New! The Security Ratings report is now the Executive Report. Request your report to see enhanced analysis such as your rating, likelihood of ransomware incidents, and likelihood of data breach incidents.
U.S. Election Security, Part 1: Voting Systems Vendors’ Cybersecurity is Improving
Tags:


Significant concerns have been raised about the security of the 2020 United States election. Hundreds of millions of dollars in Federal funding has been made available to state and local governments to improve the security of election systems and remediate vulnerabilities within critical organizations. Congressional hearings have highlighted risks to electronic voting systems and the vendors who manufacture them. Government task forces have been created to address the challenge.
Are these efforts having an impact?
After Congressional testimony was received in January 2020 from Voting System Vendors and experts, Bitsight began tracking the security performance of a number of Voting Systems Vendors who together represent a large percentage of the U.S. election infrastructure market. Voting System Vendors are companies that produce electronic voting machines, equipment, software, and services for use in U.S. elections. Bitsight continuously collects over 200 billion security events on a daily basis from around the global internet leverage in an automated, non-intrusive fashion, and leverages this data to track security performance of organizations around the world.
Since January 2020, Bitsight has observed steady improvement in security hygiene among critical Voting Systems Vendors, suggesting that these organizations have made changes to their security programs that have resulted in improvements.
Back in January 2020, the median Bitsight security rating of Voting System Vendors was 695. (The Bitsight rating scale is from 250-900, with lower scores correlated to breach probability). Bitsight observed a number of critical security issues. For example:
- A Voting System Vendor was observed with multiple instances of network administration and monitoring interfaces exposed to the Internet. As a best practice, such interfaces should be protected behind a firewall to prevent them from being discovered as a potential attack surface. If compromised, network infrastructure devices can enable attackers to rapidly expand access to an organization by enabling them to monitor internal network traffic for sensitive information and attack other internal network services.
- A Voting System Vendor was observed running software vulnerable to a critical severity vulnerability (CVE-2019-11581). This extremely high severity vulnerability means that an attacker can likely gain remote access to the host operating this software with minimal effort.
- A Voting System Vendor was observed running remote access software that is no longer supported by the platform on which it operates. Such software may not receive updates to critical security issues, leaving it potentially vulnerable to exploitation. This represents evidence that the Vendor does not operate an effective software patching program.
- A Voting System Vendor was observed operating an open DNS resolver, meaning one that will respond to requests for which it is not configured to resolve authoritatively. In addition to making this DNS resolver vulnerable to an array of attacks and compromises, it is a misconfiguration that may reflect a poor understanding of networking principles on behalf of the staff responsible for managing and securing the Vendor’s network infrastructure.
Since we first made these observations in January, Bitsight has observed improvements in the Voting System Vendors’ security posture. From January 1, 2020 until August 28, 2020, Bitsight has observed that Voting System Vendors median Bitsight security ratings have improved from an average rating of 695 to an average rating of 745, a 50 point improvement over the timeframe. Because Bitsight ratings are the only security rating independently correlated with breach, this measurable improvement means that the group significantly reduced their breach probability during the critical run-up period to the election.

Among the security improvements that Bitsight has observed:
- At some point last year a large number of VPN services had expired certificates, but all are resolved by now. This could have potentially allowed an attacker to collect credentials and gain unauthorized access to systems.
- Multiple systems that used an expired wildcard certificate since August 2018 were found to have remediated the issue in April 2018; these systems are no longer using expired certificates.
- Some Telnet (Port 23) ports for networking devices that were once accessible and unencrypted have been resolved.
- A JIRA server vulnerable to remote code execution has been resolved.
Generally speaking, the numbers of observations and findings that Bitsight makes about exposed or vulnerable systems for these organizations has reduced over the last year. For example, Bitsight observes ports that are exposed to the Internet, known as “open ports.” While certain ports must be open to support normal business functions and few companies will actually have no ports open, the fewer ports that are exposed to the Internet, the fewer openings there are for attack. Bitsight identifies particularly risky exposures by categorizing them as “WARN” or “BAD.” There were no more WARN or BAD observations registered after April 2020.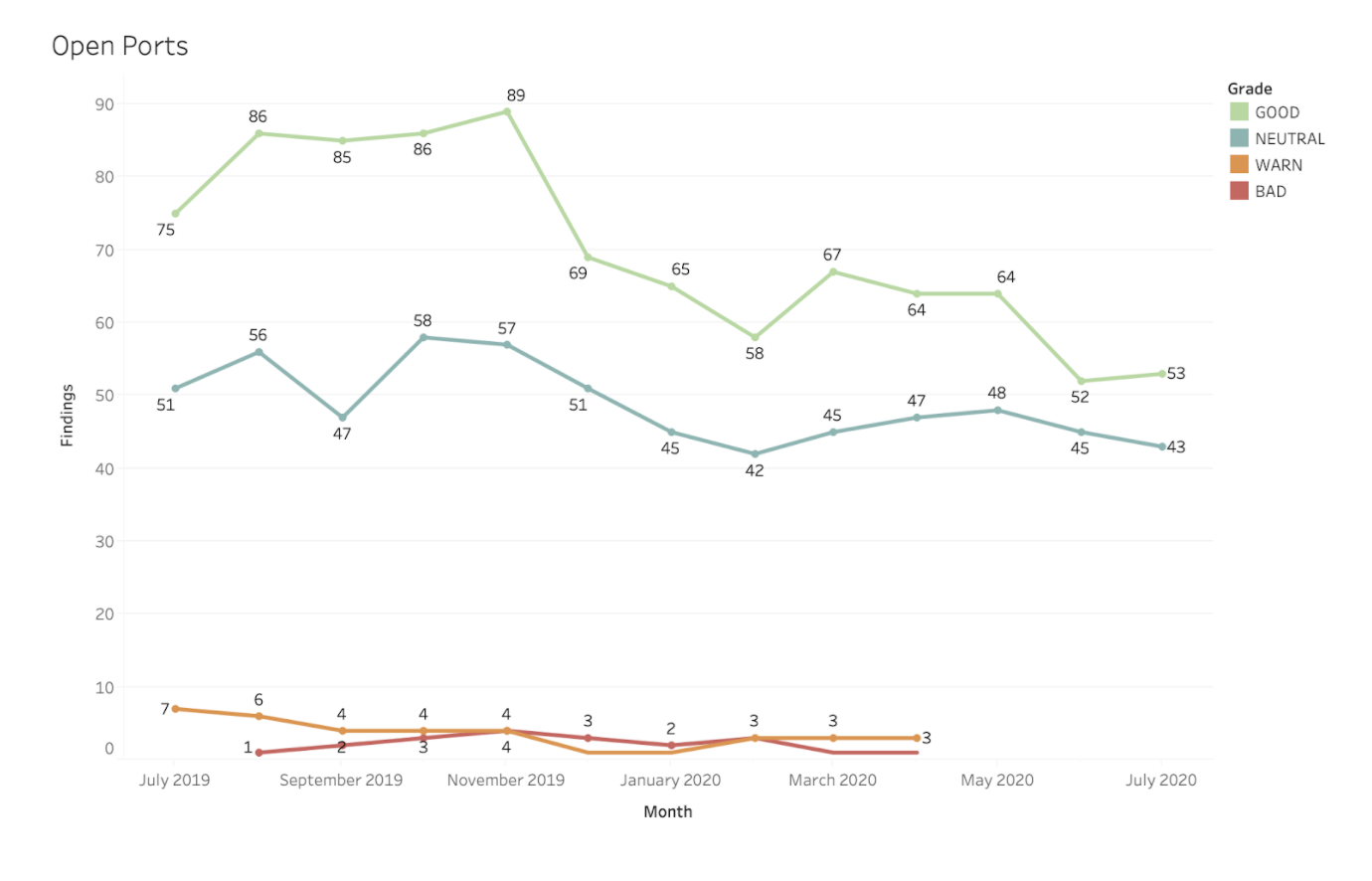
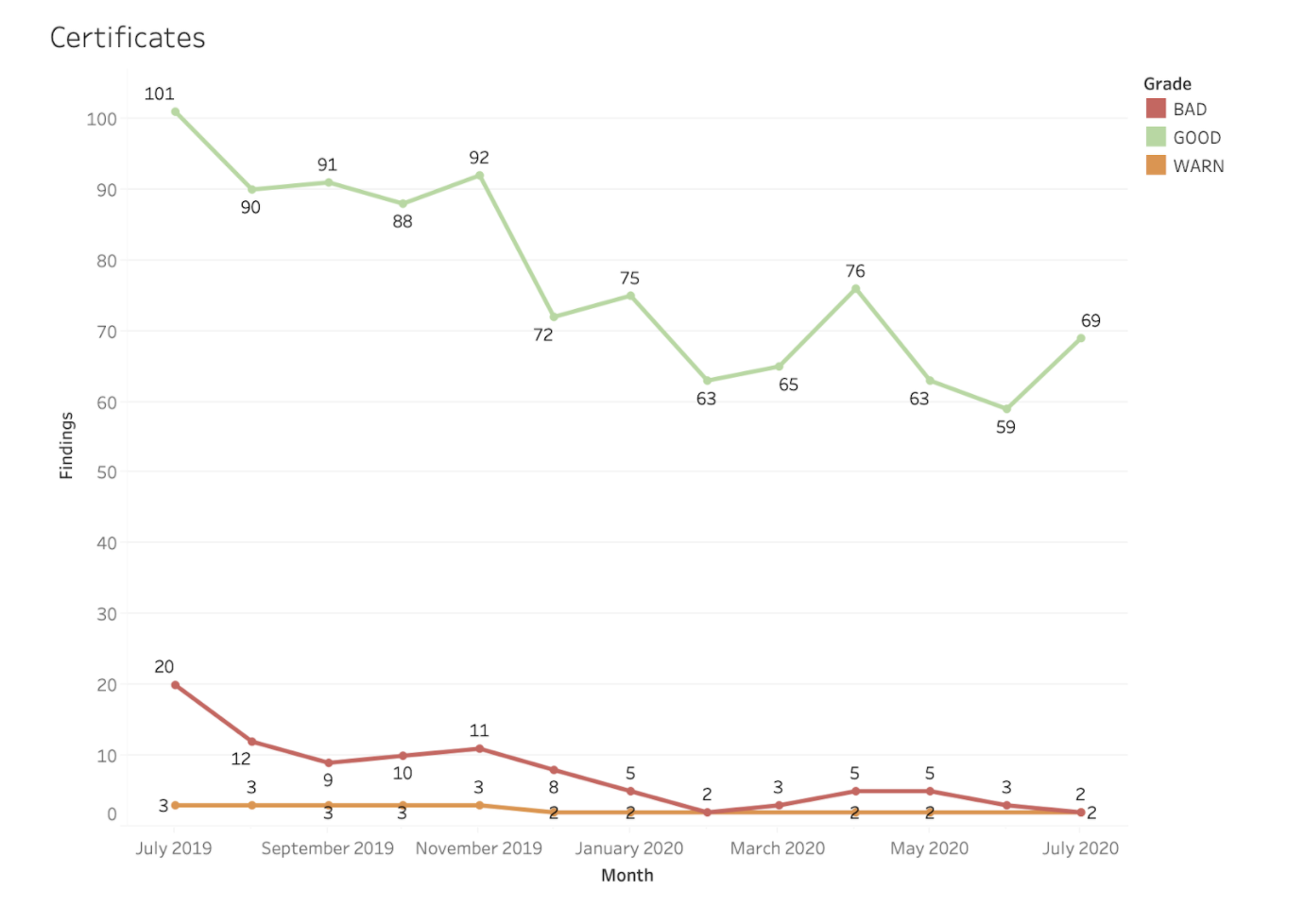
For another example, Bitsight evaluates the strength and effectiveness of the cryptographic keys within TLS and SSL certificates, which are used to encrypt internet traffic. Certificates are responsible for verifying the authenticity of company servers to associates, clients, and guests, and also serves as the basis for establishing cryptographic trust. In reviewing certificates of Vendors, Bitsight also discovered that “BAD” certificates were nearly eliminated.
Summary and Recommendations
- In today’s threat environment, organizations can reduce risk by addressing vulnerable systems. While threat actors continue to explore methods of attack, organizations can reduce the likelihood of breach by identifying and remediating vulnerabilities within their infrastructure. Bitsight cautions that these and other organizations associated with the 2020 U.S. election still face risk from highly capable threat actors and may still be at risk of incident despite addressing these important issues. However, improving security and reducing attack surface are clear and measurable steps to improve performance and reduce likelihood of breach.
- Governments can use data to measure efficacy of cybersecurity policies and programs. Bitsight cannot say for certain what caused the change in the security performance of these Vendors. Was it the result of increased funding? More internal resources devoted to identifying and remediating these issues? External pressure? All of the above? While the causes for change may be unknown, the result is a clear improvement in the security hygiene within a critical sector. Bitsight suggests that U.S. and international policymakers continue leveraging objective data and metrics to track the impact of their significant cybersecurity investments and evaluate success.
- Additional organizations and systems may be at risk. Voting System Vendors are only one type of organization critical to the outcome of the U.S. election. State and local government agencies, critical technology suppliers, and the US Postal Service are only some examples of organizations that will play a role in the 2020 US election. Bitsight intends to examine security performance among other organizations in the weeks ahead.


