From the Server Room to the Board Room: Actionable Security Metrics
Tags:

As we highlighted in a recent blog post, a diverse range of companies utilize Bitsight Security Ratings to manage cyber risk. Many of our customers are actively using these ratings to manage vendor risks, screen mergers and acquisition targets, underwrite cyber insurance and benchmark security performance. Regardless of how customers use these ratings within their security and risk programs, it is important that the ratings are both actionable and accurate.
Data accuracy is a fundamental principle of Bitsight; any security vendor can provide mountains of data but Bitsight is a leader in creating ratings based on actual evidence of system compromise. Numerous customers have vetted Bitsight’s data and network footprint mapping in order to ensure that they can leverage this information for important business decisions. Yet even with highly accurate ratings, companies need to address perhaps the most fundamental question in the rollout of a ratings solution: Are the ratings actionable?
Risk and security professionals constantly want to determine a company’s risk of a data breach, whether it be to analyze their own company’s security risk or the risk of a third party vendor, insurance applicant or acquisition target. Similar to how lenders use credit scores to measure the risk of a loan default, ratings on cyber security need to effectively inform users of the major consequence of security weaknesses: a data breach. Data breaches have been shown to cause reputational and financial damage to all companies involved. Perhaps more worrying, Verizon recently highlighted that 70% of breaches affect a third party - a third party that may have had no insight into the cause of the breach. This paradigm is now changing, as Bitsight provides deep insight -- and is the only security ratings platform that is indicative of the risk of a publicly disclosed data breach.
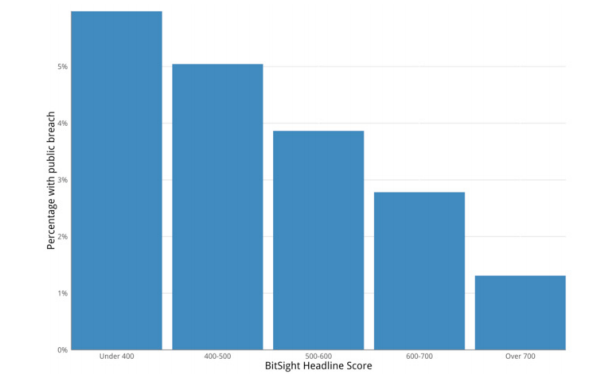
To determine this, Bitsight recently analyzed the ratings of 27,458 companies. By comparing ratings to a database of 2,671 digital data breaches provided by leading insurance consultancy Advisen, Bitsight was able to uncover a clear correlation between ratings and breaches. Specifically, Bitsight found that companies with ratings of 400 or below were more than five times likely to experience a publicly disclosed data breach than organizations with ratings of 700 or above.
To learn more, you can download this Technical Note on the study and methodology. If you would like an even deeper look into specific risk vectors involved in the ratings of security posture, I strongly recommend attending our upcoming webinar on November 20, From Signal to Action: Security Metrics that Drive Business Decisions. Beyond an overview of the ratings and how they correlate to breaches, Bitsight’s CTO Stephen Boyer and Senior Data Scientist Jay Jacobs will be diving into how security and risk professionals can view different security metrics and drive change within their cyber risk management programs.


