Brexit and Cybersecurity: Anger Is an Energy
Tags:

Right now, the UK is in political turmoil, which makes any long-term cyber security predictions difficult. But it is possible to make statements about cybersecurity in the short term.
Let’s look at where we are. The country has just had a bitter, nasty, and brutal referendum campaign that focused on hot button issues like immigration and Britain’s sovereignty. The post referendum analysis shows the country was split young vs old, those with degrees vs. those without, London vs, the rest of England, and so on. Hate crimes are reportedly up significantly.
Things aren’t going to get better soon. The two major political parties have both had leadership struggles and Scotland may hold another independence referendum splitting the union apart.
So what are the cybersecurity implications of this turmoil? There’s a line from an old punk song that I think describes the resulting cyber security situation: ‘anger is an energy’.
In a highly charged atmosphere, the risk of cyber attacks can significantly increase. There’s a strong motivation to damage ‘the other side’ by defacing websites, hacking databases to breach data, or to bring sites down through DDoS attacks. The well-known ‘Anonymous’ hacker group is a good example of a group responding to events through direct action, though there are numerous other examples of politically motivated attacks.
The obvious targets are government, political parties, the media, and campaign groups, but here the list of possible targets is much wider. Many high-profile business people campaigned for one side or another, trade unions and business organisations made public statements, and even entertainers had their say. This is a huge range of potential targets to damage or embarrass.
To attack an opponent, it’s not just their websites that are targets. Digital services are increasingly outsourced and there’s a cyber supply chain with data passed from vendor to vendor. To embarrass or breach an opponent, you may just need to attack one of their key cyber supply chain vendors.
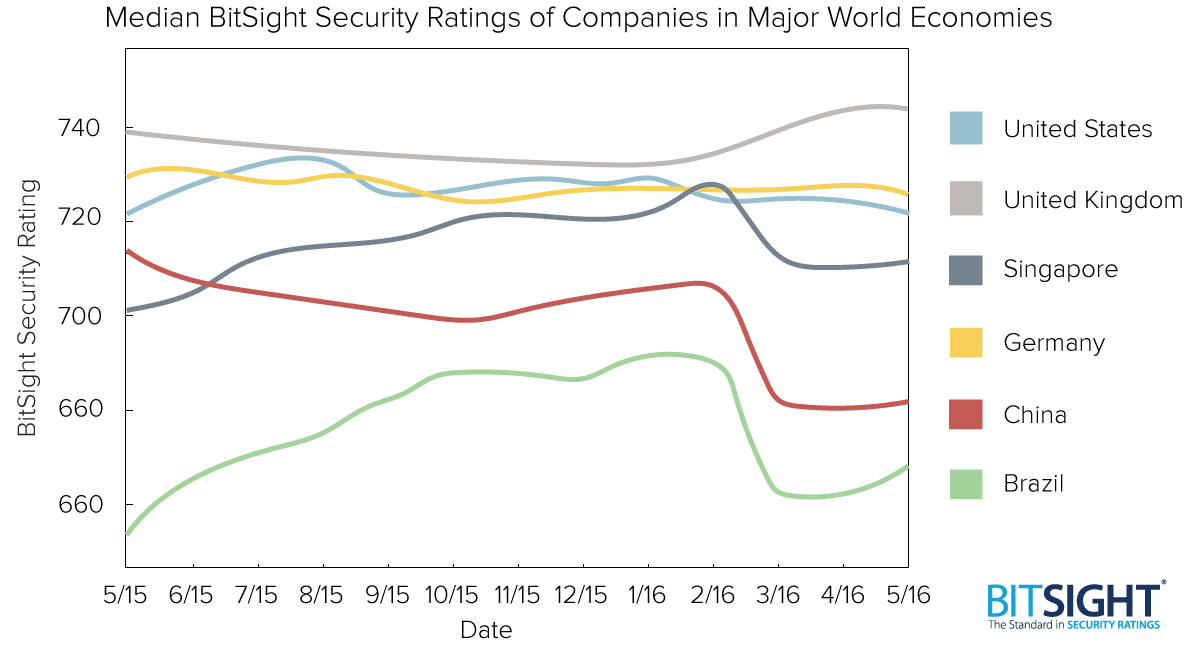
On the whole, the UK is in a good place with respect to cybersecurity. In a recent Bitsight study, we found companies with the majority of their IP addresses in the UK tended to be quite secure; the average Bitsight rating was higher for UK companies than for several other countries as I show below. But even companies with good security overall can still succumb to attacks and a weak link in the digital supply chain can expose a company’s data.
So what actions can companies take to mitigate cyber risk? The UK government has been promoting its cyber essentials programme for a while and it contains a lot of very good guidance. Here’s a list of items I suggest you address in the wake of the Brexit vote:
Conclusion
- Make sure your software is up to date - patch everything often. Installing patches is a nuisance, but a motivated attacker can take advantage of a short window where your systems are unpatched.
- Make sure you’ve changed default passwords and that you’ve prevented anonymous database access. An astonishing number of databases containing personal details are left open and unprotected. This can be a real problem for voluntary organisations (e.g. campaign groups) that lack the technical resources to configure their databases securely.
- Make sure your systems are correctly configured. This includes having appropriate SSL configurations, configuring email servers correctly (SPF, DKIM,...), and locking down unnecessarily open ports.
- Know your cyber supply chain and know who is processing your data. Who are your vendors outsourcing your data too?
- Keep an eye on your weaknesses and the weaknesses of any vendors you share data with and the vendors they share your data with. The security of your data is only as good as the weakest link in the cyber supply chain. Do you truly know how secure your vendors are? If you can’t measure it, you can’t control it, and you can’t fix it.
Of course, this list applies all the time, but while ‘anger is an energy’, the need for security against motivated and energetic attackers increases greatly.


