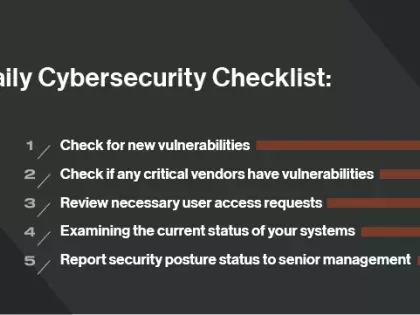
Explore expert perspectives, data-driven strategies, and the latest trends in cybersecurity, third-party risk management, and cyber threat intel — all from the leader in cyber risk intelligence.
Blog
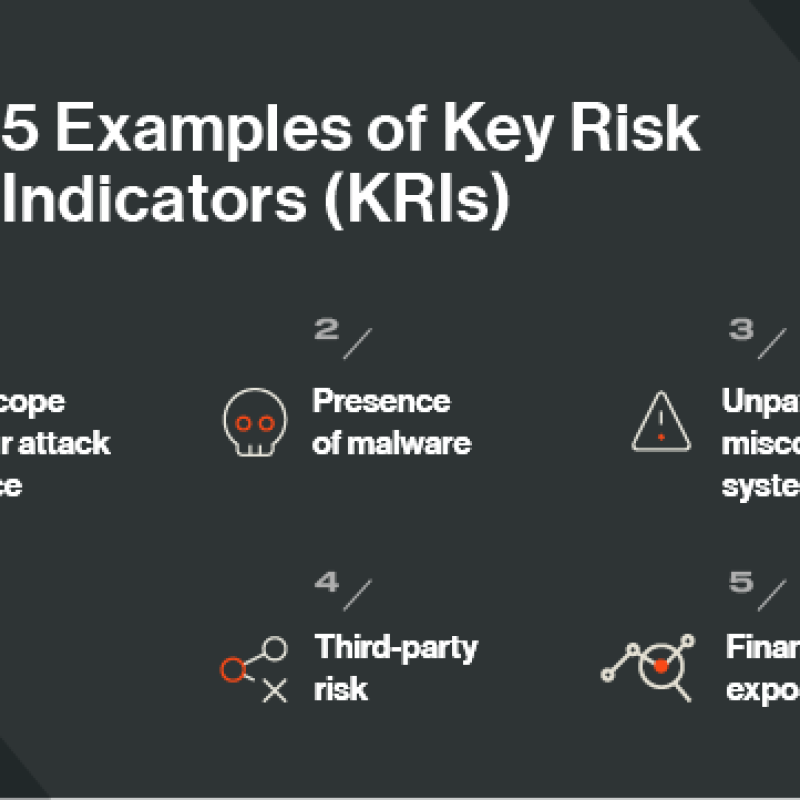
Featured blog
Key risk indicators (KRIs) can help monitor and control cyber risk. But what KRIs should you focus on?