Stealer malware is thriving—especially Lumma and Risepro. These logs fuel ransomware, MFA bypass, and persistent access. It's $10 to compromise an account. Explore this and other insights the data reveals.
From Fragments to Full Picture: Turning Threat News into Actionable Campaign Intelligence


Drowning in data
Consider this scenario: a critical zero-day vulnerability is announced for a popular enterprise software and you, as a threat analyst, are tasked with briefing leadership on which threat actors are exploiting it and how. You start to research and are immediately overwhelmed. One news site reports on a Chinese APT using the exploit, another blog details an Iranian group, and a third report lists CVEs without context. You have a dozen articles open and are trying to build a master timeline in a spreadsheet, but the data is conflicting and messy. You spend hours just trying to figure out which malware belongs to which campaign, thinking, "I wish someone could make sense of all of this. I need the full picture to know how to prepare for what comes next."
Cyber attacks happen all the time. But are they coordinated without rhyme or reason? Or are they connected to each other, potentially part of a larger campaign? And, more significantly, is your organization the next target?
Connect the dots to see the bigger picture
Cyber threat analysts struggle to manually stitch together a narrative. And frankly, the struggle is real. Currently, security teams rely on fragmented, tactical approaches to threat data. This includes:
- Siloed alerts: They investigate incidents one by one (phishing emails, malware detections, CVE exploits) without visibility into how they might connect.
- Generic CTI feeds: They subscribe to broad, undifferentiated threat intelligence that lacks context or correlation, forcing analysts to manually stitch together meaning.
- Manual correlation: Analysts attempt to link related activity across log sources, threat feeds, and incident data with spreadsheets or ad hoc investigations.
- Reactive response: Without understanding the bigger picture, teams often respond late or miss the strategic objective behind repeated or coordinated activity.
Practically speaking, analysts must detail the painful, manual process of sifting through this unstructured data. An analyst must open 20+ tabs, read through paragraphs of text, and manually copy-paste actor names, victim details, and CVEs into a spreadsheet or wiki. This process is slow, error-prone, and leads to an incomplete picture.
From unstructured text to structured intelligence
Bitsight Threat Intelligence works like a team of seasoned analysts—minus the overhead. Powered by Bitsight AI, it ingests and analyzes massive volumes of public reporting from the clear, deep, and dark web, transforming raw data into real insight.
This means we’re able to extract, correlate, and de-duplicate entities like malware, leaked credentials, CVEs, TTPs, and threat actors—turning noisy, unstructured inputs into clear, actionable intelligence.
Introducing the Bitsight Threat Intelligence Campaigns card
The Campaigns card, the newest addition to our Adversary Intelligence module, connects individual attacks into a single, strategic view of adversary operations. Each campaign includes a curated timeline of events, attacker objectives, targeted sectors, and links to related actors, APTs, malware families, vulnerabilities, and tools.
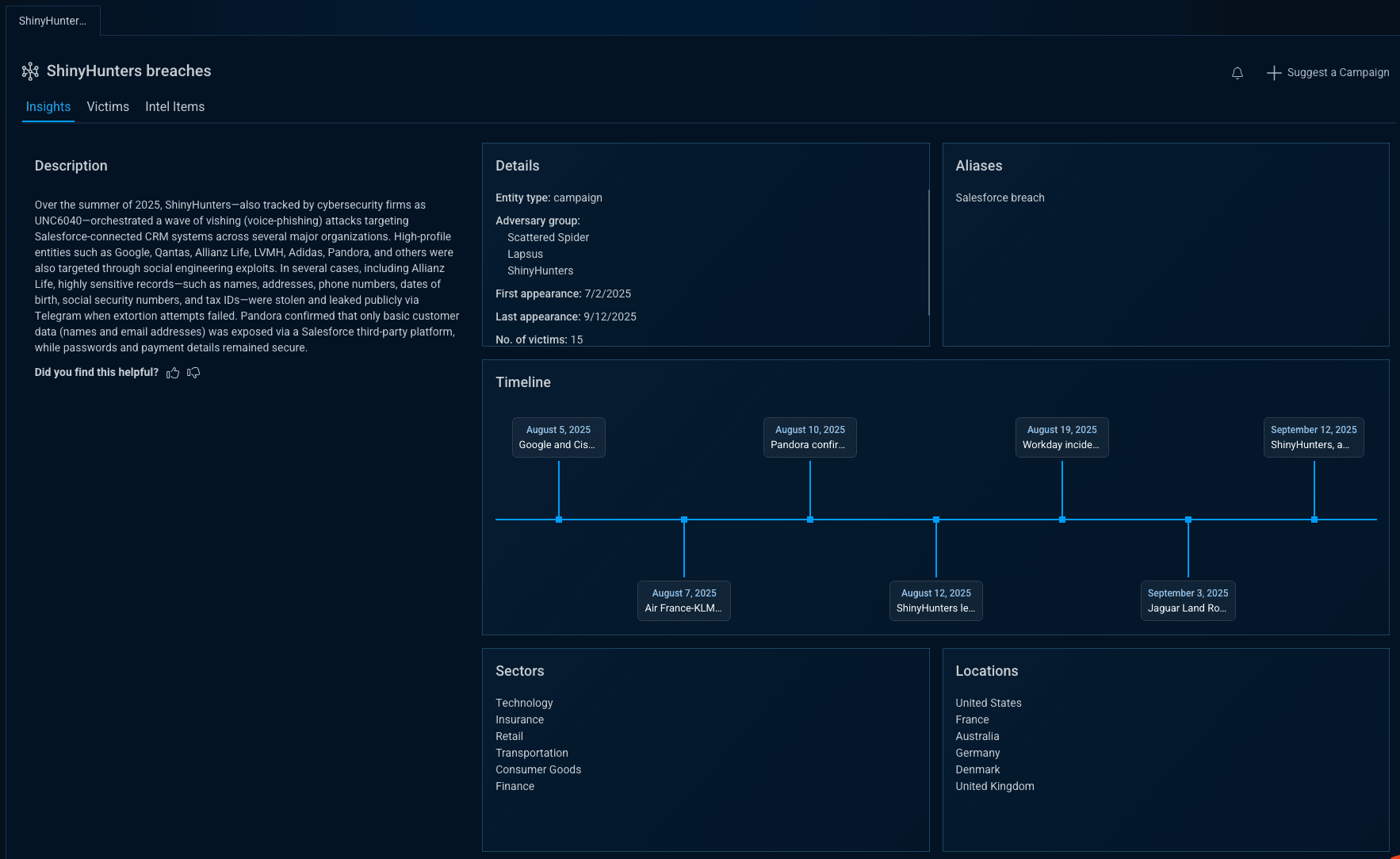
Every campaign is curated by Bitsight AI to enrich the underlying data at scale—mapping assets, summarizing activity, and surfacing relevant intelligence from the dark, deep and clear web. The result is high-value intelligence that is both trustworthy and actionable.
With Campaigns, security teams can move from reactive firefighting to proactive defense. They can prioritize the most critical threats, anticipate attacker moves, and prevent escalation. Analysts reduce investigation time, CISOs gain the narrative needed to brief leadership with confidence, and organizations strengthen resilience against the world’s most impactful campaigns.
Understand how previous attacks unfolded to prevent future threats
The winner in cybersecurity is the one who can move from noise to a decision the fastest. The one who can anticipate the next move and take action.
By transforming chaotic public reporting into a structured campaign view, you gain instant visibility into the full scope of a threat, enabling clear and confident action.
Getting started with Campaigns
Ready to turn news overload into threat clarity? Talk to our team to schedule a demo.



