Explore expert perspectives, data-driven strategies, and the latest trends in cybersecurity, third-party risk management, and cyber threat intel — all from the leader in cyber risk intelligence.
Blog

Featured blog
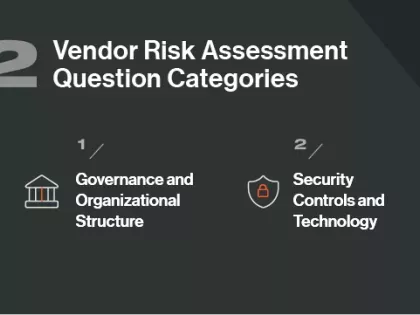
How is one questionnaire different from another, and how do you decide which ones to use in vendor risk assessments? We compare CAIQ vs. SIG.