Get a report built on your actual external infrastructure—domains, IPs, certificates, cloud assets—and benchmarked against real-world breach data.
How Does Bitsight Work? A Look At Security Ratings & How They're Used
Since our foundation in 2011 as the first company to provide a rating for measuring a company’s cyber security, Bitsight has become the world-leading security ratings provider. Bitsight is used around the world by industry leaders, country governance systems, as well as smaller organizations alike to take control of their cyber footprint, using safe and objective rating techniques. What does Bitsight do to stand apart from others in the security industry?
What are Bitsight Ratings?
Bitsight offers the most widely adopted Security Ratings solution by following our mission to change the way the world prioritizes and manages cyber risk. Bitsight’s security ratings software helps companies:
- Understand their own security performance, as well as the performance of their vendors, clients, and other third and fourth parties.
- Continuously assess cyber risks within their digital ecosystem.
- Have the confidence to make faster, more strategic cyber risk management decisions using objective, verifiable, and actionable data.
What are security ratings?
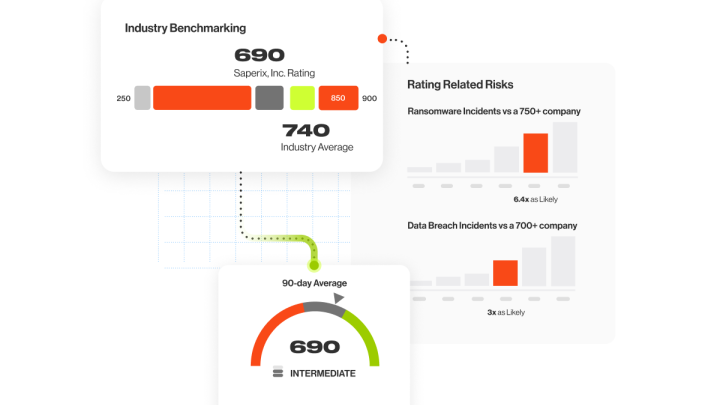
Security Ratings can be compared to the use of credit scores, which we are mostly familiar with when it comes to larger purchasing decisions or receiving a loan. Bitsight’s ratings range from 250 to 900, with a higher rating indicating better cybersecurity performance. These scores are used by CISOs, CIOs, security managers, underwriters, auditors, and many others to address a company’s procedures and level of risk awareness and management.
Security ratings are objective, outside evaluations and do not require input from any company involved. These ratings are continuously updated—and because Bitsight is a software-as-a-service (SaaS) solution, ratings can be accessed in the Bitsight Security Ratings Platform from any online browser.
Security ratings take into account things like historical security performance and performance change over time. Alerts are generated to notify users of significant changes in their ratings or those of their third parties, and actionable information is provided to mitigate the specific risk associated with the alert. The Bitsight platform is designed to provide a user-friendly experience with little-to-no training needed to understand the data.
What goes into the Bitsight Security Rating calculation?
Bitsight formulates security ratings by gathering security information from billions of stored data points and events that happen online. From this data, we’re able to see the following:
- Indicators of compromise.
- Infected machines.
- Proper or improper configuration of cybersecurity controls.
- Positive or poor cyber hygiene.
- Potentially harmful user behaviors.
The data is then applied to a network footprint of any company or organization to then be run through an algorithm that analyzes the data for severity, frequency, duration, and confidence indicators. With this information, Bitsight is able to create an overall rating of an organization’s security performance.
Bitsight invests heavily in research and development to empower customers with objective, verifiable, and actionable cybersecurity data. Check out the video below for more details.
How to apply the Bitsight Security Rating
Curious how Bitsight can be applied to different use cases? The Security Ratings Platform can be leveraged for multiple uses, including security performance management, third-party vendor risk management, cyber insurance, and mergers and acquisitions.
Security Performance Management
There are a few ways companies use what Bitsight does through providing security ratings for their security performance management:
- Bitsight helps users take a risk-based, outcome-driven approach to managing the performance of their organization’s cybersecurity program through broad measurement, continuous monitoring, and detailed forecasting in an effort to measurably reduce cyber risk.
- What does Bitsight do to help users benchmark against their industry peers or competitors? It’s easy to see if your security rating is more or less advanced than your industry peers using the standardized rating system Bitsight data creates. With this information, organizations can make better decisions on how to efficiently allocate resources for their security program to stay competitive within their peers.
- Users facilitate the process of reporting their security data by utilizing their Bitsight rating when presenting to their board of directors. Company executives and leadership teams are becoming increasingly concerned with cybersecurity performance, and Bitsight’s Security Ratings are a proven and effective way to communicate security performance with the board.
Third-Party Vendor Risk Management
Security ratings can be used during various life-cycle stages of a vendor relationship:
- Selection: Companies can look at security ratings to get a sense of the vendor’s cybersecurity posture before they begin engaging with them.
- Onboarding: Once a vendor has been selected, the vendor will become intertwined with the user’s first-party network. Depending on their criticality, the vendor may have access to the internal network or sensitive data. So while completing onboarding, your company must continue to monitor a vendor’s security performance.
- Ongoing: Security ratings are critical for continuous monitoring in long-term vendor relationships. Bitsight will alert you if there are any changes to the vendor’s security posture, and will help you keep an eye on your most critical, highest tiered vendors year-long instead of just during a yearly cybersecurity audit.
- Termination: If a vendor becomes a large security problem — say they’ve been breached and didn’t tell you, but you found out via the Bitsight platform — you can use ratings to help you decide if a vendor relationship needs to be terminated.
Cyber Insurance
Cyber insurance underwriters use ratings to get a sense of a company’s cyber footprint. If an insurance company is looking to underwrite a cyber insurance policy for a big bank and they see the bank has a poor rating, they’re likely to take that into consideration when writing the policy.
On the other hand, if a company is looking for cyber insurance and they have a great Bitsight Security Rating, they could shop their rating around to find the best offer. This is another way what Bitsight does is helping increase user efficiency in their business operations.
Mergers & Acquisitions
When a company acquires another company, they often assume ownership of every IP address and security process associated with the purchased company. There have been many cases where companies have either merged with or acquired another business that carries a lot of security risk.
Today, more companies are recognizing this risk — and it is now evaluated on the same stage as credit, financial, or operational risk. What Bitsight does is provide security ratings that give the purchasing company a better look at information that could alter their decision to purchase.
Read here for more in-depth information on our ratings process, methodology, and governance.


