Global State of Exposure: OpenSSL Vulnerabilities

The OpenSSL Project has issued patches for two severe vulnerabilities affecting the project’s encryption libraries used to encrypt Internet communications. At first, the vulnerabilities were thought to be practically exploitable and therefore dangerous, but recent developments show that these vulnerabilities may not be as serious as initially thought.
New Bitsight research finds that many organizations are still affected by the OpenSSL vulnerabilities, tracked as CVE-2022-3786 and CVE-2022-3602. This blog identifies the most affected sectors and nations around the world. In addition to directly impacting affected organizations, these vulnerabilities also have the potential to impact third-party vendors and suppliers, once again highlighting the need for effective vulnerability management and a comprehensive third-party risk management program.
What is OpenSSL?
The OpenSSL Project was founded in 1998, consisting of cryptographic libraries used to encrypt Internet communications. These libraries provide open source implementations of the SSL and TLS protocols – the same protocols that put the “S” in HTTPS. If a site does not use SSL/TLS encryption, then data transmitted over the connection may be intercepted and read by an attacker.
OpenSSL has played a critical role in providing the tools necessary to properly implement the SSL/TLS protocols. The library helps systems and applications generate private keys, checksums, Certificate Signing Requests (CSRs), and a variety of other tasks needed to manage certificates and perform encryption and decryption of communications. The library is the dominant library for web servers – two-thirds of them use OpenSSL.
Simply put, OpenSSL plays a critical role in ensuring Internet communications are kept secure.
How is OpenSSL vulnerable and what is the potential impact?
OpenSSL issued patches for two vulnerabilities, tracked via the following CVEs:
CVE-2022-3786: Denial of service (DoS) via buffer overflow
A buffer overflow is a common form of memory corruption, where successful exploitation can allow attackers to exceed the bounds of allocated memory buffers. This can sometimes result in remote code execution, but in the case of CVE-2022-3786, it is much more likely to be used to crash the affected application resulting in a denial of service.
Denial of service attacks can result in a variety of business complications. If your systems are rendered inoperable for sustained periods of time, your organizations could face significant financial losses and reputational damage. And the third-party implications are just as serious – if a critical business partner experiences a DoS attack, they could be unable to deliver services you need for your business to operate.
CVE-2022-3602: Remote code execution (RCE) via buffer overflow
Originally assessed by OpenSSL as “critical,” this vulnerability is an arbitrary 4-byte stack buffer overflow that could lead to RCE. An attacker executing code remotely on any system is a big deal but the latest information suggests this vulnerability may not be as serious as initially thought.
Remote code execution is among the most serious of attacks. An attacker with the ability to remotely execute code on your machines could lead to data breach and/or data exfiltration, malware deployment, lateral movement into other systems, service loss, and more. All of these scenarios present critical business threats – for example, if you’re responsible for your partners’ data and you get breached, you could end up suffering significant financial loss due to terminated relationships.
Bitsight’s observations into OpenSSL risk
As serious as the issue remains, it turns out that the concerns about RCE might have been overblown in early coverage of the vulnerability. In fact, CVE-2022-3602 was initially described as Critical but based on “mitigating factors,” the vulnerability was downgraded to High. OpenSSL even publicly stated “we are not aware of any working exploit that could lead to remote code execution, and we have no evidence of these issues being exploited as of the time of release of this post.” Nonetheless, Bitsight security experts determined that RCE is possible but only under certain circumstances, concluding that exploitation for code execution is highly dependent on how the application is compiled and configured.
The threats presented by CVE-2022-3786 are also nuanced. Buffer overflow attacks can lead to forced overwriting of data but Bitsight’s assessment is that attacker control of the data is limited, and successful exploitation likely results in a denial of service. Still, denial of service presents serious complications if fully realized.
We also analyzed the scope of affected organizations, detailing their respective sectors and geographical presence around the globe.
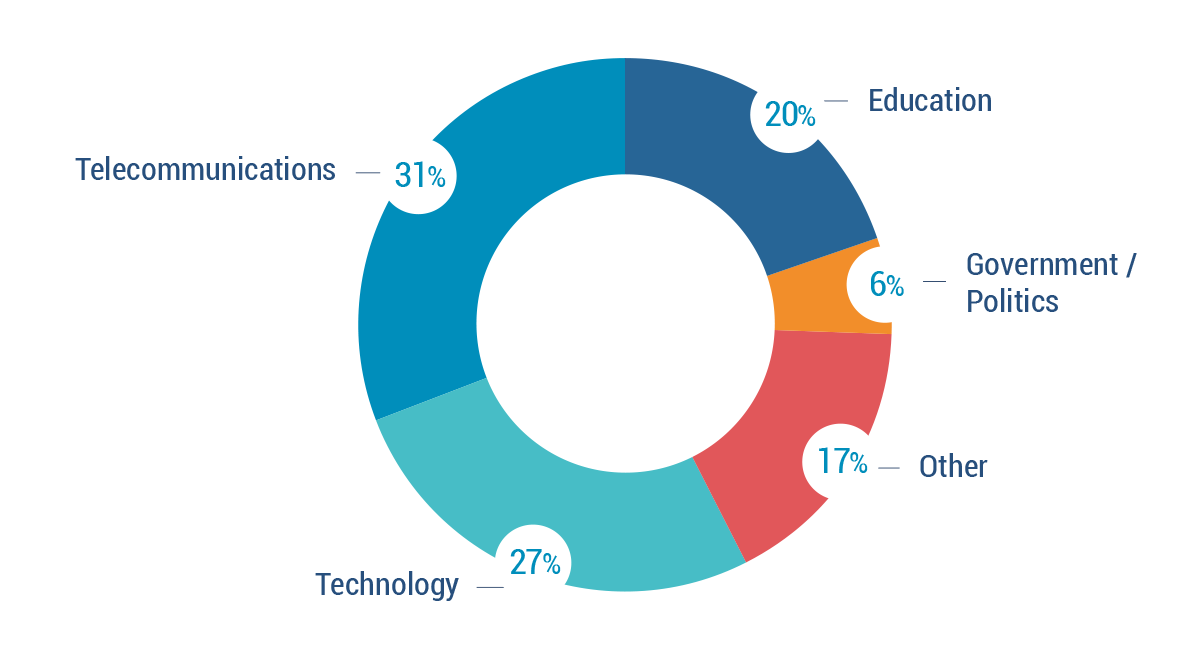
Many organizations still impacted
Bitsight observes over 700 organizations, from a variety of sectors around the globe, to still be affected by OpenSSL vulnerabilities. Telecommunications, technology, and educational organizations comprise the majority of affected organizations. Affected organizations are those still running vulnerable versions of OpenSSL.
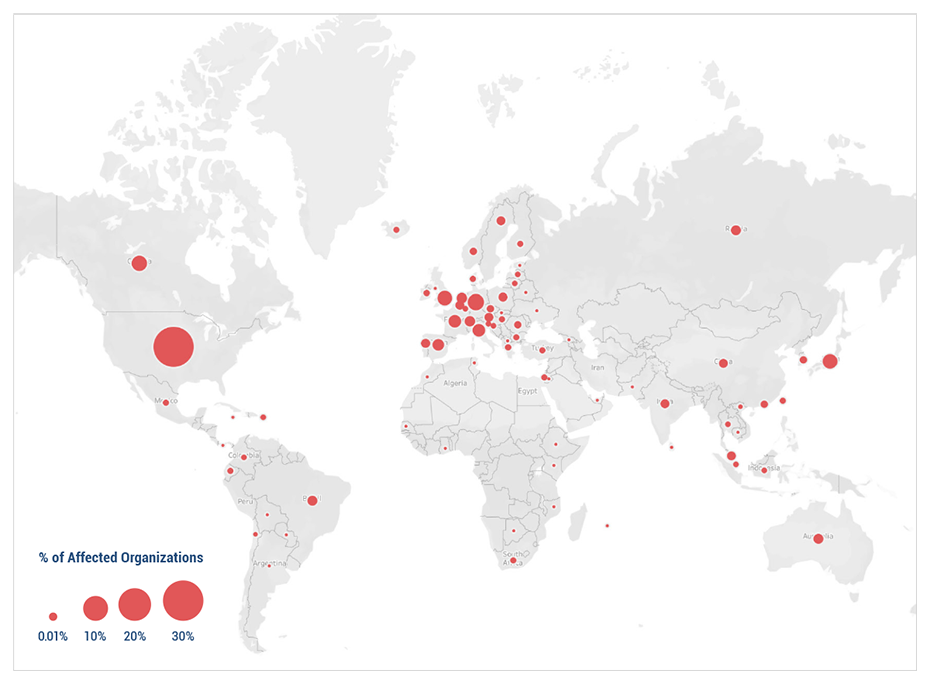
Geographic scope is significant
Presently affected organizations are largely headquartered in the United States but Europe and Asia make up a significant portion of affected organizations.
Recommendations for security professionals
It is critical that your organization quickly and effectively identify vulnerabilities like the ones discussed here. Every minute your organization remains unknowingly vulnerable is another minute an attacker can leverage to generate an exploit and attack your weak points. Bitsight recommends organizations follow these three guidelines when remediating these OpenSSL vulnerabilities and similar ones:
Prioritize implementing patches
Patching cadence measures how many systems within an organization’s network are affected by important vulnerabilities, and how quickly the organization remediates them. This area of your cybersecurity program warrants much attention – the world’s largest insurance broker, Marsh McLennan, found poor patching performance as measured by Bitsight to be most correlated with the likelihood of cybersecurity incidents. In the context of the OpenSSL vulnerabilities, strong patching cadence looks like ensuring applications using OpenSSL are pulling patched updates from the developer.
Quickly identify supply chain threats
You don’t need to be directly affected by these vulnerabilities to be impacted. The OpenSSL vulnerabilities can lead to complete system takeover, denial of service, and other serious consequences. If one of your critical supply chain partners falls victim to one or more of these attacks and experiences business disruption, your organization could in turn be impacted – delayed shipments and deliveries, unfulfilled digital services, and more. An event like this could significantly impact your reputation and ability to deliver critical business services.
With the consequences as serious as ever before, it’s critical that your organization leverage all digital tools at your disposal. Of particular urgency should be your ability to rapidly and efficiently detect vulnerabilities in your system, and the systems of your third-party ecosystem. Bitsight Third-Party Vulnerability Detection allows third-party security teams to fight risks effectively without overexerting their resources. With industry-leading vendor risk data, security teams can prioritize vendor exposure to critical vulnerabilities and respond more quickly and with more precision.
Only onboard the most secure vendors
Managing third-party cyber risk starts with onboarding the right vendors and partners in the first place. Bitsight VRM, in combination with the Bitsight Risk Rating, allows you to confidently onboard vendors that meet your cybersecurity control requirements.
Reach out to Bitsight to learn more about how we can help your organizations reduce the risk of a cybersecurity incident.