The 2025 State of Cyber Risk and Exposure report reveals why security leaders are under pressure: AI-driven threats, expanding attack surfaces, and misalignment with business priorities. Based on global survey data, it surfaces the root causes behind today’s risk fatigue—and what mature organizations are doing differently.
Why Patching Cadence Should Be a Risk Priority in 2026
Tags:


Patching cadence is a critical component of maintaining an organization’s cybersecurity posture. It refers not just to whether patches are applied, but how quickly and consistently vulnerabilities are addressed across systems and software. A regular, timely patching process reduces the window of exposure to known vulnerabilities, limiting opportunities for exploitation and strengthening overall vulnerability management.
Most organizations understand the importance of patching and have programs in place to do it. The problem is that many of those programs move too slowly to keep up with today’s threat environment. Vulnerabilities are weaponized faster than ever, and attackers routinely exploit known issues within days or even hours of disclosure. In this context, patching that happens eventually is often indistinguishable from patching that never happens at all.
Today, speed and consistency of patching matters more than coverage alone. Applying every patch months late provides far less risk reduction than rapidly addressing the most exploitable vulnerabilities. When vendors release security updates, delays directly translate into risk. Leaving systems unpatched after a fix is available is like leaving a door unlocked after being warned about suspicious activity nearby. The longer the delay, the greater the likelihood that someone will take advantage of it.
Fortunately, organizations have more tools than ever to improve patching speed. Automation platforms such as Microsoft System Center Configuration Manager, Ansible, Chef, and Puppet can streamline deployment across large environments. Cloud providers also offer native patching services that make it easier to schedule and apply updates consistently. Yet despite these capabilities, patching remains uneven, especially in complex environments.
Large enterprises and operational technology environments such as manufacturing often face significant patching challenges due to scale, legacy systems, and uptime requirements. In some cases, applying patches quickly is difficult or temporarily impossible. When that happens, organizations must rely on compensating controls such as restricting access to vulnerable services, disabling unnecessary functionality, and closely monitoring for signs of exploitation. These measures help reduce risk, but they do not eliminate the underlying exposure.
As attack timelines continue to shrink, patching cadence is emerging as a more meaningful indicator of cyber risk than patch status alone. Understanding how fast an organization can respond to known vulnerabilities is becoming essential to assessing its true security posture.
The threat landscape has outpaced traditional patching
According to insights from our Bitsight Threat Intelligence solution, the vulnerability landscape has shifted in ways that significantly increase risk for organizations that patch slowly. The time between public disclosure and active exploitation has continued to shrink, with threat actors weaponizing vulnerabilities almost immediately after details become available, turning each disclosure into a real world attack opportunity.
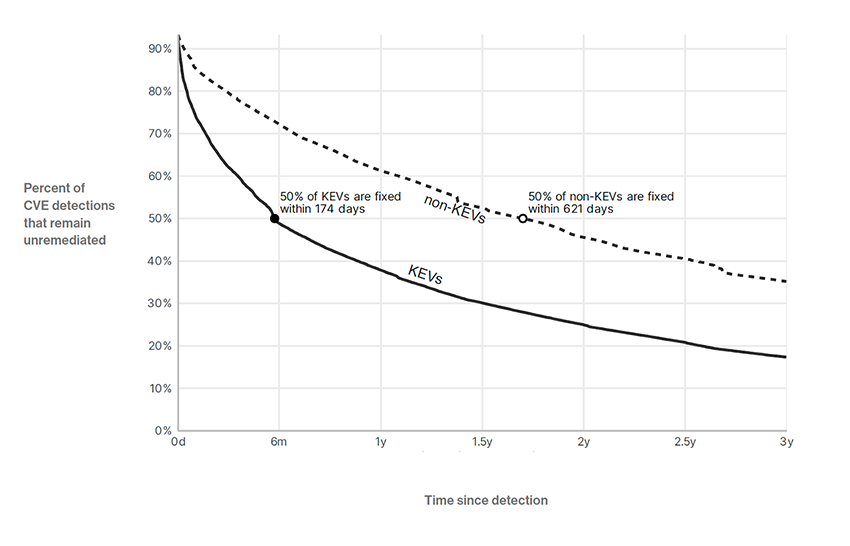
At the same time, the volume of disclosed vulnerabilities has surged, with a reported 40 percent increase reaching roughly 39,000 disclosures in 2024, overwhelming security teams and making effective prioritization more difficult. Bitsight data also shows that high severity vulnerabilities increased by 78 percent between 2020 and 2021, further compounding the challenge. As attacker access to exploit code becomes more widespread, a growing gap has emerged between disclosure and remediation, leaving many organizations exposed.
This risk is not theoretical. In a realistic scenario increasingly reflected in incident response data, a single unpatched vulnerability that is more than 25 years old can be exploited in a widely used vendor platform, forcing the vendor to shut down systems to contain the breach. CVE-1999-0024 is one such example. Now over two decades old, attackers continue to exploit this DNS cache poisoning vulnerability due to missed patching.
When exploited, it allows forged responses to be injected into a DNS resolver’s cache, silently redirecting users who rely on that resolver to infrastructure controlled by an attacker. DNS cache poisoning remains a potent and prevalent third-party attack vector. That outage then ripples outward, disrupting customers and downstream partners that rely on the service, including third and fourth parties with no direct control over the vulnerable system.
Recent studies show that 15% of open DNS resolvers remain susceptible to these types of flaws, underscoring the scale of exposure. In the hands of a supply chain attacker, a single poisoned resolver at an ISP, hosting provider, or other vendor could redirect traffic for thousands of downstream users simultaneously, enabling credential harvesting through fake login portals or even the distribution of malicious software updates to multiple organizations at once. As attackers move laterally, sensitive customer data and personally identifiable information is exposed, triggering breach notifications, regulatory scrutiny, and potential legal action. What began as a long ignored vulnerability escalates into a mass service disruption, long term reputational damage, and material financial loss. According to Bitsight observations, incidents like these underscore that age does not reduce risk. In many cases, it increases it, especially when legacy vulnerabilities persist across shared technology ecosystems.
Why patching cadence is a better risk signal than patch status
Patch status provides only a snapshot of an organization’s security posture at a single point in time. While it shows whether systems are patched at the moment of measurement, it does not capture how consistently or quickly an organization responds to newly disclosed vulnerabilities. In contrast, patching cadence reflects ongoing behavior over time, making it a more reliable indicator of sustained risk management behavior.
Patching cadence also provides insight into operational maturity. It reveals whether security and IT teams can consistently identify, prioritize, and remediate vulnerabilities as conditions change. According to Bitsight Threat Intelligence, organizations that maintain consistent remediation timeliness across reporting periods tend to exhibit more stable and predictable vulnerability management outcomes, even as vulnerability volumes and severity fluctuate. Lower variance in remediation timelines often signals standardized workflows, clear ownership, and repeatable execution. These characteristics are commonly associated with more mature security programs and greater resilience.
Snapshot-based compliance metrics can create a false sense of security. Many organizations appear compliant during audits or assessments yet remain exposed due to delayed or inconsistent remediation cycles. Bitsight observations indicate that some organizations maintain acceptable patch levels at reporting checkpoints while repeatedly leaving high risk vulnerabilities unresolved for extended periods. These gaps often persist between reporting cycles, creating windows of exposure that attackers actively exploit.
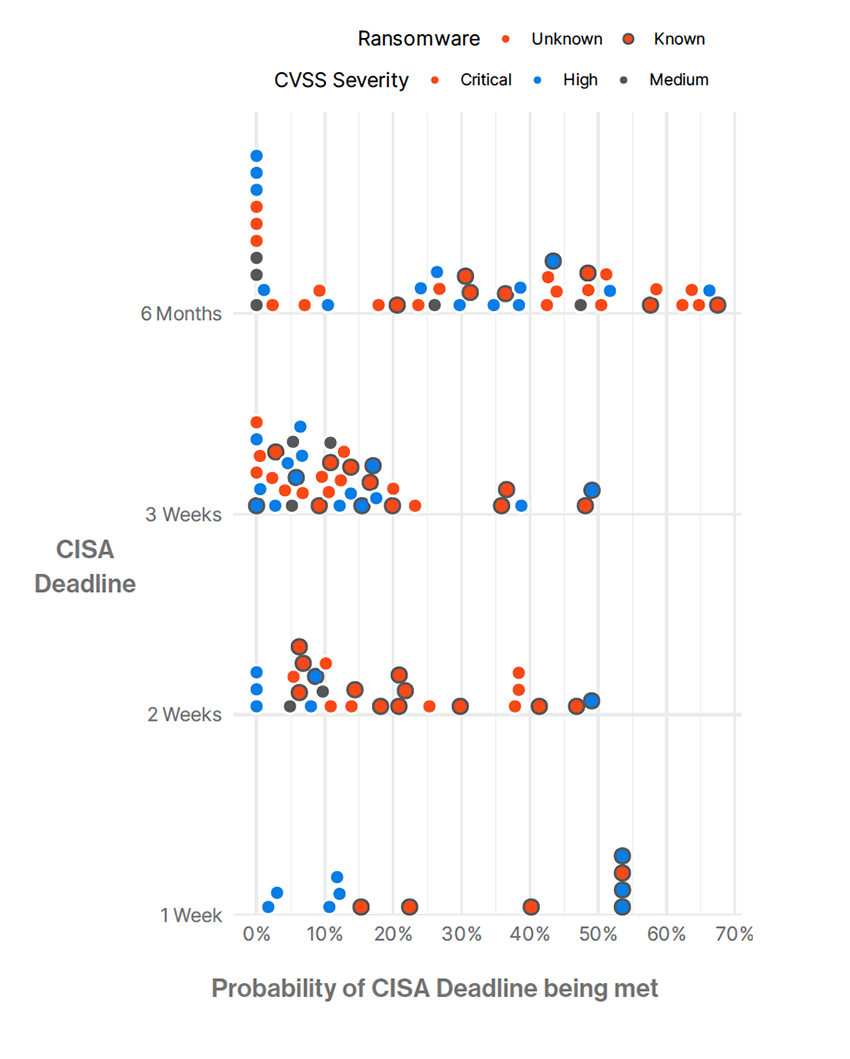
Examples from incident data further highlight this disconnect. Organizations that patch infrequently but in large batches may temporarily reach compliance thresholds, yet still experience breaches tied to vulnerabilities that were disclosed weeks or months earlier. According to our threat intelligence, attackers consistently target these delays, focusing less on whether a vulnerability exists and more on how long it remains unpatched.
Ultimately, patching cadence shifts the focus from static compliance to dynamic risk management. It measures how an organization behaves when new threats emerge, making it a more accurate and actionable signal for assessing cyber risk across internal environments and extended third-party ecosystems.
Attack surface expansion and its impact on patching cadence
Attack surface definition
An attack surface is the total sum of all digital and physical entry points that an attacker can probe or exploit to gain unauthorized access. This includes infrastructure components, network interfaces, applications, workflows, and the processes that support them. As environments grow more complex, the number of potential entry points increases, raising the likelihood that vulnerabilities will be missed or patched too slowly.
Growth factors driving attack surface expansion
The enterprise attack surface continues to expand due to widespread adoption of cloud platforms, SaaS applications, mobile devices, IoT systems, and third party tools. Hybrid and remote work models have introduced new endpoints and network paths that require ongoing security oversight. Each additional system increases the number of assets that must be inventoried, monitored, and patched, making consistent patching cadence more difficult to maintain.
AI-driven attack surface growth
AI adoption has introduced a rapidly expanding and often poorly understood attack surface. Many organizations deploy AI tools without full visibility into data flows, model training processes, or integration points. This creates new opportunities for attackers to exploit exposed interfaces, insecure configurations, or improperly governed data pipelines. As AI systems evolve quickly, traditional patching processes often struggle to keep pace.
Visibility challenges across the enterprise
Lack of visibility remains one of the biggest obstacles to effective attack surface management. Many organizations do not fully understand how employees are using consumer and enterprise AI tools, including uploading sensitive data into platforms like ChatGPT. These blind spots increase the risk of data exposure and make it harder to identify where vulnerabilities exist or which systems require urgent remediation.
Security implications of an expanding attack surface
Every connected asset represents a potential entry point for threat actors, particularly when ownership and accountability are unclear. As the attack surface grows across internal systems and third party ecosystems, gaps in patching cadence become more likely. Without continuous visibility and prioritization, organizations may unknowingly leave exploitable vulnerabilities exposed for extended periods.
Attack surface management strategies
Effective attack surface management relies on continuous and automated discovery of assets and exposures as they appear. This includes mapping internal, external, and previously unknown systems to ensure they are monitored and included in vulnerability and patch management workflows. Continuous reconnaissance allows organizations to detect new risks early rather than reacting after exploitation occurs.
Proactive measures to reduce risk
Organizations should prioritize regular mapping, monitoring, and testing of their attack surface to maintain a defensible security posture. Continuous monitoring helps validate that patches are applied as expected and that new assets do not introduce unmanaged risk. Strong governance and repeatable processes are essential for sustaining patching cadence as environments scale.
The cost of slow patching
Slow patching materially increases the likelihood of breaches and ransomware incidents. According to Bitsight Threat Intelligence, threat actors consistently exploit known vulnerabilities where patches are available but delayed, prioritizing ease of access over technical novelty. When remediation timelines stretch, attackers gain predictable windows to deploy commodity exploits, escalate privileges, and establish persistence before defenders can respond.
Beyond breach risk, delayed patching creates regulatory and contractual exposure. Many compliance frameworks and customer agreements require timely remediation of known vulnerabilities, particularly those rated high or critical severity. Failure to meet these expectations can result in fines, contract termination, or increased scrutiny following an incident. In third party environments, slow patching can also cascade risk downstream, exposing partners and customers who depend on shared systems.
Reputational damage is often the most lasting consequence. Breaches tied to long known vulnerabilities are difficult to defend publicly and erode trust with customers, regulators, and investors. When incidents are traced back to vulnerabilities that were disclosed months or years earlier, organizations face increased pressure to explain not just what happened, but why known risks were allowed to persist.
What good patching cadence looks like in 2026
Effective patching cadence in 2026 is defined by prioritization, adaptability, and consistency. Rather than relying on blanket service level agreements, mature organizations apply risk based prioritization that considers exploit activity, asset criticality, and exposure. This approach ensures that the vulnerabilities most likely to be targeted are addressed first, even if lower risk issues are deferred.
Aligning patch timelines with real world exploit activity is becoming essential. Vulnerabilities actively exploited in the wild present exponentially higher risk than those without known weaponization. Organizations that integrate cyber threat intelligence into patching decisions can shorten remediation timelines where it matters most.
Measurement also matters. Leading organizations track median time to patch, as well as variance across asset classes and business units. These metrics provide visibility into consistency and reveal where operational bottlenecks exist. Over time, improving these trends is a stronger indicator of reduced risk than achieving perfect patch coverage.
How security and risk leaders should respond
Security and risk leaders should elevate patching cadence to a board level discussion. Framing cadence as a business risk metric helps shift the conversation from technical compliance to operational resilience. Organizations that treat remediation speed as a strategic priority are likely to reduce exposure more effectively than those focused solely on audit driven metrics.
Patching data should also be integrated into enterprise risk scoring and third party assessments. Understanding how quickly internal teams and vendors remediate vulnerabilities provides valuable insight into systemic risk across the ecosystem. This is particularly important as third- and fourth-party incidents continue to rise.
Finally, leaders should focus on trend improvement rather than perfection. In complex environments, some delays are inevitable. What matters most is whether patching performance is improving over time and whether response speed aligns with threat activity. Continuous improvement is a more realistic and effective goal than absolute compliance.
Conclusion
Patching cadence has emerged as a leading indicator of cyber risk because it reflects how organizations behave under pressure, not just how they score at a single moment in time. The ability to consistently remediate vulnerabilities quickly is increasingly correlated with reduced breach likelihood and improved resilience.
As attack timelines continue to shrink and enterprise attack surfaces expand, patching speed is no longer just an IT concern. It is a business risk issue that affects operations, reputation, and customer trust. Organizations that continue to measure patching performance through static status checks risk overlooking the very gaps attackers exploit.
Reassessing how patching is measured, prioritized, and reported is essential for 2026 and beyond. By shifting focus from patch status to patching cadence, organizations can better align security efforts with real world threat behavior and meaningfully reduce cyber risk.



