With this ebook, we'll help you prioritize which vendors need the most attention with an in-depth security assessment – such as those with low security ratings, or critical vendors that maintain constant contact with your company’s systems.
A Complete Guide to Third Party Risk Management (TPRM)

Vendor risk management (VRM) and third party risk management (TPRM) are trending terms following a series of major cyberattacks and data breaches affecting organizations through their third-party vendors (Kaseya and SolarWinds are the latest examples). But what is TPRM?
The global, interconnected network of enterprises and vendors working together, and the uptick in digitization and remote work stress a growing risk of being hit by a third-party data breach. Assuming your organization interacts with dozens or hundreds of third-party vendors, read on to find out everything you need to know about third-party risk management and how to secure your vendor ecosystem.
What is TPRM?
Third-party risk management (TPRM) is the continuous process of identifying, assessing, and managing risks presented by third parties to an organization, its data, operations and finances. It’s not just a compliance task—it’s a strategic function that helps answer key questions: Can we trust this vendor? Are they secure? What happens if something goes wrong?
TPRM allows organizations to control the risk that arises from outsourcing services and products, by shedding light into areas of potential business risk.
What is a third party?
The term ‘third party’ encompasses vendors, contractors, suppliers, and any person or entity that provides goods and services to other entities, such as:
- A law firm
- An outsourced software development company
- A company that sells office equipment
- A finance consultant who advises about mergers and acquisitions
- A research center
What are third party risks?
Third-party risks are the vulnerabilities your vendors can introduce to your organization—whether intentional or not. These risks include:
- Critical Exploits: Unpatched systems or weak controls can open the door to attackers.
- Data Breaches: If a vendor is breached, your data and your clients data could be exposed too.
- Regulatory Risk: Non-compliance by vendors puts your organization at legal and audit risk.
- Operational Disruption: Outages or supply chain issues at a vendor can impact your business.
- Reputational Damage: Vendor incidents can erode customer trust and investor confidence.
- Legal Exposure: Breaches involving PII or regulated data can lead to lawsuits or fines.
Managing these risks proactively is essential in a connected, cloud-based ecosystem.
What challenges do you face when managing third party risks?
Vendor sprawl & cyber volatility
As third- and fourth-party ecosystems grow, so does the risk surface. With constant cyber threats like ransomware and zero-days, TPRM teams are under pressure to detect and respond across a rapidly expanding vendor footprint.
Budget pressure & efficiency focus
As businesses prioritize profitability, TPRM teams are expected to deliver more with less. Tools that offer automation, speed, and clear insights—not just more data—are rising to the top.
Interdependence without leverage
Vendor relationships are critical but not always balanced. TPRM teams often depend on limited, vendor-provided intel. That makes independent visibility from tools like Bitsight essential.
Scaling constraints
Most TPRM teams are small, managing hundreds of vendors with limited resources and varied cyber expertise. Usable, intuitive tools often outperform complex ones in driving real outcomes.
Fatigue with traditional methods
Teams are increasingly frustrated with slow, burdensome questionnaires and static risk ratings. They’re seeking smarter, integrated solutions with clearer risk signals and less manual overhead.
AI & LLMs as disruptors
AI—especially large language models—is reshaping TPRM. These tools can automate analysis of vendor documents, helping teams extract value quickly without relying on vendors to produce new materials. The result: faster reviews, better prioritization, and scalable workflows.
TPRM common questions & myths
1. Is TPRM only necessary for companies with thousands of third-party relationships?
No: it just takes one of your third parties to cause a breach. Nearly every organization is reliant on a third-party for some type of service. If immediate third parties do not pose cyber risk directly, their third parties (your fourth parties) may. Organizations need to ensure they are tracking the entire flow of their data and monitoring organizations across these flows. Security ratings allow you to deliver timely, data-driven insights into any vendor’s security performance by continuously analyzing, and monitoring companies’ cybersecurity, all from the outside. Security ratings are generated on a daily basis, giving organizations continuous visibility into the security posture of key business partners.
2. Is compliance the primary goal of any third-party risk management program?
No: compliance should be one goal of your third-party risk management program, but not necessarily the primary goal. Many industries and governments regulate third-party risk management, but maintaining compliance doesn’t ensure the safety of your company’s data. It's critical to align third-party risk management strategy or programs with increasing global and regional cybersecurity regulations (i.e. GDPR, NYDFS) and business initiatives. Ongoing and continuous monitoring is a key step towards aligning third-party risk management strategy to cybersecurity regulations.
Security ratings can serve as a critical piece of your TPRM program by helping security and risk teams go above and beyond to quickly identify critical third parties, efficiently scale their TPRM programs, and provide a means to collaborate with those third parties and remediate security issues efficiently.
3. Should TPRM be a Board-level initiative?
Yes: TPRM is no longer just a responsibility for IT departments. A successful third-party risk management program has sponsorship from multiple departments, as well as support and involvement from the Board. In fact, Gartner estimates that by 2020, 75% of Fortune Global 500 companies will treat vendor risk management as a Board-level initiative.
4. Should all cybersecurity resources be allocated towards defending one’s own network?
No: your own network could be extremely secure, but without effective third-party vendor risk management, your sensitive data will still be vulnerable. Surveys indicate that many data breaches are caused by third parties — they continue to make headlines as business after business suffers compromised security at the hands of a supplier. Deloitte reports that 1 in 5 organizations has experienced a third-party breach, and 1 in 10 has lost revenue as a result. Lastly, studies show that the most expensive data breaches are the ones that originate from third parties.
5. Is it true that a typical vendor questionnaire could be 50% shorter & just as effective?
Yes: third-party vendor security questionnaires are a traditional security assessment method, which are often time-consuming and resource-intensive. As a result, many organizations are moving towards shared, streamlined questionnaires. By supplementing these questionnaires with continuous monitoring data like Bitsight Security Ratings, customers have been able to drastically reduce the number of questions they need to ask their third parties and decrease turnaround times — making their TPRM program more efficient and effective overall.
6. Can organizations really influence their third parties’ cybersecurity practices?
Yes: security leaders have proven that writing security obligations into contracts is one way to influence, but having frequent data-driven conversations using security ratings and assessment results can also improve vendor performance. In fact, one Bitsight customer was able to improve the security posture of more than half of their vendors in just 6 months by granting them access to the Bitsight platform. Bitsight Security Ratings enables collaboration through consistent, data-driven security and risk conversations; it allows users to instantly share ratings with critical third parties directly in the vendor portal, fostering more effective collaboration around security to better protect company assets.
Businesses will keep investing in stronger third-party risk management programs as the need to outsource critical business functions continues. It’s important for these organizations to understand how security ratings can help proactively mitigate the risk posed by their third-party supply chain as well as facilitate collaborative relationships with their third-party vendors.
7. Is it possible to always have an up-to-date view of a third party’s cybersecurity posture?
Yes: Bitsight Security Ratings are updated daily, allowing third-party risk teams to continuously monitor every third parties’ cybersecurity posture from the outside in. This can make a big difference compared to traditional point-in-time risk assessment techniques. For example, during the outbreak of the WannaCry ransomware attack, one Bitsight customer was able to identify every affected third-party in just one day. With the ability to drill down into the security details used to generate an organization’s rating, companies can lead intelligent, data-driven conversations with third-party vendors about their current security posture.
8. Do security ratings reflect real-world security risks?
Yes: Bitsight continuously updates its rating algorithm to reflect real-world security risk. It has been independently verified that a company that has a Bitsight Security Rating of 500 or lower is nearly 5x more likely to experience a data breach than a company with a rating of 700 or higher. Bitsight also leverages real-time data on compromised systems from our proprietary sinkholing infrastructure — regarded as the largest in the world. Our high-quality data helps organizations proactively mitigate risk both internally and in their supply chain in real time.
9. Are all security ratings the same?
No: Different security ratings measure different risk vectors, have different levels of consistency, haven’t been independently reviewed, and are delivered through different platforms. Bitsight takes 23 risk vectors into account when computing security ratings, while alternative security ratings services factor in 10 or fewer. In addition, Bitsight has more than 1,200 customers actively monitoring over 100,000 organizations. This level of engagement and the valuable ecosystem created by and for our customers enables Bitsight to provide more accurate and refined security ratings.
With new threats emerging daily and companies increasingly outsourcing, managing vendor risk is becoming increasingly critical to protecting a company’s most important assets. The third party risk gap is growing, and it’s more critical than ever to enable your organization to proactively mitigate risk while continuously monitoring the security performance of vendors.
How to build a third-party risk management framework
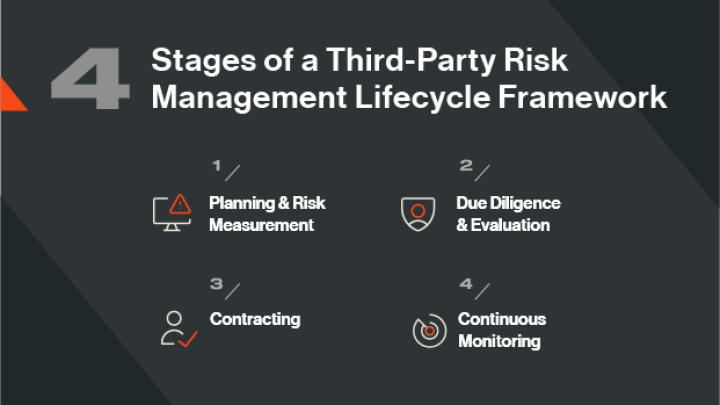
Broadly speaking, there are 4 stages on a third-party risk management lifecycle framework:
1. Planning & risk measurement
Where based on an identified business need, you determine the inherent risk of engaging with a vendor to accomplish a certain goal.
2. Due diligence & evaluation
Where you conduct the vendor risk assessment, which can be based on standards like the National Institute of Standards and Technology (NIST) Special Publication 800-53 or a customized version to include organization-specific security controls and requirements.
3. Contracting
Where based on the assessment results, you negotiate contractual risk controls and measurements.
4. Continuous monitoring
Where you constantly reassess the vendor to ensure compliance with the agreed security standards, by using security ratings and alert mechanisms.
Why is third-party risk management important?
Every organization, no matter the size or industry, engages with third-party vendors. But in working with them, organizations usually grant them access to their network and data, increasing exposure to risk and expanding the attack surface.
As a consequence, securing data and implementing defensive measures does not end at your organization’s digital perimeter. Simply put: you could end up in the headlines because your vendor failed to protect your data and that of your customers.
It is necessary to assess, monitor, and reduce the risks that arise from third-party business relationships, as well as ensure that the vendor will comply with your security standards. This is all part of a third-party risk management (TPRM) program.
How is TPRM changing?
In today’s evolving risk landscape, organizations are navigating more changes and challenges than ever before. One of the most transformative forces shaping this space is artificial intelligence (AI). As AI technologies mature, they’re becoming a critical accelerator for TPRM.
AI doesn’t just add speed—it fundamentally enhances the way we manage vendor risk. By automating assessments, analyzing vast datasets, and continuously monitoring for changes in vendor posture, AI enables teams to move from reactive to proactive. What once took weeks can now be done in minutes, without sacrificing depth or accuracy.
The result? Faster decisions, stronger insights, and more resilient supply chains. As AI continues to evolve, it’s not just enhancing TPRM—it’s redefining what’s possible
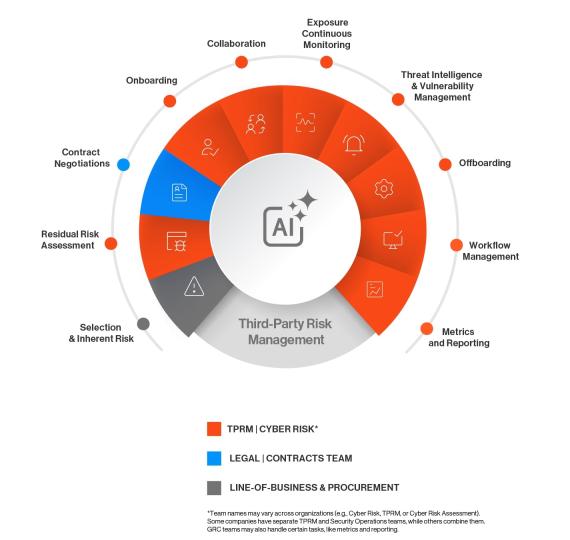
What does a TPRM program entail?
A third-party risk management program manages risks associated with third-party vendors, customers, or regulators end-to-end. This involves collecting critical vendor information, assessing their security posture, tracking what data and systems they have access to, understanding what regulations and internal policies apply to them, and more.
Vendor considerations for TRPM:
- Which of your vendors has access to critical information?
- What types of data do they have access to? Think Personally Identifiable Information (PII) or Nonpublic Personal Information (NPI)
- Do their services help your organization to comply with laws, regulations, and standards, such as HIPAA, PCI-DSS, CCPA, GDPR, etc.?
- Do they have an incident response plan?
- Do they comply with any industry standards?
- How will they act in case of a data breach?
Ultimately, the goal of TPRM is for you to know how much risk you are taking by engaging with a vendor, and to have enough information to decide if you want to pursue that relationship.
How does TPRM fit in the overall enterprise risk management strategy?
TPRM is a critical component of a comprehensive Governance, Risk and Compliance or GRC program. GRC manages enterprise risk on a much broader scale, including external risks, issues of corporate governance and compliance with regulatory requirements. Legal, contractual, internal, social, and ethical parameters, as well as industry regulations, fall under the GRC umbrella.
Therefore, every insight from a proper due diligence and vendor risk assessment process, obtained as part of a third-party risk management program, is a valuable input for the overall enterprise risk management and strategic decision making that GRC owns. That is why, in many organizations, TPRM is conducted by the GRC team, though a dedicated department is always preferable.
Benefits to having a third-party risk management program in place
There are a handful of benefits to reducing risk in your supply chain; to name a few:
- Consistency in rating the the security posture of third-parties
- Operational efficiency, with a lower cost and defragmentation of the overall third-party risk management process
- Ensuring that the vendor ecosystem adheres and complies with contractual commitments
- Access to data to make informed decisions on third-party relationships
Learn how Bitsight TPRM can bring your third-party risk management program to new heights and ensure a secure relationship with third party-vendors to avoid unnecessary risks.
Where does Bitsight help?
Bitsight has been at the forefront of third-party cyber risk management for over a decade, supporting everything from Fortune 500 enterprises to insurers and government agencies. What sets us apart is our ability to help organizations measure risk at scale—across hundreds or even thousands of vendors—within moments.
Today, customers use Bitsight’s Ecosystem products to:
- Enhance risk-based decision-making during onboarding and throughout the vendor lifecycle.
- Map out the extended attack surface, including third and fourth parties.
- Automate due diligence, cutting down manual reviews and engaging directly with vendors.
- Assess vendor security postures objectively—no need for questionnaires upfront.
- Detect posture changes, exposures, and anomalies that signal a need for remediation.
- Benchmark performance, monitor exposure trends, and proactively reduce risk.
But the value of this data goes beyond TPRM. Our solutions are used to:
- Support investment decisions by gauging governance through cyber signals.
- Optimize cyber insurance portfolios, improve underwriting, and reduce claim risks.
- Deliver macro-level risk intelligence, from regional threat trends to critical infrastructure assessments.
- Drive KYC and due diligence use cases, helping customers identify unseen risks across digital connections and infrastructure.
This breadth is why our TPRM capabilities sit at the heart of a nearly $200M business—with $103M coming from products tied directly to vendor risk, cyber insurance, investment insights, and national security use cases.
TPRM isn’t just a process—it’s a lens into how resilient your business ecosystem really is. At Bitsight, we’re not just measuring risk. We’re helping organizations act on it—confidently, at scale, and in real time.



