New! The Security Ratings report is now the Executive Report. Request your report to see enhanced analysis such as your rating, likelihood of ransomware incidents, and likelihood of data breach incidents.
Beyond Heartbleed, POODLE & FREAK: SSL Vulnerabilities Persist

Bitsight’s Third Annual Bitsight Insights Industry Benchmarking Report looked at some of the major SSL vulnerabilities affecting organizations, including Heartbleed, POODLE and FREAK. Bitsight’s analysis found that a sizeable number of companies across all industries were still running services that were vulnerable to these flaws. As mentioned in our report, businesses can leverage this information as a measure to ensure that proper controls are being met internally. In addition, companies can gain insight into the performance of their key third party vendors when it comes to ensuring that they aren’t running vulnerable services.
Below is a table showing the percentage of organizations in each industry running services with these major vulnerabilities.
|
Industry |
Heartbleed |
FREAK |
POODLE |
|
Finance |
2.6% |
30.4% |
69% |
|
Government |
7.6% |
50.4% |
79% |
|
Retail |
5.6% |
37.1% |
72.2% |
|
Energy/Utilities |
5.2% |
40.5% |
74.8% |
|
Healthcare |
4.4% |
43.4% |
73.5% |
|
Education |
23.2% |
75.6% |
90.7% |
After great feedback, interest and coverage on the report’s findings, Bitsight’s Data Science team decided to take a deeper dive into our data to derive more insights around configuration issues - especially as they relate to Secure Sockets Layer (SSL), a widely-used protocol to secure communications over the Internet.
1. SSL V3 is the most common vulnerability observed by Bitsight.

The use of SSL version 3 implies vulnerability to POODLE and the protocol itself was recently deprecated by the IETF. In addition to POODLE, a significant number of companies are vulnerable to the Logjam attack via the usage of widely shared Diffie-Hellman primes. Over half of companies still use SSLv2 which has been obsolete for nearly 20 years and not used by any modern browsers. Forty percent of companies are vulnerable to the FREAK attack which used export grade ciphers and twenty percent of companies still use insecure MD5 checksums for certificate signatures.
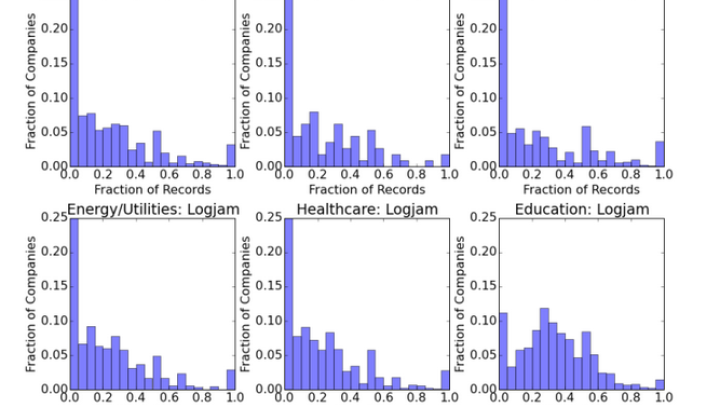
2. Logjam, like other brand name vulnerabilities, is still a major problem across all industry sectors.
Logjam was another major vulnerability that was announced in May 2015 that affects TLS connections using Diffie-Hellman ciphers, according to the OpenSSL blog. Similar to what we have seen with Heartbleed, POODLE and FREAK, this vulnerability affects companies across all industries. Some industries, such as Education, are more affected. The charts below show histograms of the fraction of SSL records vulnerable to Logjam by industry. Although many companies have zero to five percent of records affected by Logjam, others have a considerable fraction of vulnerable records.
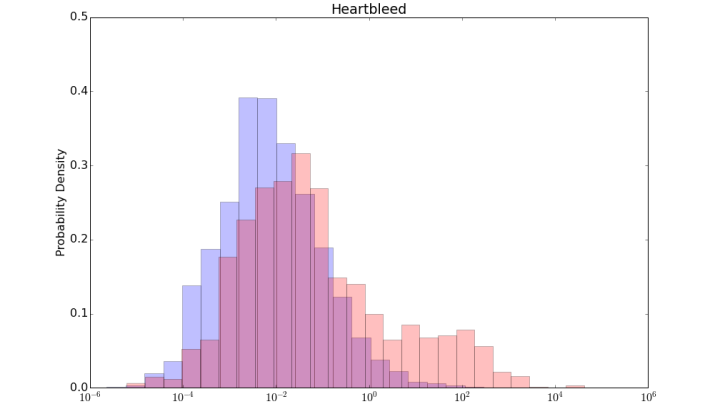
3. Companies that are vulnerable to Heartbleed have more botnet infections per person.
Probably the most interesting finding was that companies running services that were vulnerable to Heartbleed also had a greater number of botnet infections per employee at that company. The chart below shows histograms of botnet events observed per employee for companies with at least one server vulnerable to Heartbleed and those without any vulnerability to Heartbleed. Note that the horizontal axis of this plot is logarithmic. The difference in these histograms is significant with the means differing by a factor of more than 10. While there is no obvious causal relationship between being vulnerable to Heartbleed and having botnets, it is an interesting data point that may suggest companies with better security hygiene suffer from fewer infections.
Conclusion
As evidenced in the latest Bitsight Insights and this post, companies across all business sectors are experiencing difficulties in maintaining up to date SSL certificates. Leveraging this information, businesses can begin to put controls in place to ensure that vulnerable services are not running across their network ecosystem. By continuously monitoring SSL configurations across a network, organizations can proactively manage the risk of cyber attacks that take advantage of these issues. While many news headlines focus on advanced persistent threats or Chinese hackers, businesses can - and should - take steps to mitigate the risks posed by well-publicized SSL vulnerabilities. In addition, businesses can begin to gain insight into where these vulnerabilities may lie across their third party vendor network ecosystems, and communicate with vendors about remediating threats.


