File Sharing & Email Security Across The Globe
Tags:

Despite all the complex cybersecurity threats facing organizations around the globe, employee behavior often leads to security compromise. In a recent Experian survey, 66% of data protection and privacy training professionals say employees at their organizations are the weakest security link. Yet beyond training and educating employees, there are policies and controls organizations can implement to further reduce risk. By eliminating Illicit peer-to-peer file sharing and properly configuring email security protocols, organizations can diminish the likelihood that employees will inadvertently introduce malware into company networks.
Why are these risk vectors so important?
While file sharing is not an inherently harmful activity, it poses major security risks if employees are unaware of the origin of files that may contain malware. In a sample of 215 torrented applications and 104 torrented games and found 38.7% of games and 43.3% of applications contained malware. Moreover, Bitsight found that companies with high file sharing activity were likely to have more compromised machines due to botnet infections.
What about email security protocols? Phishing attacks are still the largest attack vector according to countless reports. Scammers that send emails under the guise of employees are able to glean incredible amounts of information, money, and data. During tax season, security researcher Brian Krebs saw an uptick in attacks where criminals posing as CEOs asked HR and Finance departments for employee W-2 forms. In all of 2015, the FBI estimates that spoofing emails costs businesses $263 million. found that companies with high file sharing activity were likely to have more compromised machines due to botnet infections.
So, how diligent are companies around the world when it comes to illicit peer-to-peer file sharing and email security protocols? Our latest Bitsight Insights report looks at how perform in these areas. Let’s take a look.
File Sharing
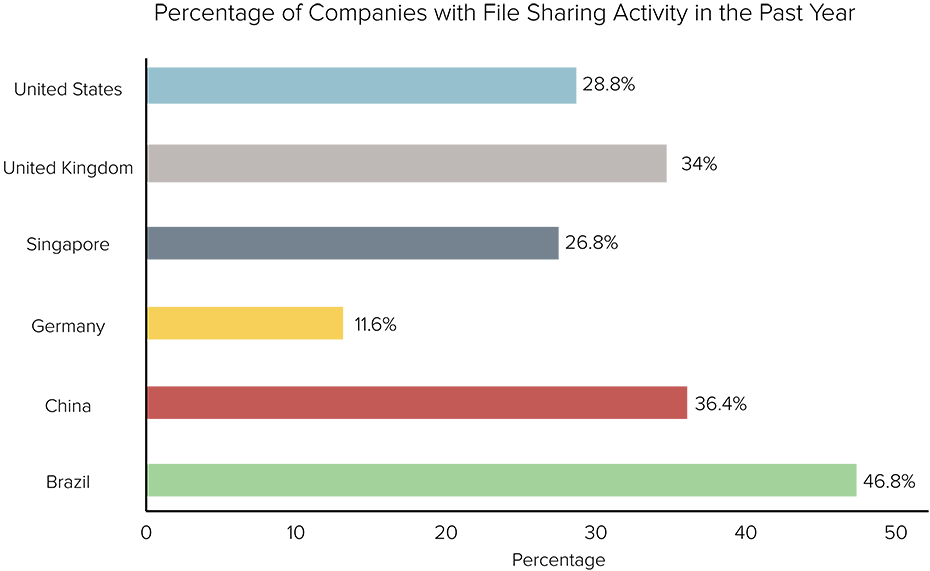
Out of all the nations studied, Brazil had by far the highest rate of harmful peer-to-peer file sharing on corporate networks. Bitsight observed a higher incidence of peer-to-peer file sharing in Brazil, as 46.8% of companies in this country experienced file sharing activity in the past year.
Conversely, German companies had a significantly low percentage of companies with observed peer-to-peer file sharing to their networks. Only 11.6% of companies showed evidence of peer-to-peer downloads. Why could there be such a stark contrast between Germany and Brazil? In Germany, strict policies exist regarding file sharing, and those caught are often subject to fines. Unsurprisingly, companies based in nations with strict copy infringement and intellectual property laws are likely to have less file sharing activity on their networks.
Email Security
Bitsight researchers looked at the utilization of two important email security protocols: Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM). Bitsight researchers specifically looked at the proportion of companies that had a Bitsight SPF or DKIM grade of C or lower.
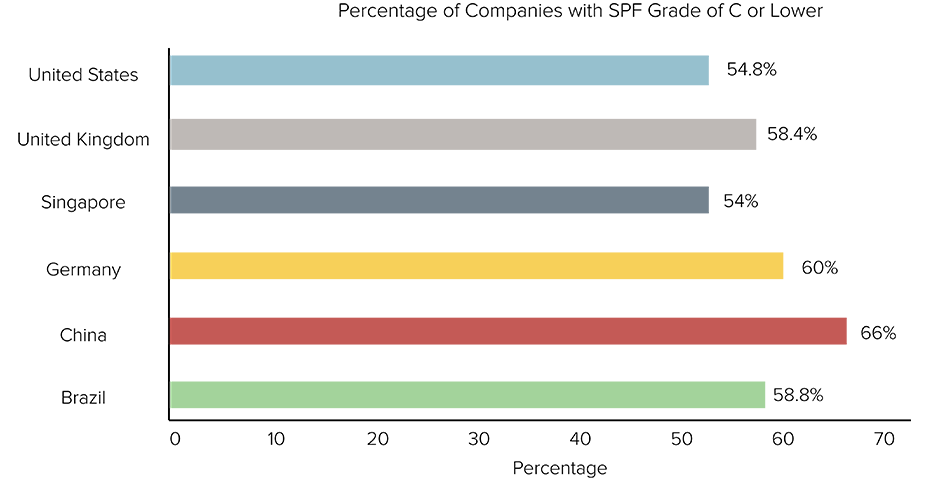
Sender Policy Framework (SPF) help to limit an attacker’s ability to successfully spoof a valid “From” address. China had the largest percentage of companies with an SPF grade of C or lower. Germany, the United Kingdom and Brazil were not too far behind.
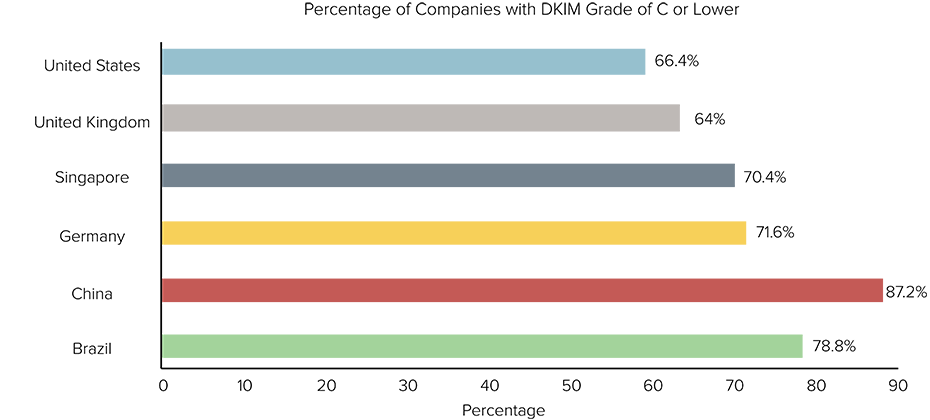
DKIM is another important email protocol that helps to authenticate valid servers and limit the sending of spoofed email messages. Bitsight found that China and Brazil had a higher percentage of companies with low grades when it comes to implementing DKIM. Germany and Singapore had 71.6% and 70.4% respectively. The US and UK had a lower percentage of companies with poor performance.


