Don’t let AI adoption outpace security. Establish an AI Council, vet vendors, and enforce policies to keep AI under control. Discover the framework top enterprises use.
Why You Should Care About Vendors Using AI Products, and How Bitsight Helps You Find Out
Tags:

Artificial intelligence—it’s a term you’ve likely encountered more than once today, and this won’t be the last. And while it reshapes how businesses operate, it’s also introducing new risks. As organizations embrace AI-powered tools for efficiency and innovation, it becomes essential to understand what technologies your vendors rely on, and what those choices mean for your cybersecurity posture.
This is especially true for fourth-party relationships, or the vendors that your vendors rely on. You can’t mitigate what you can’t see, and when it comes to AI, the invisible can be unpredictable. Here’s why it matters and how Bitsight helps bring it into view.
The AI adoption blind spot
AI brings power but also complexity. Whether it’s natural language processing (NLP) in a customer service platform or machine learning (ML) in fraud detection, these technologies often integrate deeply with sensitive systems and data. Unfortunately, many organizations have limited visibility into where and how these tools are embedded across their extended digital supply chain.
As a result, companies face key challenges:
- Unknown exposure to AI-driven products with unvetted security postures
- Difficulty verifying data handling practices involving large language models
- Limited means of prioritization when incidents involve a cascade of fourth-party dependencies
In short, you may not even know that an AI product buried in your vendor’s tech stack poses a risk until it’s too late.
How Bitsight brings AI dependencies to light
We’ve consistently heard from security and risk leaders that understanding where AI technologies exist within the supply chain is a growing priority. With Bitsight Continuous Monitoring, you have a powerful tool to meet that need. Its built-in fourth-party risk management capabilities provide clear visibility into the products used by both your vendors and their vendors, making it easier to uncover AI dependencies and evaluate their potential impact.
Pro tip: Use Continuous Monitoring to detect AI product dependencies
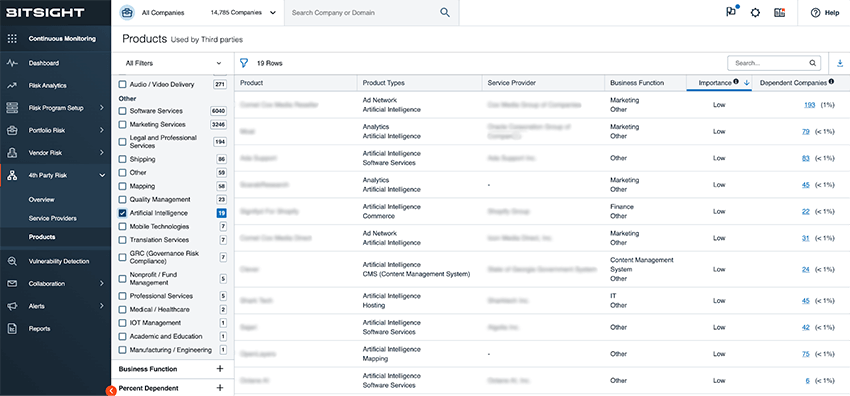
Within the Bitsight platform:
- Navigate to the “Products” table under your vendor’s profile.
- If any AI products are identified, including those related to natural language processing or machine learning, a new filter labeled Product Type > Artificial Intelligence will appear.
- Apply the filter to isolate technologies categorized as AI.
- Click into any product to view metadata and a breakdown of confirmed and suspected dependencies, backed by Bitsight’s multi-source detection methods.
This capability is part of what makes Bitsight Continuous Monitoring unique. It goes beyond assessing direct vendors by exposing AI tools in your extended supply chain, providing evidence-based insight into supplier relationships, and enabling you to communicate risk clearly across both technical and business audiences.
Unlike other solutions that stop at technical indicators, Bitsight provides both depth and context to help you take action. We classify confirmed and suspected relationships with clear evidence certainty, drawing from diverse data sources and continuously updating insights through our globally scaled, battle-tested data engine.
This combination, plus being subscribed to the Bitsight rating, gives you more than a list of dependencies—it delivers the context you need to act. Once an AI vendor is identified in your supply chain, Bitsight’s integrated workflows help you engage vendors with confidence, prioritize response during critical events, and communicate clearly with stakeholders at every level.
Final thoughts
AI can drive innovation or introduce new risks. At Bitsight, we are integrating AI into our workflows to enhance the impact of our actionable, risk-correlated cyber intelligence. To explore how AI-powered solutions can support your program, sign up for a free demo.



