New! The Security Ratings report is now the Executive Report. Request your report to see enhanced analysis such as your rating, likelihood of ransomware incidents, and likelihood of data breach incidents.
What’s Behind Your Risk Matrix?

This quarter, Bitsight released several new product features that enable organizations to more rapidly assess, prioritize and manage cyber risk. These new capabilities — the Portfolio Risk Matrix and Asset Risk Matrix — leverage Bitsight’s market-leading data to provide risk prioritization, helping customers address the most important risks within their own environment as well as their broader third-party ecosystem.
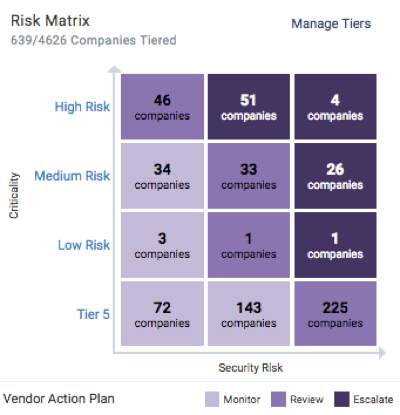
Portfolio Risk Matrix
Bitsight’s Portfolio Risk Matrix allows users to perform critical cyber risk analysis and remediation prioritization of their third-party ecosystem. It leverages a customer’s own customizable tiering configurations to present a clear picture of the state of cyber risk based on business criticality and cybersecurity performance, and it provides a way for customers to prioritize and streamline incident response and collaboration activities on that basis. Within this tool, Bitsight can provide a clear Vendor Action Plan that reflects the state of cyber risk and can be used to drive prioritization of third-party risk resources and efforts.This capability lets companies add additional business context to their vendor population by grouping them into tiers that reflect the amount of cyber risk inherent to the particular business relationship. This additional context allows them to evaluate the cybersecurity performance of their vendors through the lens of the underlying business relationship in order to identify and prioritize those that pose the highest risk to their business. By conducting this analysis, they are able to align their vendor risk program with their organization's business goals and objectives. It also allows them to more rapidly identify and prioritize additional due diligence on the third parties posing the biggest risk to their organization.
Asset Risk Matrix
The Asset Risk Matrix is an innovative feature that prioritizes Bitsight’s security findings based on the importance of assets belonging to a particular organization and the severity of security findings. The automatic calculation of asset importance allows an organization to quickly identify which assets it should focus on (for themselves and/or their vendors) to help drive effective prioritization of remediation efforts like fixing an issue or opening a contextual Enable Vendor Access (EVA) request for a vendor. The Portfolio Risk Matrix allows companies to identify the vendors that pose the most risk to them based on their designated tiering — this allows them to see a comprehensive view of their vendor population with additional business context. Instead of having to go into a specific folder (e.g. Tier 1 vendors), now organizations can see a more holistic view of the cyber risk across their entire vendor portfolio and easily drill down. Once they identify the vendors who pose the most risk, the Asset Risk Matrix allows them to focus on the highest risk issues facing these vendors (or their own company) to drive effective communication and remediation of security issues.

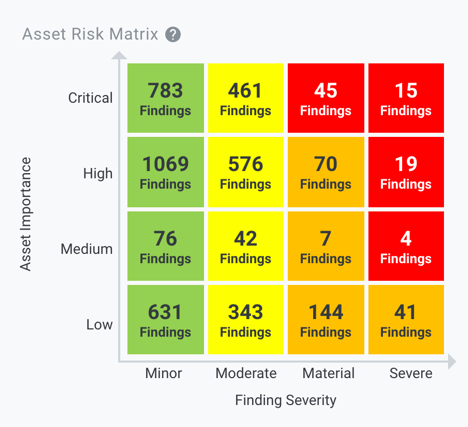
Compared to other security ratings solutions, Bitsight provides a significantly more extensive view of internet- facing assets that also takes into account important business context, like how often the organization is using the asset, to provide a more comprehensive tool to ensure companies are actually prioritizing action and remediation on the riskiest assets in their network or extended ecosystem. Backed by the most extensive visibility into security issues and assets, Bitsight is the only security ratings solution that can help you identify the most critical issues facing your critical suppliers.
Bitsight’s Portfolio Risk Matrix and Asset Risk Matrix help security and risk leaders make intelligent, data-driven decisions at the speed of business by enabling them to identify and prioritize critical areas of risk within the context of their organization. Finally, security and risk leaders can be confident they are focusing on the critical areas of cyber risk that matter most to the business.


