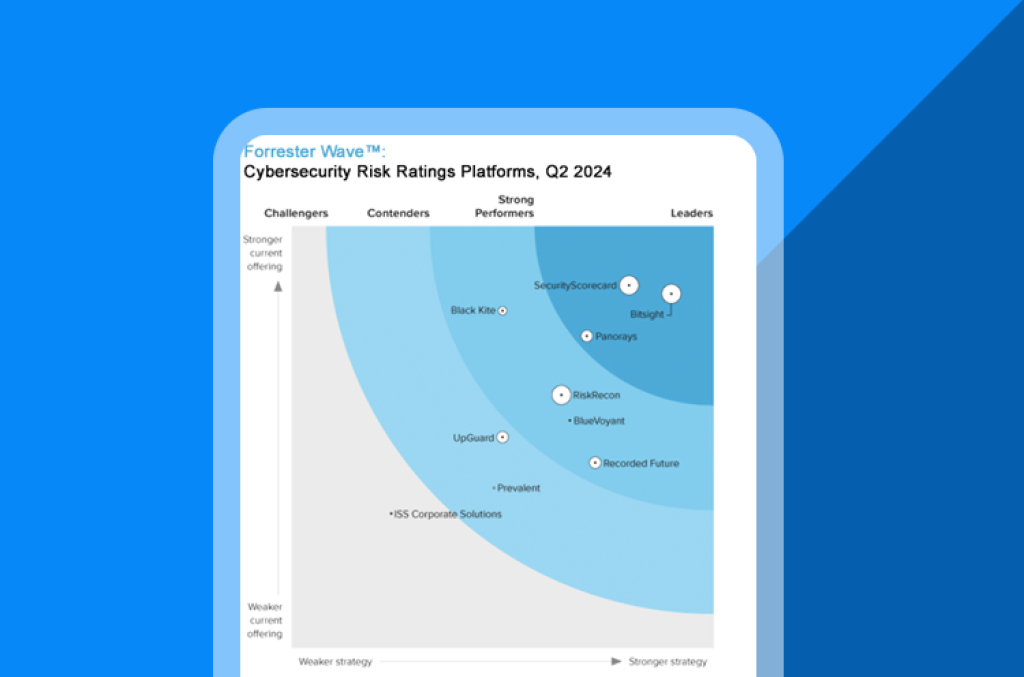
Cyber risk ratings platforms are proliferating—and not all are built equal. Forrester’s 25‑criterion evaluation reveals who’s delivering accuracy, scale, and vendor credibility. Use it to shortlist tools aligned to your risk appetite and control framework.
How to Mitigate Third-Party Risk
Understanding third-party cyber risk
Third-party cyber risk is the potential threat posed by external entities—such as vendors, suppliers, and partners—that have access to an organization's systems or data. These risks can manifest through various vulnerabilities, including inadequate security controls, lack of compliance with industry standards, or insufficient incident response capabilities. It can lead to financial, reputational, and regulatory/compliance consequences.
Third-party risk management (TPRM)
Third Party Risk Management (TPRM) is the practice of continually identifying, analyzing, mitigating, and controlling risks associated with third parties. Effective TPRM programs allow organizations to accurately gauge vendor risk in a variety of areas, understand the risk of current and potential vendors, and take steps to mitigate risk by implementing protections, addressing concerns with vendors, and avoiding or ending vendor relationships that are considered too risky.
Strategies to mitigate third-party cyber risk
As enterprises are more reliant than ever on outsourcing and cloud services, knowing how to mitigate third-party risk has become a critical priority. Risk incidents connected to third parties are at an all-time high, with 59% of organizations reporting that a data breach was caused by one of their vendors.
As a result, security leaders and risk managers are seeking better solutions for third-party risk management. Companies need strategies for accessing the value that vendors and third-party services provide, but without introducing unwanted cyber risk and unnecessary overhead. Traditional approaches to measuring third-party risk provide some help, but they don’t deliver the security visibility organizations need to prioritize resources and achieve measurable risk reduction.
1. Implement continuous monitoring
Traditional point-in-time assessments are insufficient in the dynamic cyber threat landscape. Continuous monitoring provides real-time visibility into the security posture of third-party vendors, enabling organizations to detect and respond to risks promptly. Tools like Bitsight offer daily-updated Security Ratings, offering objective insights into a vendor's cybersecurity performance.
2. Conduct thorough vendor assessments
Before onboarding a new vendor, perform comprehensive due diligence to evaluate their security practices. Assessments should include reviewing security policies, incident response plans, and compliance with relevant regulations. Automated solutions can streamline this process, reducing the time and resources required for manual evaluations.
3. Facilitate transparent communication
Establish open lines of communication with vendors regarding cybersecurity expectations and requirements. Sharing security ratings and assessment results fosters collaborative efforts to address vulnerabilities and enhance overall security posture. Bitsight's platform, for instance, allows organizations to share ratings with vendors, promoting transparency and accountability.
4. Define clear security requirements in contracts
Incorporate specific cybersecurity clauses into vendor contracts, outlining expectations for data protection, incident reporting, and compliance obligations. Clearly defined contractual requirements ensure that vendors are legally bound to maintain adequate security measures, reducing the likelihood of breaches originating from third-party relationships.
5. Prioritize vendors based on risk
Not all vendors pose the same level of risk. Implement a tiered approach to vendor management by categorizing vendors based on the sensitivity of the data they handle and their access to critical systems. This prioritization enables organizations to allocate resources effectively, focusing on high-risk vendors that require more rigorous oversight.
6. Leverage risk ratings for informed decision-making
Security ratings provide a quantifiable measure of a vendor's cybersecurity performance. By leveraging these ratings, organizations can make informed decisions about engaging with vendors, identifying potential risks early in the relationship. Bitsight's Security Ratings, for example, offer objective data to assess and compare vendors' security postures.
The importance of a proactive approach
Adopting a proactive stance toward third-party cyber risk management is crucial. By continuously monitoring vendors, conducting thorough assessments, and fostering transparent communication, organizations can identify and address vulnerabilities before they are exploited. This proactive approach not only mitigates risks but also strengthens the overall cybersecurity resilience of the organization.
Bitsight for Third-Party Risk Management provides tools for continuously monitoring the security posture of vendors to give risk managers a complete and trusted view into their risk portfolio. With Bitsight, risk managers can learn how to mitigate third-party risk through automated processes, daily-updated Security Ratings, and a clear picture of third-party risk aligned to the organization’s risk tolerance levels.
How to minimize the risk of a third-party data breach
A key challenge to managing third-party cyber risk is that everything is out of your direct control. How can you gain insight into your vendor's security posture so that you can make informed decisions about the risks of doing business with them? Even with that insight, how do you get at-risk vendors to improve their security controls?
Below are 4 steps you can take to reduce of the risk of a third-party data breach:
Assess your vendors for risk before you enter a relationship
Onboarding third-party vendors who will have access to your network and data without gauging the cybersecurity risk they pose is extremely risky. Yet, too many organizations overlook the importance of cyber risk assessment during the vendor selection process.
One way to calculate risk is by using a continuous monitoring and vendor risk assessment tool, like Bitsight Security Ratings. With Bitsight, you can quickly assess the information security, vulnerability and threats that a vendor may pose and the risk for a potential breach. This pre-assessment can be done without requiring consent from a vendor. You can even benchmark and compare a vendor to their peers and others in their sector to help you make an informed decision about which vendor you should select.
The result is a more accurate real-time picture of cyber risk than can be achieved by completing costly vendor risk assessments, penetration tests, or vulnerability scans.
Incorporate risk management into your contracts
Make a practice of including cybersecurity risk into your vendor contracts. While this won’t prevent a third-party data breach, it will hold the vendor accountable should their cyber risk posture change and they fail to act to remediate it.
We also recommend that you incorporate SLAs into your contract so that you can steer the cybersecurity risk management behavior of your vendor. Consider adding language that requires your vendors to communicate or even remediate any security issues within a certain time frame, such as 48 or 72 hours.
Once onboard, continuously monitor your vendors for security risks
An organization’s security posture can and will change over the course of your contract. It’s critical that you continuously monitor their security controls over time.
The trouble is, most organizations don’t continuously monitor into their third-party risk management programs. Instead, they perform point-in-time assessments, such as a cyber security audit or cyber security risk assessment questionnaires, which are typically only snapshots of an organization's security posture. These snapshots can fail to capture risk that can arise over the course of the third-party relationship.
Indeed, Gartner found that 83% of legal and compliance leaders identified third-party risks after due diligence and before recertification. “As third-party relationships change, compliance leaders must ensure risks are mitigated over the course of the relationship.
Collaborate with your vendors to protect against a third-party data breach
While you can never fully prevent a third-party data breach, it’s important that you work collaboratively, not combatively, with your vendors to reduce risk and fix security issues quickly so that you don't end up in a situation similar to the SolarWinds breach.
There are several features in Bitsight that support this process. For example, you can give vendors access to your portal so they can investigate their rating and the details behind it, enabling them to identify vulnerabilities and immediately remediate risk. Bitsight also sends alerts when a vendor’s rating drops below a certain threshold and suggests remediation strategies. This facilitates outreach and allows you and your vendors to react quickly and responsively.
The role of continuous monitoring
Continuous monitoring has long been an effective tool for addressing cybersecurity risk. Many organizations have security operations centers that monitor the network 24/7 for attacks and vulnerabilities, enabling security teams to quickly identify threats and take action to remediate them.
However, effectively deploying continuous monitoring for third-party cyber risk assessment has been more of a challenge, as organizations lack clear insight into the internal operations, defenses, and security controls of their vendors as networks are rapidly expanding year over year. Instead, risk managers have relied on vendor self-assessments completed at regular intervals – often yearly – to evaluate the security posture of their organizations, leaving them blind to vulnerabilities that occur between assessment periods.
While this approach offers some value, it is limited by its subjectivity and frequency. Self-assessment questionnaires are inherently subjective, and risk managers can’t know how accurate a vendor’s assessment is without spending a great deal of time manually verifying their responses. Additionally, because assessments are completed so infrequently, they offer no help in continuously monitoring for third-party risk.
To implement a continuous monitoring program, third-party risk managers need objective, verifiable information about a vendor’s security posture on an ongoing basis. Fortunately, Bitsight Security Ratings can provide this information easily and accurately.
Mitigating third-party risk with Bitsight
Bitsight Third-Party Risk Management provides organizations with the capabilities they need to reduce third-party risk and mitigate third-party cyber security issues:
- Take a proactive approach. With near real-time insight into the security posture of vendors, risk managers can measure changes in security ratings against established risk thresholds and conduct reassessments to prevent potentially unacceptable risk from being introduced into the third-party ecosystem.
- Customize assessments. Risk managers can tailor assessments to each vendor, spending more time and resources on the vendors or areas of a vendor’s operation that represent greater risk, and can choose to skip or spend minimal time on vendors with higher Bitsight ratings.
- Establish a tiered assessment structure. By tiering vendors according to level of sensitive data they will have access to, risk management teams can spend more time assessing vendors that pose a greater risk to their organization and less time on vendors who won’t cause much damage to the organization based on their business use-case.
- Provide objective context to self-assessments. Armed with data from continuous monitoring, risk managers can add objective context to the assessments completed by vendors to determine how accurate their answers are and whether their self-assessment truthfully reflects their security posture.
- Security ratings that correlate to risk of data breach. Research has shown that an organization’s Bitsight rating along with grades in certain risk categories can reliably predict future security performance and how susceptible they are to bad actors.
- Faster onboarding. Bitsight helps third-party risk management teams reduce the time and cost of onboarding vendors by quickly identifying known issues and quantifying risk with smart tiering recommendations.
- Enable the business. Bitsight makes it easy to bring on vendors in a timely way while summarizing and communicating the risk that’s associated with the vendor relationship.
- Reduce third-party and cyber security risk. Bitsight delivers a clear picture of risk aligned to each organization’s risk tolerance. Risk managers can prioritize resources to drive risk reduction across the portfolio of vendors, based on the risk-based tier a vendor falls into.
- Communicate risk to the Board and C-suite. Bitsight’s reporting capabilities make security performance understandable and accessible for individuals with non-technical backgrounds. Security and risk managers can quickly create custom reports on the fly or use built-in cyber security risk assessment report samples and templates.