Request your free custom report and see how you can start reducing your cyber risk exposure across your digital ecosystem: cloud assets across all geos & subsidiaries; discover shadow IT; security risk findings; and more!
Bitsight Analysis of SolarWinds Orion — Part 2: Declining Prevalence

In light of the cyber attack targeting SolarWinds, security and risk professionals are working to identify instances of the Orion software within their organization -- including their broader partner ecosystem -- and reduce their exposure. How responsive have organizations been to the SolarWinds hack?
Bitsight is leveraging our continuous collection of security performance and software usage data on 260,000 organizations across 24 sectors to track the prevalence of Orion -- including trojanized versions of the software -- and observe steps taken by organizations to reduce their exposure.
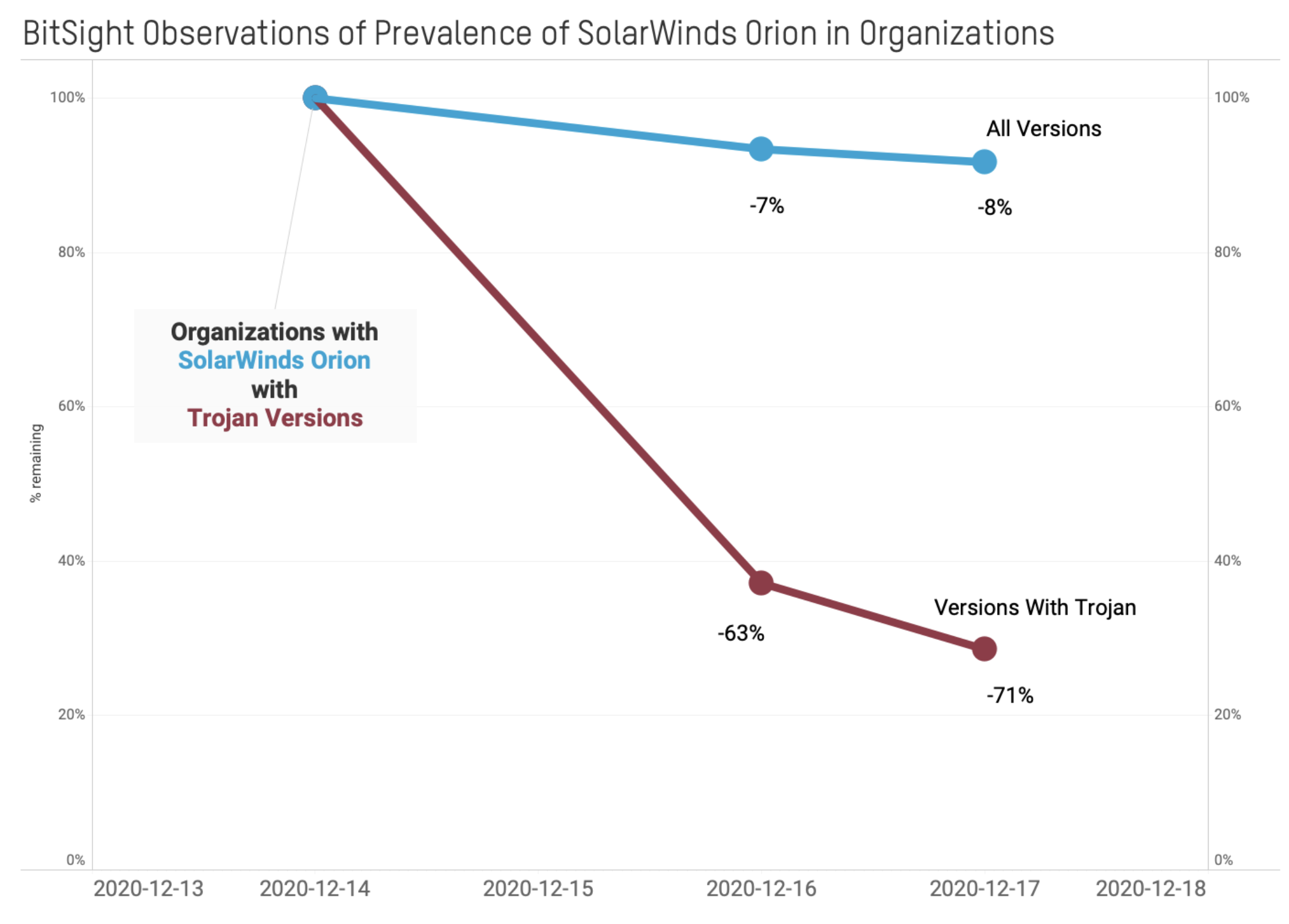
Bitsight observes that many organizations with publicly exposed trojanized versions of Orion have acted over the last 3 days to remove those instances from the Internet or to patch them:
- Since Dec. 14, we have observed a 71% decline in organizations with publicly exposed trojanized versions of Orion
- We observed a 63% decline in organizations with publicly exposed trojanized versions of Orion on Dec. 16
- We observed an additional 8% decline in organizations with publicly exposed trojanized versions of Orion on Dec. 17
While these efforts may shut off further penetration, organizations once using trojanized versions of Orion may have been compromised since March; FireEye and Microsoft have suggested that a smaller number of organizations may have been impacted.

Organizations are also acting to remove their instances of SolarWinds Orion from the Internet, likely bringing the software inside the firewall to reduce potential exposure. The rate that organizations are removing these instances is significantly less than the trojanized version -- likely due to the fact that Orion is a critical piece of software for many organizations:
- Since Dec. 14, we have observed an 8% decline in organizations with publicly exposed SolarWinds Orion
- We observed a 7% decline in organizations with publicly exposed SolarWinds Orion on Dec. 16
- We observed an additional 1% decline in organizations with publicly exposed SolarWinds Orion on Dec. 17
Bitsight recommends that security and risk professionals immediately determine the prevalence of SolarWinds Orion within their organization and broader third party supply chain in order to mitigate the risk of exposure. Given the significance of this incident, Bitsight recommends reporting any potential exposure to senior executives and the board as soon as possible. For additional information, please read our earlier Part 1 analysis of the SolarWinds breach.

Third party vendors present major cybersecurity risks, even for companies with strong network protections.
Learn how to create a scalable & sustainable vendor risk management program to see what it takes to create a VRM program that’s ready and able to stand up to our interconnected economy


