Stealer malware is thriving—especially Lumma and Risepro. These logs fuel ransomware, MFA bypass, and persistent access. It's $10 to compromise an account. Explore this and other insights the data reveals.
Refund & Credit Card Fraud: How Scammers Commit Fraud


What is refund fraud?
Refund fraud is a widespread and increasingly sophisticated form of cybercrime where threat actors manipulate return policies to obtain illegitimate refunds, replacements, or store credits. While the direct impact is felt by retailers, the ripple effects extend across supply chains, logistics partners, and B2B enterprises, leading to inventory distortion, revenue loss, and reputational damage.
This type of fraud is particularly challenging to detect because it often mimics legitimate consumer behavior, making it ideal for low-risk, high-reward exploitation. In some cases, organized cybercriminal groups scale these attacks using bots, fake identities, and compromised accounts to operate across multiple retail platforms undetected.
How does refund fraud happen?
Refund fraud has a simple set of Tactics, Techniques, and Procedures (TTPs) that allow the attacker to earn a nice payout.
Receipt fraud
Cybercriminals generate or alter receipts using stolen data, phishing kits, or dark web templates. These fake receipts are used to return goods that were never purchased. This is often facilitated through social engineering or insider collusion.
Wardrobing
A form of "friendly fraud" where individuals purchase items (e.g., clothing, electronics) with the intent to use them temporarily and return them. This abuse thrives under lenient return windows and no-questions-asked refund policies.
Switch fraud
In this scheme, a fraudster buys a new product, removes it from its packaging, and replaces it with a used or defective version—returning the swapped item as if it were new. This tactic is common with electronics and small appliances.
Return abuse
Fraudsters exploit generous or poorly enforced return policies by repeatedly returning items, often using multiple identities or retail locations. Automation and synthetic identities have made it easier to scale this tactic across online and physical stores.
Examples of refund and return scams
Kohl’s Cash Refund Exploit
- A scammer exploited Kohl’s loyalty system (“Kohl’s Cash”) across multiple stores, repeatedly returning items purchased with coupons or bonuses to gain store credit or cash.
- Total losses reportedly reached $200,000.
- So what? Loyalty and store credit systems are increasingly targeted, often with automated or serial fraud tactics.
Airline Refund Scam via Forged Documents (India)
- A fake travel agency booked real flights for clients, then canceled them using fraudulent death or medical certificates to claim refunds from airlines.
- The fraudster pocketed most or all of the refund while the customer was left stranded or misled.
- So what? Return fraud is not limited to goods — services like travel or events are highly vulnerable to document-based deception.
Social Engineering + “Over-Refund” Scam (USA)
- A victim was tricked by a fake Norton antivirus email claiming she had been overcharged. When she called the listed number, the scammer “mistakenly” refunded her $49,500 and pressured her to return it in cash.
- She made multiple payments before realizing it was a scam.
- So what? Refund scams can include psychological manipulation and money laundering, not just product returns. These are hard to detect without user awareness or transaction analysis.
Amazon Insider Refund Fraud (USA)
- A fraud ring involving former Amazon employees orchestrated a scheme where customers received both the products and fraudulent refunds.
- The ringleader and accomplices were ordered to repay $2.4 million in damages.
- So what? Insider threats are real and can bypass even well-controlled systems when refund permissions aren’t tightly monitored.
Refund fraud & Retailers
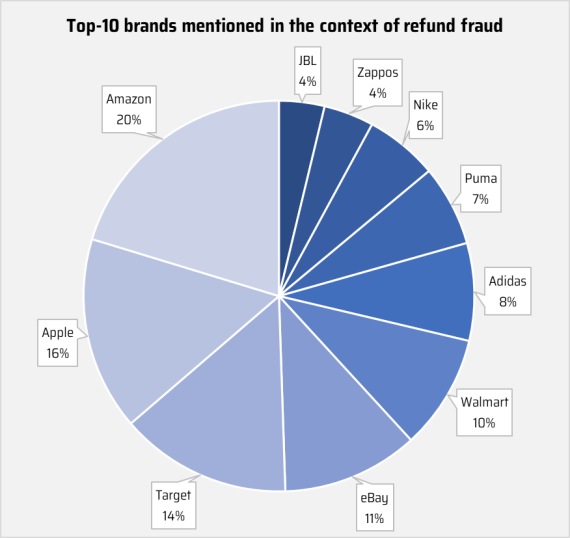
On the cyber underground, threat actors seek to profit fraudulently from the e-commerce boom. In particular, this refunding tactic is growing in popularity. The underground discourse of threat actors peddling their refunding services and threat actors refunding exchanging tips and best practices reveals that certain e-commerce vendors more frequently attract the attention of threat actors. Recently, Amazon attracted the most threat actor attention, followed by Apple, Target, and eBay. This attention inevitably relates to the size and popularity of these retailers, but a study of underground refunding manuals reveals that social engineers are acutely attuned to the unique weaknesses and protocols of different retailers, sharing advice on which retailers to target by which methods - and for how much.
4 Common refunding methods
Generally, most refund scams use social engineering. The underground is rife with guides and manuals on refunding methods and social engineering techniques - some for sale, but many published freely and often anonymously. This section briefly overviews threat actors' most common methods and lays them out in their "how to" guides.
1. “Did Not Arrive”/”DNA”
The simplest refund fraud method involves claiming that the package has not arrived. Underground manuals suggest that customer support will likely press you on whether “you checked with your neighbors/garage/porch,” but that after enough strenuous denial, they will offer you a replacement or refund. An anonymous guide (figure 1) recommends that if the customer service representative says they want to launch an investigation with the courier service, simply hang up and try again.
2. “Empty Box”
This method claims that the shipment arrived empty. The leading vendor that suffers from this refund scam is Apple due to the high value of their items in price. For example, a successful return fraud for a new laptop could net $3,200. Moreover, this method works much better when reporting on small items such as apple’s AirPods, iPhones, etc. In one example, a threat actor shares a guide for refunding Apple in different countries using the ‘empty box’ method.
3. “Wrong Item Arrived”/"Wrong Item In the Box"
Here, the social engineer claims the retailer has sent the incorrect item, then returns a similar, but much cheaper, object that the retailer stocks in their inventory. Social engineering guides emphasize the psychological components of pulling off this method. According to the actor, it doesn't matter who the company is, as they all have a warehouse with an inventory of stock ready to be picked, packaged, and dispatched to their customers. As such, human error is inevitable when picking & packing an order. Thus threat actors can use social engineering for just about any item they like.
4. “Boxing”
This method entails contacting the retailer’s customer support to claim an item is defective, returning the box without the purchased item, and claiming the item got stolen during delivery. Since packages are weighed during shipment, social engineers generally place dry ice of equivalent weight, then tamper with the box to give the impression that the container had been tampered with during transit.
In addition to these guides, threat actors also share their experiences in refunding different retailers, which shed light on what to expect and how to succeed. In one example, an actor sells refunding guides for various retailers such as Best Buy, Amazon, and Sephora, at prices ranging from $600 to $3,000.
How to protect your business
1. Threat intelligence on fraud markets
Bitsight’s Threat Intelligence capabilities include robust deep and dark web monitoring, enabling visibility into online marketplaces and fraud communities where refund scams are openly discussed, bought, and sold. Analysts can uncover emerging TTPs (Tactics, Techniques, and Procedures), such as "box swap" schemes or refund-as-a-service operations, and track threat actor chatter to identify trends or campaigns targeting specific retailers or industries.
2. Actor and botnet attribution
Bitsight delivers on-demand threat actor profiles and supports ongoing tracking of known fraud groups. By correlating refund scam activity with identified actors or automation frameworks (e.g., bots exploiting return APIs), organizations gain vital context to understand who is behind the fraud, what tools they're using, and how widespread the campaign is. This helps prioritize response and enhances fraud detection rules.
3. Brand and retailer monitoring
With Brand Intelligence and Takedown Services, Bitsight monitors for impersonation of your company’s brand or abuse of its return systems across both surface and underground sources. Whether it’s phishing pages mimicking return portals or leaked return label templates, Bitsight helps quickly identify and remove these risks before they result in fraud or customer trust erosion.
4. Supply chain risk management
Refund fraud often targets weaknesses in fulfillment, logistics, or third-party vendor return policies. Bitsight provides supply chain cyber risk visibility, allowing you to identify partners with weak controls or exposure to abuse. This proactive approach helps you secure your extended retail and logistics ecosystem and prevents fraudulent returns from slipping through the cracks via trusted partners.
What is credit card fraud?
Credit card fraud remains one of the most persistent and damaging types of cybercrime, involving the unauthorized use of cardholder data to make fraudulent purchases or cash withdrawals. This fraud manifests in two main scenarios:
Common types of credit card fraud
- Card-Present (CP): Physical card is used, typically at point-of-sale systems or ATMs.
- Card-Not-Present (CNP): The card is not physically present—common in online and mobile transactions.
CNP fraud is the most prevalent, driven by the rapid growth of e-commerce and the ease of transacting with stolen or synthetic card data.
How does credit card fraud happen?
Cybercriminals use multiple techniques to harvest credit card information:
- Data Breaches: Large-scale intrusions into company databases to steal payment details. The healthcare, retail, and hospitality sectors are frequent targets.
- Card Skimming: Skimming devices are attached to legitimate readers (e.g., ATMs, gas stations) to capture magnetic stripe data covertly.
- Phishing Campaigns: Attackers use spoofed emails or fake websites to trick users into entering their card data.
- Algorithmic Generation: Fraudsters use software to generate plausible card numbers using known BINs (Bank Identification Numbers) and validate them using the Luhn algorithm.
How to prevent credit card fraud
Preventing credit card fraud requires a combination of awareness, secure habits, and the right tools. While it’s difficult to eliminate all risk, taking proactive steps can significantly reduce your exposure:
- Stay Vigilant Online: Be skeptical of unsolicited emails or texts that request your credit card details. Always verify the legitimacy of a website before entering sensitive information.
- Use Virtual Credit Cards: Consider using virtual or masked credit card numbers, which are offered by some banks and third-party services. These provide a temporary card number that links to your real account — keeping the real number protected in case of a breach.
- Secure Digital Wallets: Use secure payment platforms like Apple Pay or Google Pay, which tokenize your card information. This means your actual card number isn’t shared during a transaction, making it harder for attackers to intercept.
- Enable Alerts and Monitoring: Set up transaction alerts and regularly review your credit card statements. Quick detection is key to minimizing losses from unauthorized charges.
- Avoid Public Wi-Fi for Transactions: Always use a secure, private network when shopping online or accessing financial accounts. Public networks are often monitored or targeted by attackers. Remember, data in is data out.
Fraud detection
The financial sector continues to be a prime target for cybercriminals and nation-state actors alike, driven by the high value of financial transactions, the sensitivity of customer data, and the sector’s critical role in global economic stability.
According to Bitsight’s 2025 State of the Underground Report, the threat is intensifying:
- 14.5 million compromised credit cards were listed in underground markets in 2024, a 20% increase from 2023.
- This surge was entirely driven by U.S.-issued cards. While non-U.S. card listings declined by 1.6 million, U.S. cards increased by 4.5 million, now making up over 80% of all listings.
This spike reflects both the increased targeting of U.S. financial institutions and potential gaps in domestic fraud detection and prevention. In many cases, fraudulent activity goes undetected for hours or even days, giving cybercriminals ample time to exploit stolen card data. The widespread reliance on credit for everyday purchases in the U.S. only increases the appeal for attackers, making American consumers and institutions prime targets for financially motivated cybercrime.
For individuals:
- Use Secure Payment Methods: Choose platforms like Apple Pay, Google Pay, or virtual cards that tokenize or mask your real card number.
- Verify Website Security: Always check for HTTPS in the URL before entering payment information. Avoid making purchases on suspicious or unsecured websites.
- Enable Account Alerts: Set up real-time transaction alerts to catch unauthorized activity quickly.
For companies:
- Monitor Your Online Presence: Keep track of how your brand is represented online — fraudsters often spoof company names or logos to build fake landing pages.
- Track Dark Web Chatter: Use threat intelligence platforms (like Bitsight CTI) to identify mentions of your company in underground forums, carding shops, or refund fraud discussions.
- Detect Impersonation Sites Early: Regular scanning for cloned domains, phishing pages, and fake apps is essential for protecting your customers and your brand.
- Respond Quickly with Takedowns: Have a takedown process in place to quickly remove fraudulent content that misuses your brand or targets your users.
Conclusion
Refund fraud isn’t just a minor loss—it’s a growing gateway to larger issues like credit card fraud and supply chain vulnerabilities. Scammers exploit weak refund policies, social engineering, and system gaps to commit these crimes, often without detection until it’s too late.
To stay ahead, organizations need visibility into where they’re exposed. That’s where Bitsight can help. Bitsight’s data-driven insights and continuous monitoring capabilities give security and risk teams a clearer picture of their external attack surface and potential vulnerabilities. By identifying high-risk behaviors, detecting compromised assets, and benchmarking security performance, businesses can strengthen defenses and reduce opportunities for refund and credit card fraud to occur.
By integrating Bitsight’s cyber risk intelligence into fraud prevention strategies, organizations can better protect their revenue, maintain customer trust, and stay ahead of emerging fraud tactics.



