices for information security management systems. This cybersecurity model is more popular among organizations in the European Union, and focuses attention on the three main areas of a mature cybersecurity management program: people, processes, and technology. The recommendations of the ISO 27000 cybersecurity model is broken down into the following areas for security managers to use best practices to reach program maturity:
- Security risk assessment
- Security policy
- Asset management
- Human resources security
- Physical and environmental security
- Communications and operations management
- Access control
- Information systems acquisition, development, and maintenance
- Information security incident management
- Business continuity management
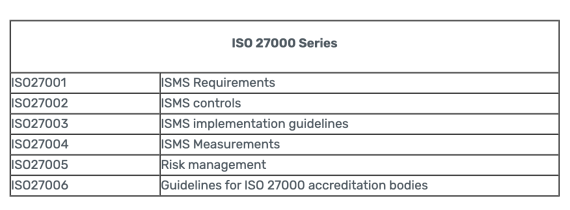
Similarly to the NIST framework, ISO 27000 guides organizations beyond the typical cybersecurity management practices to include greater information security standards and protections. ISO 27000 includes management of critical physical and operational security measures, and is broken down into ISO 27000 Series to get more specific into the actual implementation and design of this cybersecurity model.
3. CIS 20
The final cybersecurity model many organizations follow to reach program maturity is the CIS 20. Designed by the Center for Internet Security after the US defense industry experienced a data breach in 2008, the CIS 20 is a series of 20 controls deemed critical to protect an organization’s network from expansive cyber attacks.
The CIS 20 is broken down into 3 main categories of controls:
- Basic Controls (like inventory control, continuous vulnerability management, and controlled employee privileges)
- Foundational Controls (like malware defenses, data protection, or wireless access controls)
- Organizational Controls (like training programs and creation of incident response teams)
The CIS 20 cybersecurity model is designed to be all-encompassing, and require extreme attention and care to an organization’s cybersecurity management process.
3 Secondary cybersecurity models
Besides the three most popular cybersecurity models listed above, there are also industry-specific secondary frameworks organizations may be required to, or choose to follow.
1. HIPAA
Specific to the healthcare sector, the Health Insurance Portability and Accountability Act (HIPAA) was created to require healthcare organizations to protect the privacy and highly sensitive information of patients. HIPAA extends to organizations beyond healthcare when it comes to employee health information collected for insurance or medical leave purposes, but the cybersecurity model mainly applies to healthcare organizations that need to follow three key components:
- Administrative requirements
- Physical security requirements
- Technical security requirements
2. PCI DSS
The Payment Card Industry (PCI) Data Security Standard (DSS) regulations focus on the protection of consumer payment information stored by card processing transactions. There are 12 requirements for an organization to be deemed PCI DSS compliant, which is required by all companies that process or transmit cardholder information as part of their business.
3. GDPR
The European Union’s General Data Protection Regulation (GDPR) focuses on the requirements of organizations in the EU to protect consumer data. The cybersecurity model also includes data protection for information transferred from an EU-based organization to somewhere else geographically. The GDPR requirements include:
- Lawfulness, fairness and transparency
- Purpose limitation
- Data minimisation
- Accuracy
- Storage limitation
- Integrity and confidentiality (security)
- Accountability
What is cybersecurity program maturity?
A mature cybersecurity program is one where the processes, tools, and people are all aligned and working together so that the program is successful at mitigating risk. A mature program has buy-in from executive leadership, but also has goals that are felt across the entire organization. There will always be risks and vulnerabilities that plague mature cybersecurity programs, but there are actionable and agreed upon plans in place that partners and vendors agree to when working with a mature cybersecurity program.
The specifics of program maturity boil down to the cybersecurity model chosen and what is counted as mature for each model. Cybersecurity models also can outline the order in which different steps should happen to reach program maturity.
What is a third-party risk cybersecurity model?
A third-party cyber risk management framework or model identifies the risk in vendor ecosystems and outlines the strategy, people, processes, and technology required to mature a program and better mitigate risk in third-party networks.
When it comes to managing third-party vendors, choosing and adhering to the appropriate cybersecurity model can help you better mitigate risk throughout your entire vendor ecosystem. Third-party risk management (TPRM) teams often face great uncertainty about how to focus their time, money, and energy. Arranging your program to follow a superior cybersecurity model for third-party risk can help risk managers more clearly understand the risks posed by vendors and more effectively prioritize resources and budgets to mitigate them.
Maturing your cybersecurity model for third-party risk
The Deloitte Enterprise Risk Management Evaluation helps organizations discover where they rank in terms of maturity of their TPRM program. Following the Deloitte-based structure, Bitsight offers companies an analysis of their existing vendor risk management tools and processes in four categories. Based on the responses within each area, an organization can identify where they fall on the maturity scale and where they have opportunities to improve specific processes.
The four categories Bitsight analyzes include:
- Strategy and governance. How well developed is the cybersecurity policy and governance around third-party risk management? Companies with agile third-party risk programs consistently document and apply policies across their entire organization and their third-party ecosystem.
- People. Is there a team or department focused solely on vendor risk or a leader who champions TPRM to the board? Companies that lack mature programs typically don’t have dedicated resources working on TPRM and struggle to engage their leadership team or get buy in from across the organizations.
- Process. Is analysis of third-party risk restricted to the onboarding process or is the security posture of vendors continually revisited? With Bitsight for Third-Party Risk Management, companies can continually monitor their vendor’s security ratings, as well as implement other best practices to create a more mature TPRM program.
- Technology. How is onboarding, ongoing, and offboarding information collected, and is the process automated? Companies with mature cybersecurity models for cyber security risk management automate data collection and analysis to dramatically improve efficiency and ensure data accuracy.
By evaluating and ranking each of these four categories, Bitsight can help you identify the maturity level of your TPRM efforts, target areas for improvement, and allocate resources to build the most effective risk management program. With Bitsight’s tried-and-true cybersecurity model for TPRM, organizations of all sizes, sectors, and security levels can achieve their maturity level goals.
Conclusion
There are many cybersecurity models for organizations to both choose from, or to be required to follow. It’s also important for a lot of businesses to become certified for following a specific framework to best represent themselves compared to their competition.
Bitsight customers use their access to Bitsight Security Ratings and expansive cybersecurity monitoring technology to comply with cybersecurity models and maturity frameworks. To get started complying with regulations or maturity frameworks in your industry, request a Bitsight demo today.