Download our vendor portfolio risk report sample to get an exclusive look at the actionable reporting capabilities third party risk management teams can use to reduce critical portfolio risk.
Bitsight Observations Into Hafnium Part Four: Who Is Still Vulnerable?

The unfolding Hafnium attack is the latest event in the trend of cyber events. CISO’s are starting to recognize that enterprise cyber security is being redefined to mean me and all my suppliers, or the combination of first and third party cyber risk is enterprise risk. NotPetya demonstrated that breaching a small accounting firm could cost a firm like Merck over $1B in damage.
What lessons is the Hafnium attack teaching?
What Happened?
On Mar 2, threat actors attributed to a new Chinese APT Group, dubbed ‘Hafnium’ by Microsoft, exploited four Exchange server zero-day vulnerabilities. Industry participants have nearly uniformly reported this as a massive attack.
|
Observation Date |
March 10 |
March 8 |
March 11 |
March 11 |
March 15 |
|
Total Exchange Servers with OWA Observed |
320,000 |
Not avail |
400,000 |
Not avail |
18,000 |
|
Vulnerable IP’s |
100,000 |
125,000 |
82,000 |
68,500 |
2,500 |
|
Mapped Vulnerable Organizations |
14,000 |
Not avail |
Not Avail |
8,911 |
173 |
Where are we now?
In a March 15 update, Bitsight reported detecting over 300,000 Exchange servers, identifying nearly 65,000 that were vulnerable and over 14,000 (4%) that were still exploited. Twenty-one days after the attack was reported, the number of vulnerable systems has dramatically reduced indicating that organizations are steadily patching systems.
However, as of March 22, 28,500 vulnerable servers remain unpatched. But, patching alone does not remediate downloaded malicious files. The number of patched and exploited servers along with unpatched and exploited servers remains alarmingly high. These organizations are at risk of additional exploitation, including ransomware attacks. These organizations pose a digital supply chain threat to customers and partners relying on them for services.
We have detected and are now blocking a new family of ransomware being used after an initial compromise of unpatched on-premises Exchange Servers. Microsoft protects against this threat known as Ransom:Win32/DoejoCrypt.A, and also as DearCry.
— Microsoft Security Intelligence (@MsftSecIntel) March 12, 2021
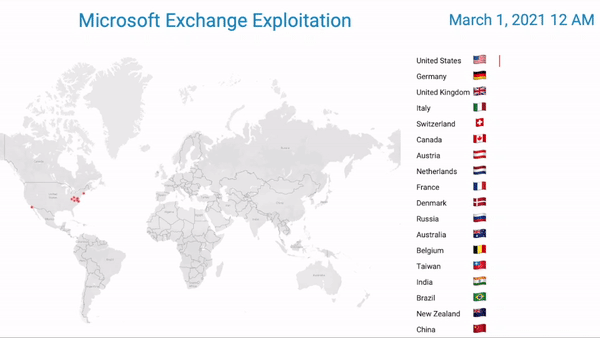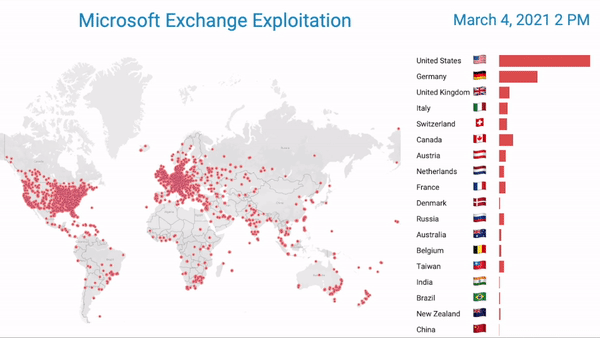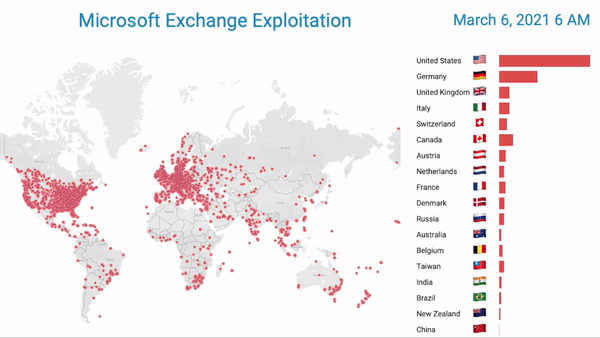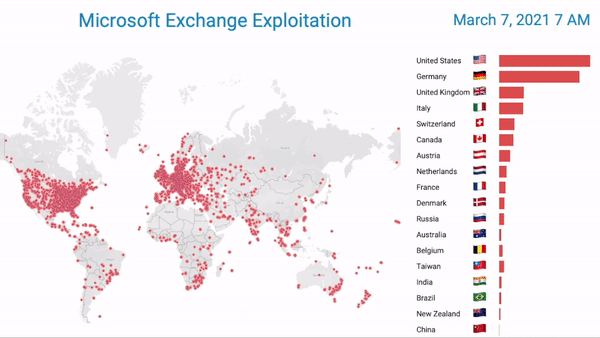

Caption: Bitsight research observes the first seven days of Hafnium’s global impact. Each dot represents an exploited exchange server ] It created significant disruption and continues to pose a significant threat to organizations that were exploited. Importantly this attack, while attributed to a state actor, opened the door for other opportunistic cyber crime actors to exploit the unpatched vulnerabilities.
It is important to keep in mind a truth put forward by security experts and regulators: across all geographies, organizations must confirm that the third parties they do business with have also performed forensics.
The Long Tail Risk
Bitsight’s research has reported that when attacks like Hafnium occur there are remediation laggards. The laggard group is similarly represented by large and small organizations. Instead of size or resources, we can speculate that it is an organization’s commitment to daily security performance excellence within their own organization and across their digital supply chain. Organizations, large and small, who are slow to patch represent the soft spot within digital supply chains, and can represent a third-party threat within the digital vendor ecosystem.
If you imagine that sensitive data about your company could be found in your vendors' email systems, maybe you should know which of them are at risk.
The potential exposure is concentrated mostly in the technology sector, with additional risk from business services, as seen in the table below. It can be inferred that the bulk of these companies are vendors within the digital supply chain, and thus their customers are in some way exposed.
|
Sector |
Percentage |
|
Technology |
28.8% |
|
Manufacturing |
12.1% |
|
Government/Politics |
11.6% |
|
Business Services |
11.0% |
|
Healthcare/Wellness |
9.4% |
This highlights the need for security and third-party risk leaders to rethink enterprise risk to encompass their third parties.
Observations and Lessons
Looking back on prior events such as SolarWinds, NotPetya, BlueKeep, WannaCry, and now Hafnium the question truly is what are the key lessons learned from these events.
For CISO’s
- Hafnium was a massive attack. Visibility across the extended enterprise is critical.
- Ask the right questions and focus on remediation. Checking for patches alone is not enough, as patched systems may still have been exploited. CISO’s must ask if systems are patched and the exploit remediated.
For Vendor Risk leaders
- Vendor Risk Management programs should adapt their own version of Zero Trust.
- Subjective attestation are not reliable. Therefore, programs should implement their own version of “never trust, always verify”
- Revisit the definition of critical vendors who require continuous monitoring
For Business leaders
- Regulatory cyber risk due diligence standards are evolving. Regulators expect data owners to preemptively test existing security measures within the organization and perform ongoing monitoring of its supply chain.
- Hyper-connected organizations benefit by raising the bar on mutual accountability over security performance. Cyber supply chain risk is a “we are they” problem. Better security performance, stronger vendor risk management programs, higher assessment standards all result in better mutual assured resilience.
- These events are changing cyber insurance underwriting
- Cyber insurers are increasingly concerned about vendor cyber risk impact on their insureds posture. Insurers are increasingly scrutinizing vendor risk during the underwriting process. In addition to expecting insureds to manage vendor risk through contractual liability and insurance retention, insurers are expecting insureds to also better control their vendor risk. Most cyber events result from known exploited vulnerabilities.

Get A Free Attack Surface Report
Request your free custom report and see how you can start reducing your cyber risk exposure across your digital ecosystem: cloud assets across all geos & subsidiaries; discover shadow IT; security risk findings; and more!


