Bitsight Observations Into HAFNIUM Attacks, Part Three: Exploitation and Vulnerability Persists


Organizations around the globe continue to address the fallout from the Microsoft Exchange Server zero-day attacks. It was recently announced that hackers may now be exploiting the vulnerabilities in Exchange to drop ransomware into vulnerable systems via backdoor attacks (or Web shells). There is significant urgency for organizations to update their systems and patch immediately to stop these backdoor attacks that originated with Exchange.
Bitsight’s latest global analysis shows that thousands of organizations have been successfully exploited as a result of Microsoft Exchange Server vulnerabilities. Encouragingly, the number of vulnerable systems continues to drop at a healthy rate since our original observations from last week, suggesting that organizations are steadily patching systems. However, thousands of vulnerable systems remain unpatched around the globe, placing those organizations at risk of a damaging ransomware attack or additional exploitation. In addition, there remain thousands of servers that remain exploited with backdoor attacks despite being patched.
Bitsight’s latest observations from March 15-16, 2021 include:
- 316,401 Microsoft Exchange Servers observed
- 64,931 Exchange Servers observed to be vulnerable
- 14,112 unique Exchange Servers detected with backdoors (Web shells)
- 26,085 total Web shells observed on Exchange Servers, confirming that some Exchange Servers have multiple Web shells installed
- 5,537 Exchange Servers with observable, backdoor attack driven vulnerabilities, that have also been patched, implying that those administrators have yet to perform forensics or remediation of their systems
Bitsight finds that:
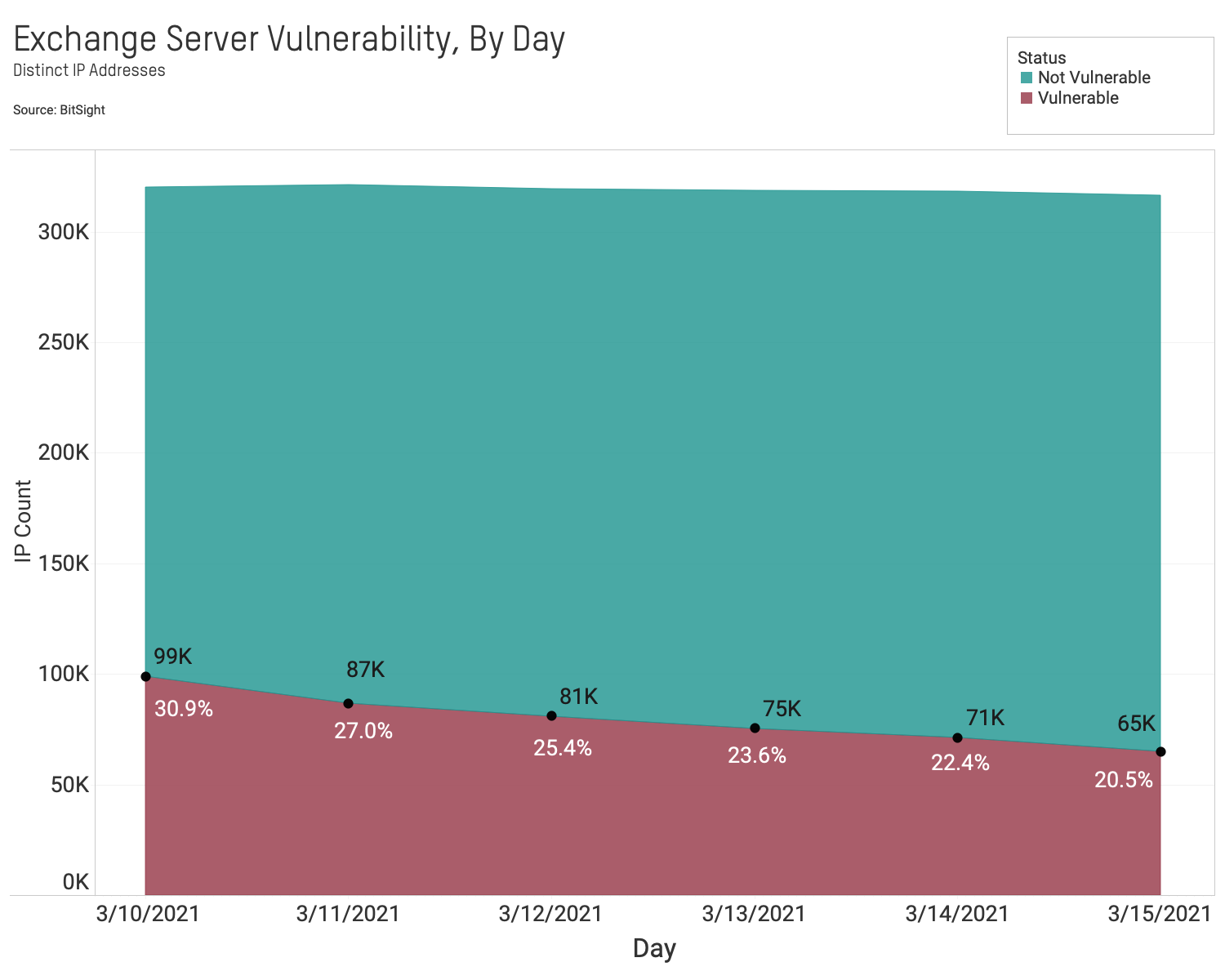
- 20% of exposed Exchange Servers remain vulnerable. The rate of observable patched Exchange servers is improving. Nearly 65,000 out of 316,000 (20%) observed Exchange servers remain vulnerable as of March 15. This is down from 99,000 (30%) observed vulnerable servers on March 9.
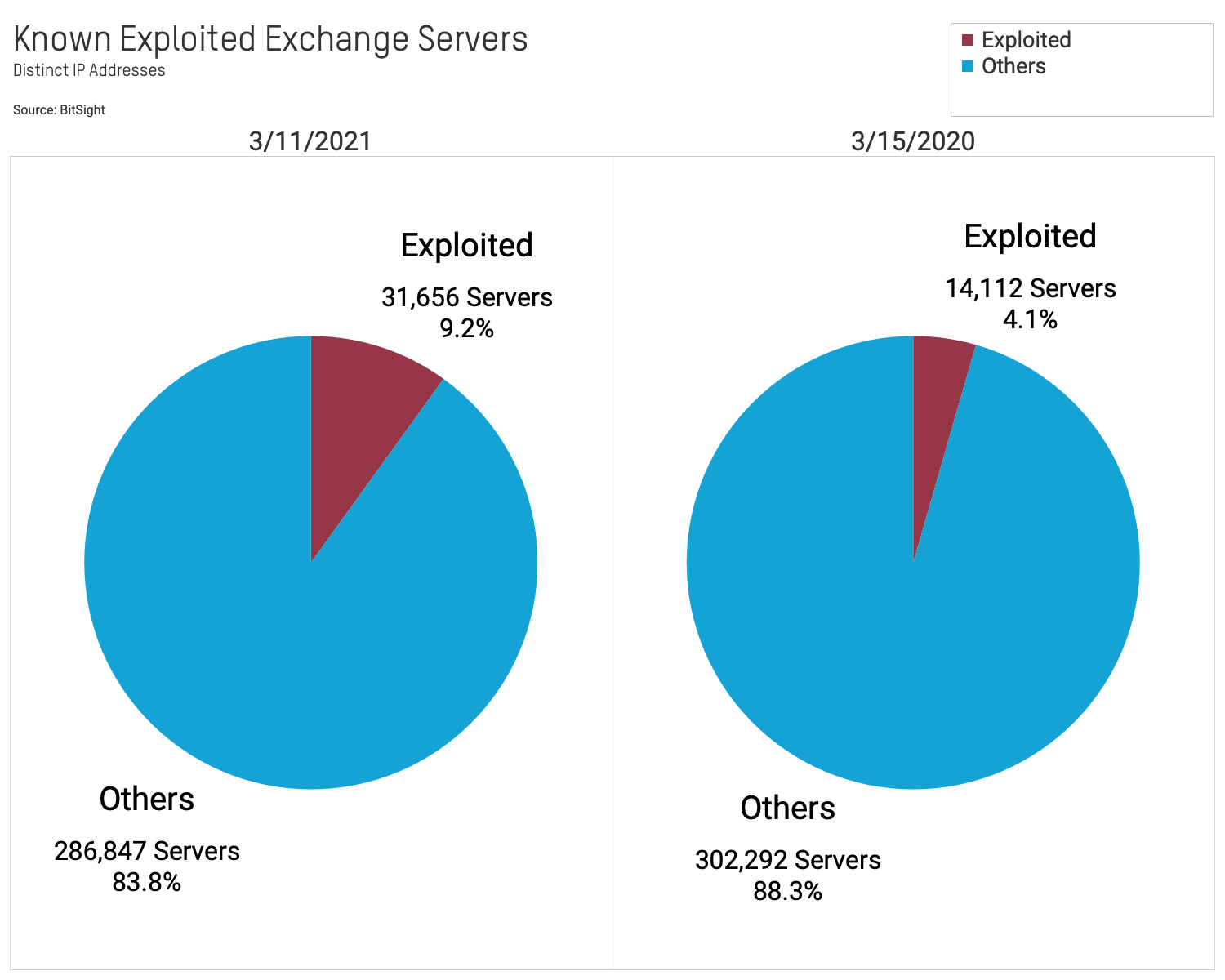
- 4% of exposed Exchange Servers are currently observed with backdoor attack points. There remain a significant number of currently exploited Exchange servers. More than 14,000 (4%) observed Exchange servers are currently exploited. This is down from more than 31,000 (9%) on March 11.
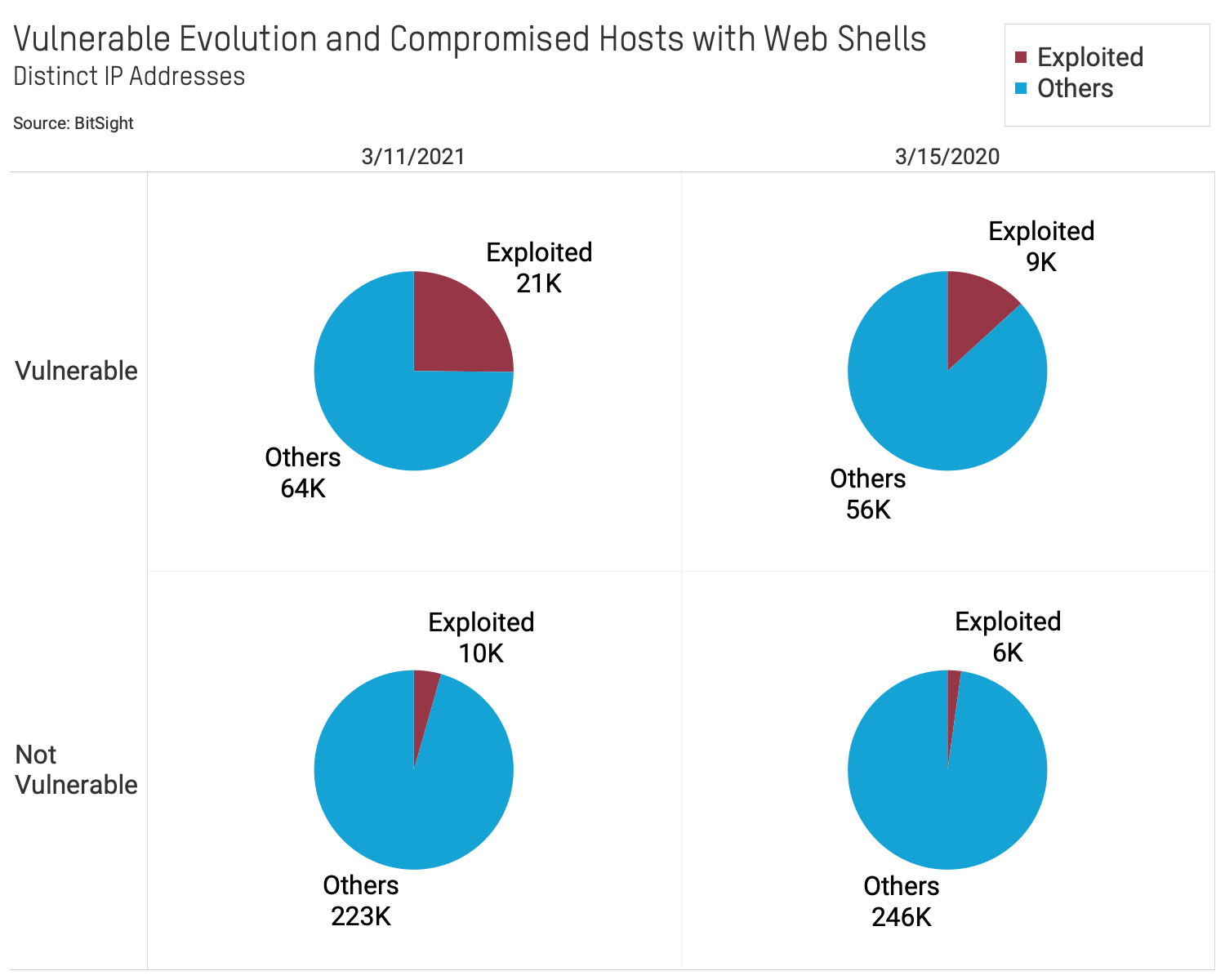
- Nearly 1 in 2 exposed Exchange Servers that contain a backdoor have also been patched. More than 5,500 observed patched systems still have a backdoor attack point, implying that those administrators have yet to perform incident response of their systems.
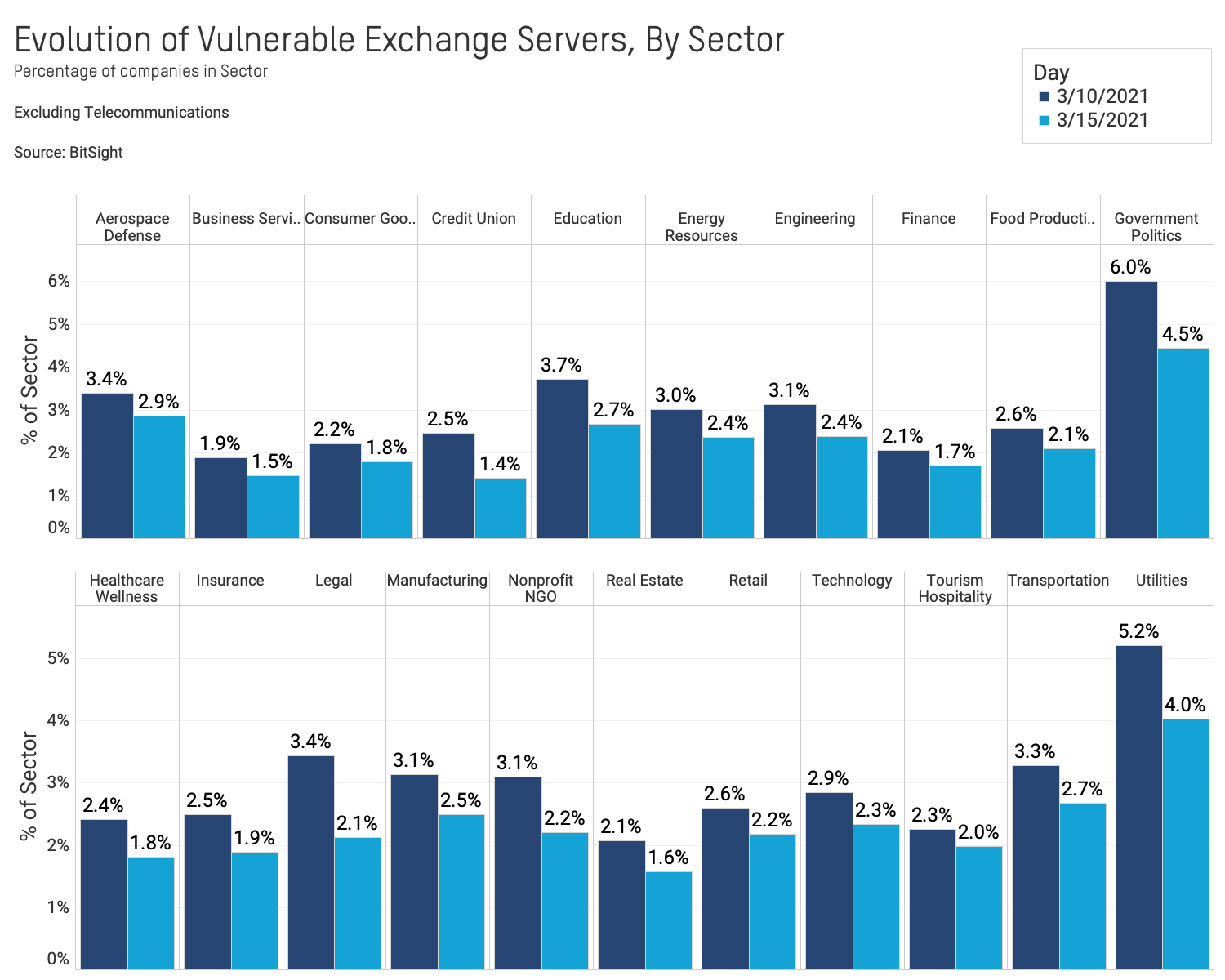
- The rate of patching Exchange Servers varies by sector. The Government (4.5%) and Utilities (4%) sectors still have the highest rate of vulnerable Exchange servers, though this has improved since March 10. Other sectors show slight improvements in patching vulnerable systems.
These findings are based on Bitsight’s continuous data collection. As part of our telemetry, Bitsight continuously interacts with all Internet-accessible systems to understand what services they have accessible on their network and understand their current configurations. We are able to detect Microsoft Exchange Servers through this activity, and when we do, we can assess those systems for certain vulnerabilities and insecure configurations. The data Bitsight observes is made possible through using information and tools made available by Microsoft and other members of the security community.
1) 20% of exposed Exchange Servers remain vulnerable.
The rate of observable patched Exchange Servers is improving. Nearly 65,000 out of 316,000 (20%) observed Exchange Servers remain vulnerable as of March 15. This is down from 99,000 (30%) observed vulnerable servers on March 9.
2) 4% of exposed Exchange Servers are currently observed with a backdoor attack vulnerability.
There remain a significant number of currently exploited Exchange Servers. More than 14,000 (4%) observed Exchange Servers are currently exploited. This is down from more than 31,000 (9%) on March 11. Because Bitsight only observes a subset of all possible backdoors, this number is a lower bound for the total number of systems that have been compromised.
3) Roughly 1 in 2 exposed Exchange Servers that contain a backdoor have also been patched.
More than 5,500 observed patched systems still have a backdoor attack vulnerability, implying that those administrators have yet to perform incident response of their systems.
4) The rate of patching Exchange Servers varies by sector.
The Government (4.5%) and Utilities (4%) sectors still have the highest rate of vulnerable Exchange Servers, though this has improved since March 10. Other sectors show slight improvements in patching vulnerable systems.
What Should Organizations Do?
Based on analysis and public reporting, Bitsight estimates that the majority of vulnerable Exchange Servers on the Internet were likely compromised, making it imperative for organizations with public Exchange Servers to initiate an incident response process under the assumption that theirs was compromised.
Organizations running any affected version of Microsoft Exchange Server should immediately install any available patches to Exchange Server software.
It’s also important to note that the presence of this vulnerability within your third-party vendor ecosystem can pose a threat as well. Bad actors in the Exchange breach can not only access your conversations with an infiltrated third party, but can penetrate your network through your vendor’s access. Continuously monitoring your supply chain can help identify vulnerabilities and facilitate remediation before they can become a danger to your organization.
How Bitsight Can Help
Organizations are seeking to determine if they or their vendors may be utilizing vulnerable versions of Microsoft Exchange Server in order to understand their cybersecurity threat exposure. Bitsight is currently showing data of vulnerable and exploited Exchange servers in the vulnerability catalog. Customers can search for any of the Exchange CVEs in the attack chain, by searching for any of the CVEs:
- CVE-2021-26855
- CVE-2021-26857
- CVE-2021-26858
- CVE-2021-27065
Bitsight will continue to update this research and our product with additional telemetry. Please reach out to Bitsight if you have specific questions about the impact of this incident to your organization or your vendor ecosystem.
Critical Policy Questions Moving Forward
The global response to the latest Exchange vulnerabilities raises critical questions about the efficacy of government and industry efforts:
- In light of the Exchange and SolarWinds incidents, how can the government and industry improve their visibility into critical risks and work collaboratively to reduce vulnerabilities that impact the global marketplace?
- Are current patching rates reasonable? What can be done to improve the rates at which organizations apply critical patches? How can business leaders understand whether their organizations are meeting critical metrics? Are there initiatives that could improve patching rates by organizational size or sector?
- What is the appropriate role of the government in providing insight and information for the private sector into these risks? How can government agencies improve their own performance efforts when it comes to managing and patching these critical vulnerabilities?
- How can continuous performance measurement be useful in driving widespread improvement in security hygiene?
Bitsight believes that continuous, ongoing measurement of security performance can provide global market participants with critical information and data that they can use to improve the security posture of their own organizations, supply chains, business partners, insureds, and investments. The latest incidents have highlighted fundamental weaknesses in our society’s approach to addressing and remediating cyber risk, but we strongly believe that data and measurement can help turn government and commercial organizations alike from reactive participants to proactive managers of risk.


